As more people are working remotely due to the coronavirus, cloud services have seen a surge in demand. But as this trend has unfolded, cybercriminals have found a ripe target to exploit. A blog post published Wednesday by security provider Abnormal Security describes how phishing attacks are taking advantage of Amazon Web Services to steal user credentials.
In this new phishing campaign, the attackers deploy an email that contains an automated notification allegedly from Amazon Web Services (AWS). The anchor text used in the body of the email looks like legitimate AWS links. However, the URL used as the anchor text is different from the actual URL in the hyperlink. By disguising the URL this way, the attackers hope to convince the recipients that the site they’re accessing is the real AWS page.
SEE: Fighting social media phishing attacks: 10 tips (free PDF) (TechRepublic)
Instead, the attached hyperlink redirects the user to a webpage that looks identical to the AWS login page, complete with official Amazon images and the right layout. Of course, unsuspecting users who sign in will see their Amazon login credentials stolen and their sensitive AWS data compromised.
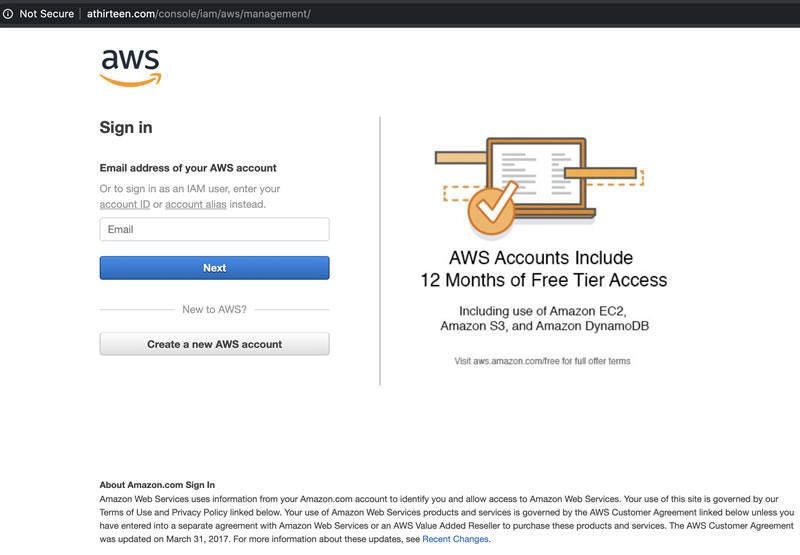
Image: Abnormal Security
Abnormal Security said that it has witnessed several versions of this attack across different clients, from different sender addresses, and using different payload links. But all the payload links take the user to AWS credential phishing websites. Each of the phishing emails discovered have come from the same IP address hosted by a French VPN.
“Employee credentials that can get to their cloud accounts are an easy way to get to the prized possessions of an organization,” said CloudKnox Security CEO Balaji Parimi. “In every company’s cloud accounts, there are thousands of identities with the potential to be exploited, and most of them are not even aware of the level of permissions all these identities have. It’s a simple numbers game—the more identities that can perform risky operations and access keys to the kingdom, the easier it is for the bad guys. It’s time to prioritize these ticking time bombs and proactively manage identity permissions to mitigate the humongous risk exposure.”

Image: Getty Images/iStockphoto