While tracking the mobile banking malware FluBot, the F5 Labs researchers discovered the new Malibot threat targeting Android phones. Malibot has a number of features and capabilities that make it an important threat to consider.
SEE: Mobile device security policy (TechRepublic Premium)
How is Malibot distributed?
Malibot is currently being distributed by cybercriminals via two different channels.
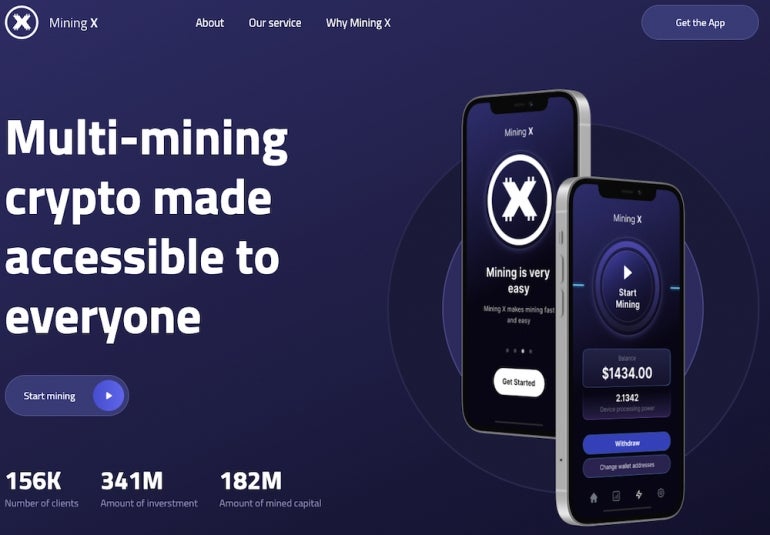
The first distribution method is through the web: Two different websites have been created by the fraudsters, named “Mining X” and “TheCryptoApp” (Figure A and Figure B).
Figure A
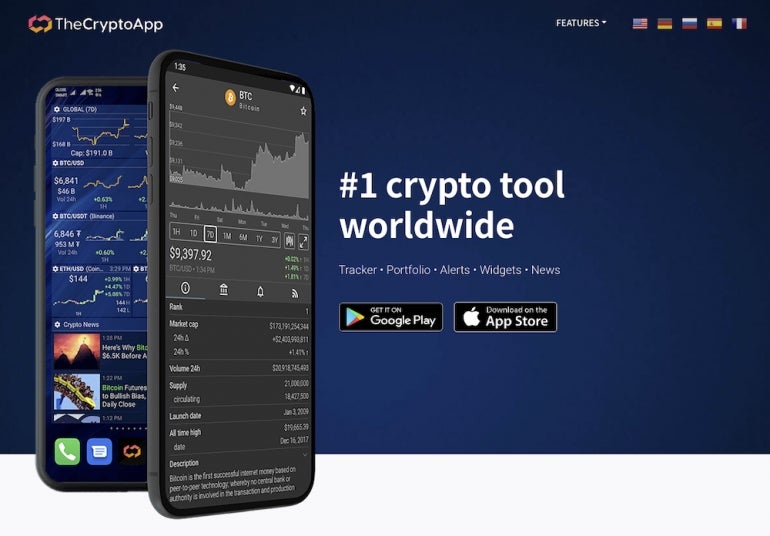
Figure B
TheCryptoApp campaign impersonates a legitimate cryptocurrency tracker application. The user will only be infected and provided with the malware link if browsing from an Android phone. Browsing from any other device will result in the user being provided with a legitimate link for the real TheCryptoApp application on the Google Play Store. A direct download link is provided to the Android users outside of the Google Play Store.
As for the Mining X distribution campaign, clicking on the download link from the website leads to the opening of a window containing a QR code to download the application.
The second distribution channel is via smishing, directly hitting Android phones: Malibot has the ability to send SMS messages on-demand, and once it receives such a command it sends texts on a phone list provided by the Malibot command and control server.
What data does Malibot steal?
Malibot is designed to steal information such as personal data, credentials and financial knowledge. To achieve this goal, it is able to steal cookies, multi-factor authentication credentials and crypto wallets.
Google accounts
Malibot has a mechanism to collect Google account credentials. When the victim opens a Google application, the malware opens a WebView to a Google sign-in page, forcing the user to sign in and not allowing the user to click any back button.
In addition to collecting the Google account credentials, Malibot is also able to bypass Google’s 2FA. When the user tries to connect to their Google account, they are shown a Google prompt screen that the malware immediately validates. The 2FA code is sent to the attacker instead of the legitimate user, then is retrieved by the malware to validate the authentication.
