Image: VMware
VMware in 2012 made a $1 billion bet on the small startup Nicira that enterprise IT managers would see the value of server and storage virtualization and extend that construct to the network. VMware’s follow-on product to Nicira–the NSX network hypervisor–seems to have paid off.
NSX is best known for the ability to provide zero-trust security between virtual machines, however, VMware would like to highlight the value of moving more of the intelligence away from network hardware devices to software-based controllers. Enterprise networks are one of the last areas of IT that have not been impacted by software abstraction–until recently.
Many tech analysts believe the time of the software-defined network (SDN) has arrived. Public cloud companies such as AWS have long embraced SDN, and Cisco’s announcement of its intent-based management signals changes within the industry. This guide to VMware NSX is a brief introduction to the virtualization product.
Update: VMware announced end of life for NSX data center (NSX-V) in 2018, and as of mid-2020 is actively encouraging people to migrate to NSX-T, the newer cloud-native version of NSX that is decoupled from the hypervisor. NSX-V 6.3 has already reached end of general support, and its end of technical guidance data is February 2, 2021. NSX-V 6.4 will reach end of general support on January 16, 2022, and end of technical guidance on January 16, 2023. NSX customers should consider migrating to NSX-T as soon as possible to avoid service interruption.
Executive summary
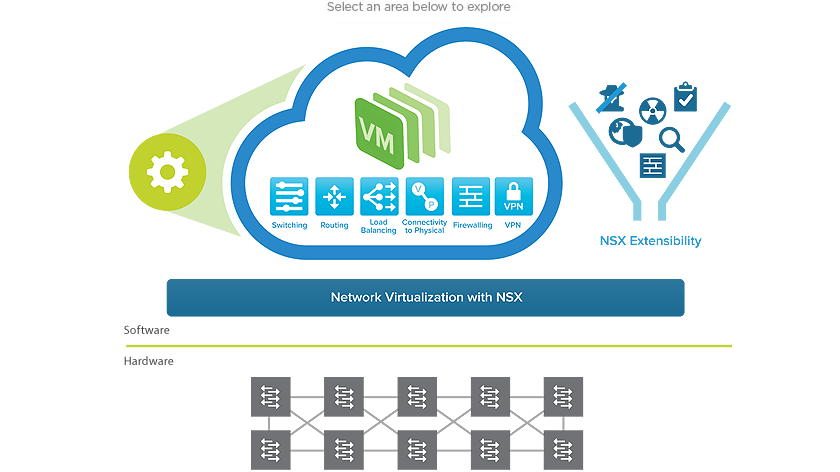
- What is VMware NSX? NSX is a network hypervisor that provides a platform to manage virtualized network deployments.
- Why does VMware NSX matter? NSX is currently the leading network virtualization platform; also, it offers an interesting micro-segmentation security use case.
- When is VMware NSX available? NSX currently ships as version 6.3.2.
- How do I use VMware NSX? NSX comes in two major flavors: one for vSphere environments and one for non-vSphere environments.
SEE: Virtualization Policy (TechRepublic Premium)
What is VMware NSX?
Martin Casado, a founder of Nicira and General Partner at Andreessen Horowitz (a16z), has referred to NSX as a network hypervisor. As a network hypervisor, NSX is an advanced network provider for virtualized environments that are powered by virtual switches. The number of virtual switch ports has long outnumbered the number of physical switch ports.
Most enterprise environments maintain a high number of virtualized workloads. The virtual machine (VM) is the primary measure of data resources–even cloud-based services best describe their environments as VMs hosted in a public data center.
NSX leverages the concept of the virtual switch to extend the capability of the virtual network. While there is a version of NSX for non-vSphere environments, the primary target is vSphere. NSX provides tight integration with VMware vCenter‘s database; the integration allows for a natural extension of vSphere constructs to the network.
SEE: Basics of VMware vSphere & ESXi Virtualization Software (TechRepublic Academy)
Network administrators gain the capability to control the network using vCenter-like policy–VMware calls this approach software-defined networking. From a computer science perspective, it’s the abstraction of network control and services from physical hardware. Functions such as routing, load balancers, intrusion protection, and security exist as services within the hypervisor; as such, network admins configure and manage the virtual network from a single NSX control panel and API.
As software, VMware can deploy NSX practically in any environment. In addition to supporting vSphere, a version of NSX exists for KVM, and VMware has shown a non-shipping version for AWS EC2 environments.
Additional resources
- Why VMware’s NSX must evolve to keep up in a serverless future (TechRepublic)
- VMworld 2016: VMware lays out its strategy for cross-cloud support (TechRepublic)
- VMware’s next play: Managing all clouds for enterprises (ZDNet)
- VMware buys Arkin Net, adds software defined networking heft (ZDNet)
- NSX – The Network Redefined (CANTECHIT)
Why does VMware NSX matter?
Agility and security first come to mind when considering NSX. The network silo within enterprise IT has long resisted abstraction. Webscale cloud providers and telecom service providers are two industries that demonstrate the value of the abstracted network.
AWS’ virtual private cloud (VPC) represents, in my opinion, the pinnacle of the abstracted network. The customer has the ability via API or control panel to deploy and manage services such as load balancers, zero trust security, and multi-zone redundant networks–even users without a great deal of knowledge about networking can configure these advanced services within hours or minutes in AWS. These services take days, months, or years to deploy within traditional data centers. Enterprises benefit greatly from the agility of the AWS VPC.
