Malicious software continues to rise and it’s IT’s job to prevent such code from finding its way to end-user systems. But because it’s your job to serve as the front line assembly of defense, it doesn’t mean you can’t empower your users (and their tools) to give you a hand. Chances are your company already employs the means to prevent malware. However, no one solution is infallible. So when Google decided to roll out a built-in anti-malware tool (a tool that was actually announced way back in 2017), it meant those users who work with the Chrome browser enjoyed an added layer of defense.
The one caveat to this particular anti-malware software is that it’s not an all-purpose tool. It’s not going to scan your system for any and all threats. Instead, it will scan for known threats to the Chrome browser. That’s not a bad thing, as many malware threats are picked up from using a browser.
What Google has done is roll in its own malware scanner, one that runs in the background (so long as Chrome is open) and can also be run manually. As you might expect, this tool can only be found in the Windows version of Chrome, so Linux and macOS users need not apply. I want to show you how to use this added level of defense against malware on Windows.
What you’ll need
Obviously, you’ll need a Windows machine, running an updated version of Chrome. The version of Chrome I am testing is 67.0.3396.79. To check your version, open Chrome, click on the Menu button, and select About Chrome. If you’re running an older version, update immediately.
Usage
Using the built-in malware scanner is quite simple. Open up Chrome and then enter chrome://settings/cleanup in the address bar. Hit enter and the tool will appear (Figure A).
Figure A
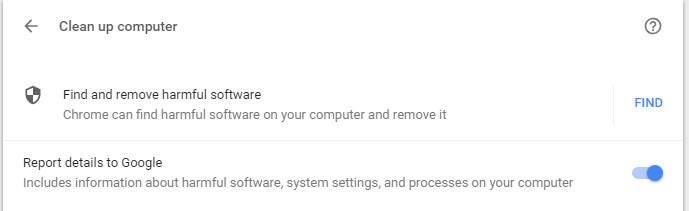
Click on the FIND button and the scanner will run. If you don’t click on the FIND button, eventually the scanner will run of its own accord. The scanner will do its thing and eventually report back (hopefully) that your system is clean.
What does the scanner look for? According to the official Google Blog, the developers worked with ESET to combine the Chrome sandbox technology with ESET’s detection engine to create a system that will remove software that doesn’t comply with Google’s unwanted software policy.
Although the scanner does run automatically (it’s not, however, real-time), should you download a file or suspect something is going on, run the scanner manually.
SEE: Google Cloud Platform: An insider’s guide (free PDF) (TechRepublic)
Results
I have yet to actually see the scanner pick up any malicious software. I attempted to intentionally infect a Windows 10 VM with a known malware test file (eicar.zip) but Chrome didn’t pick it up. My guess is that, because the eicar test file doesn’t directly affect Chrome, it wasn’t picked up. I do know, however, that should the Chrome scanner pick up malware, it will first send information to Google (which you can opt out of) and then pop up a warning, asking if you want the threat removed. Even if the Chrome scanner shunned the eicar test file, it’s nice to know Google recognizes the severity of threat that malware poses against end users. And that they’ve created this tool, such that users don’t have to interact, is a bonus to IT admins scrambling to keep their users virus- and malware-free.