Multiple injects for selected online services
The infected device application list is also provided by the malware to the attacker, which helps the attacker know what application can be hooked by the malware to show an inject instead. An inject is a page shown to the user that perfectly impersonates a legitimate one (Figure C).
Figure C
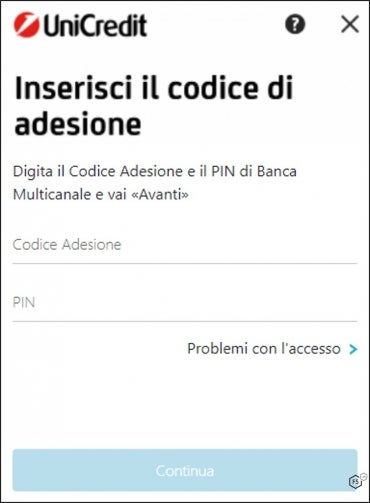
According to F5 Labs, the Malibot injects target financial institutions in Spain and Italy.
Multi-factor authentication
In addition to the method used to steal Google accounts, Malibot can also steal multi-factor authentication codes from Google Authenticator on-demand. MFA codes sent by SMS to the mobile phone are intercepted by the malware and exfiltrated.
Crypto wallets
Malibot is able to steal data from Binance and Trust cryptocurrency wallets.
The malware tries to get the total balance from the victims wallets for both Binance and Trust and export it to the C2 server.
As for the Trust wallet, Malibot can also collect the seed phrases for the victim, which allows the attacker to later transfer all the money to another wallet of their choice.
SMS fraud
Malibot can send SMS messages on-demand. While it mostly uses this capability to spread through smishing, it can also send Premium SMS which bills the victim’s mobile credits, if enabled.
How does Malibot obtain control over the infected device?
Malibot makes heavy use of the Android’s accessibility API, which allows mobile applications to perform actions on behalf of the user. Using this, the malicious software can steal information and maintain persistence. More specifically, it protects itself against uninstallation and permissions removal by looking at specific text or labels on the screen and pressing the back button to prevent the action.
Malibot: A very active threat
Malibot developers want it to stay undetected and maintain persistence as long as possible on infected devices. To avoid being killed or paused by the operating system in case of inactivity, the malware is set as a launcher. Every time its activity is checked, it starts or wakes up the service.
A few additional protections are contained in the malware, but not used. F5 researchers found a function to detect if the malware runs in a simulated environment. Another unused function sets the malware as a hidden application.
Mmore Malibot targets to come, U.S. may already be hit
While the F5 Labs research revealed targets in Spain and Italy, they also found ongoing activity that might hint at the cybercriminals targeting American citizens.
One domain used by the same threat actor impersonates American tax services and leads to a “Trust NFT” website (Figure D) offering to download the malware.
Figure D
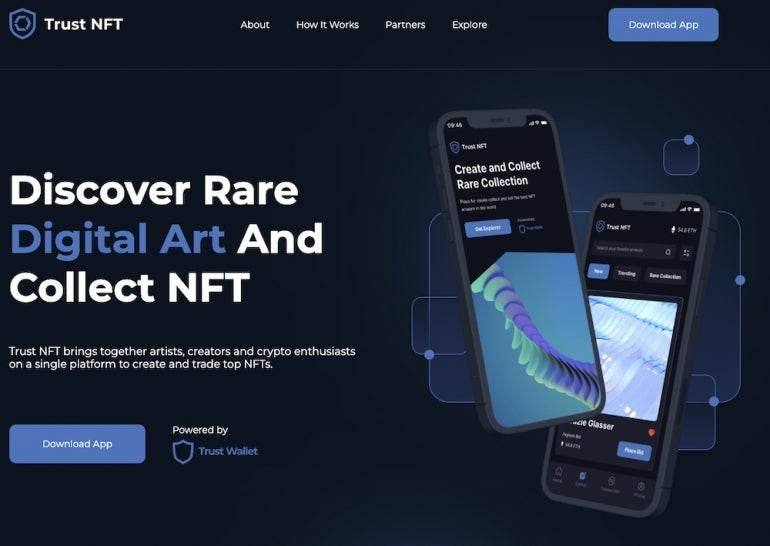
Another website using the COVID-19 theme in its domain name leads to the same content. Researchers expect the attackers to deploy more malware via these new websites in other parts of the world, including the U.S.
How to protect yourself from Malibot
The malware is distributed only from websites built by the cybercriminals and SMS. It is not currently spread through any legitimate Android platform such as the Google Play Store.
Never install any application on an Android device that is directly downloadable from a click. Users should only install applications from trusted and legitimate application stores and platforms. Users should never install applications from a link they receive by SMS.
Install comprehensive security applications on the Android device to protect it from known threats.
When installing an application, permissions should be carefully checked. Malibot malware for SMS sending permissions when being launched the first time, which should raise suspicion.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.