Similarly, telecom service providers have taken advantage of SDN to deploy network function virtualization (NFV), which takes what was a physical server or other dedicated hardware and virtualizes it. Think of a content distribution node (CDN). In the past, if a service provider wanted to onboard a new CDN customer, the service provider deployed a technician to provision and install the physical server. As an NFV device, the service provider provisions a new VM to service a new customer. There’s no need to deploy a technician, and the time required to onboard a new customer is reduced by weeks.
SEE: Quick glossary: Virtualization (TechRepublic Premium)
While some service providers and webscale companies utilize NSX, VMware scales network abstraction down to the enterprise level. NSX integrates into VMware’s ecosystem of products, including VMware Realize (vRA) for orchestration and automation. Organizations heavily invested in VMware gain the ability to automate network, storage, and compute via a single organization for support.
Additional resources
- Video: The most important tech underneath VMware’s new Cross-Cloud Architecture (TechRepublic)
- Global SDDC market to hit $139B by 2022, says new report (TechRepublic)
- NV, NFV, and SDN: What’s with the networking acronym explosion? (TechRepublic)
- Ebook: IT leader’s guide to the automated enterprise (TechRepublic Premium)
- SDN and the data center: Deployment plans, business drivers, and preferred vendors (TechRepublic Premium)
Who does VMware NSX affect?
NSX is a network product and therefore targets the network team; however, NSX is part of a greater strategy of a software-defined data center (SDDC). In the SDDC, all aspects of operations must be factored in. As an example, a surprising use for NSX is security.
SEE: Free ebook–Executive’s guide to the software defined data center (TechRepublic)
Due to the integration of NSX with vCenter, the NSX Firewall provides an unexpected side benefit VMware calls micro-segmentation, which is a spin on the idea of zero-trust security. Zero-trust security makes no assumption of trust between nodes based on the network broadcast domain. Using the vCenter database, security engineers gain the ability to implement security policies between two nodes on the same logical subnet. Before NSX, creating a zero-trust network was cost prohibitive.
Although, in speaking with Martin Casado when he was general manager of VMware’s Network and Security business unit, there are limits. When asked about non-virtualized nodes such as communications between two bare metal hosts, Casado answered that NSX doesn’t offer support for communication that doesn’t traverse the virtual switch hosted networks. NSX doesn’t completely replace the intelligence of the physical network, and NSX doesn’t provide support for non-virtualized workloads. Solutions from companies such as Nuage Networks and Cisco offer hardware-based solutions.
Additional resources
- Is VMware NSX more than just a security platform? (TechRepublic)
- Ebook–The cloud v. data center decision (TechRepublic)
- Network Security Policy (TechRepublic Premium)
- 6 Ways How SDN Can Enhance Data Center Security (TechRepublic download)
When was VMware NSX released?
The original version of NSX 6.0 was released in August 2013 at the US VMworld user conference. NSX currently ships as version 6.3.2.
VMware has maintained two tracks for the VMware NSX platform: NSX for vSphere and NSX-T. NSX for vSphere (which I’ve seen referenced as NSX-V in some early documentation) focuses on vSphere environments and supports Open vSwitch (OVS) and VMware’s virtual distributed switch (vDS). NSX for vSphere also offers tight integration with vCenter.
SEE: All of TechRepublic’s smart person’s guides
Nicira was a large contributor to OpenStack and therefore offered support for KVM. NSX-T aligns historically with the original Nicira product and offers support for KVM via OVS. The primary difference between NSX for vSphere and NSX-T is the vCenter integration–NSX-T doesn’t have the tight vCenter integration of NSX for vSphere.
Existing KVM customers or customers looking to migrate to KVM have the option of deploying NSX-T in their current vSphere environment. NSX-T offers support for both OVS and vDS in vSphere environments, making a potential shift to KVM without disrupting network operations possible.
Additional resources
- Product offerings for VMware NSX for vSphere 6.2.x and 6.3.x (VMware)
- How VMware paved the way for the rise of SDDC (ZDNet)
- VMware vSphere: The smart person’s guide (TechRepublic)
- Cisco supports VMware NSX, though customers want integration (TechRepublic)
Who are VMware NSX competitors?
Cisco recently announced an intelligent network platform that provides a competitive vision to NSX. In addition to the unreleased Cisco solution, VMware also competes against Nuage Networks and Juniper. I spoke with the Big Switch Networks product team; while the product team doesn’t view VMware as a competitor, Big Switch has overlapping features to NSX.
Additional resources
- Video: Cisco is reinventing networking with a new intuitive system (TechRepublic)
- Cisco: Network intuitive puts us several years ahead of the competition (ZDNet)
- Do your SDN homework: Read about solutions from Cisco, Brocade, Juniper, Arista (TechRepublic)
- Google shares details about Espresso, its peering edge architecture (ZDNet)
How do I use VMware NSX?
Whether your goal is micro-segmentation, automation, or simplified operations, NSX offers a new perspective to virtualized networking. VMware has made a bold bet on NSX and the ability of traditional network teams working side by side with virtualization and security operations. As shown by webscale providers and telecom customers, the potential is great for improved capability and operations.
Additional resources
- Getting started on NSX (VMware)
- VMware NSX: 3 different use cases (TechRepublic)
- 10 things you should know about deploying a software defined network (TechRepublic)
- Ebook: How to automate the enterprise (TechRepublic)
- Is it time for virtual switch abstraction to fade? (TheCTOAdvisor)
Editor’s note: This article was written by Keith Townsend. The update was written by Brandon Vigliarolo.

