
The last thing upper management wants this time of the year is to receive an anonymous email or fax demanding the company pay an exorbitant amount of money within the next 24 hours, or the company’s website and business portal will be knocked offline. Then for good measure the bad guys offer a taste of what to expect — a short but attention-grabbing Distributed Denial of Service (DDoS) attack.
The threat should not be treated lightly, and Akamai’s State of the Internet / Security Q2 2015 report explains why: “The second quarter of 2015 set a record for the number of DDoS attacks recorded… more than double what was reported in Q2 2014.”
Mitigating DDoS attacks by using a CBSP
Erring on the side of caution, many businesses contract with a Cloud Based Security Provider (CBSP) that offer security services such as DDoS mitigation. One popular method used by CBSPs to squelch DDoS attacks diverts internet traffic destined for the client’s network through the CBSP’s security infrastructure.
The rerouting of traffic to the CBSP involves either the client purchasing dedicated hardware programmed to send traffic to the CBSP, or changing how the client’s domain name is routed so all traffic is sent to the CBSP.
At the CBSP, the client’s traffic passes through a scrubbing center. If the traffic is legitimate, it will be forwarded to the client’s web servers for processing; if not, the traffic will be silently discarded.
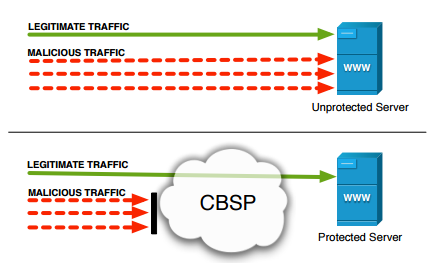
Methods of routing redirection
As to how routing redirection takes place, there are two methods: BGP rerouting and DNS rerouting.
- BGP rerouting: This is possible when the client manages an entire /24 IP block. The client can withdraw the BGP announcements for that block from the company routers. Then, the CBSP will begin BGP announcements for that same range. That will send all traffic to the CBSP.
- DNS rerouting: The client configures the company website domain name to resolve to an IP address belonging to the CBSP.
An underlying problem with DNS rerouting
Unfortunately, DNS rerouting, which is by far the most popular choice, does not eliminate the possibility of DDoS attacks, according to the research team of Thomas Vissers, Tom Van Goethem, and Wouter Joosen of KU Leuven, and Nick Nikiforakis of Stony Brook University. In their paper Maneuvering Around Clouds: Bypassing Cloud-based Security Providers (PDF), the team writes, “This rerouting mechanism can be completely circumvented by directly attacking the website’s hosting IP address. Therefore, it is crucial for the security and availability of these websites that their real IP address remains hidden from potential attackers.”
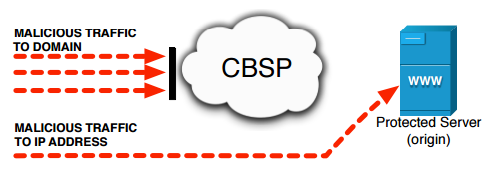
CloudPiercer scanning tool
To find out the depth of the problem, the researchers developed CloudPiercer, an automated tool that determines whether websites are vulnerable by scanning for website IP address information using the following “origin-exposing vectors.”
- IP history databases: A website’s origin might be exposed in databases that hold historical DNS data about the website. CloudPiercer will query these databases to find out which IP addresses are listed for the website’s domain.
- Sub-domains: In order not to break some protocols, several websites configure sub-domains that resolve directly to the origin (e.g., ftp.example.com). CloudPiercer will scan the domain for the existence of sub-domains to determine if such a leak exists.
- DNS records: Domains might reveal their web server’s IP address through MX, SPF, and other DNS records. During the scan, the domain’s DNS records will be queried and checked.
- Sensitive files: Administrators often forget to restrict access to development or log files that expose sensitive information. The tool attempts to access PHP information files residing on the web server.
- Ping Backs: Verification mechanisms can be leveraged to trigger an outbound connection from the website, revealing its origin to the recipient. CloudPiercer searches for Ping Back endpoints and attempts to trigger a connection to its server.
Thomas Vissers, one of the paper’s authors and PhD student at KU Leuven, emailed about a new feature, “CloudPiercer has been updated to include scanning for SSL certificates.”
To test their scanning tool, the research team assembled a list of clients who use CBSPs, have the appropriate DNS configurations, and belong to Alexa’s top 1 million websites. “We used CloudPiercer to evaluate 17,877 long-term, CBSP-protected domains against origin exposure,” note the authors.
The results
The team cautions it is not straightforward to distinguish Content-Delivery Network-only clients from CBSP clients with DDoS mitigation included. “We selected five well-known providers that have a specific focus on security… CloudFlare, Incapsula, DOSarrest, Prolexic (PLXedge), and Sucuri (Cloud Proxy),” write the authors. “We gathered a list of clients from each provider, enabling us to study their necessary configurations and their adoption by popular websites.” (Note: The authors dutifully notified all five CBSPs before their paper’s publication.)
As to what the research team found: “Our results show the problem is severe: 71.5 percent of the 17,877 CBSP-protected websites that we tested, expose their real IP address through at least one of the evaluated vectors.”
An unforeseen benefit of CloudPiercer
During their research, the team realized CloudPiercer can be used by law enforcement agencies. “Miscreants use CBSPs to hide their real hosting location, making it harder to track and shut them down,” the team suggests. “Consequently, the discussed vectors and their reported effectiveness can be leveraged by the appropriate institutions to react quicker against malicious online activities.”
Countermeasures
The research team admits that hiding website IP addresses is difficult. “However, a tool similar to CloudPiercer could be deployed by CBSPs to scan their client’s domains for exposed origins (IP addresses), creating awareness and helping administrators fix specific vulnerabilities,” the paper adds.
Another suggestion offered by the foursome is adjusting the perimeter firewall to block all connections except those originating from the CBSP. Doing this makes life a great deal more difficult for the bad guys. “Together with requesting a new IP address, this firewall configuration should be standard practice when cloud-based security is utilized,” conclude the researchers. “We can safely assume that the vast majority of customers are currently not adopting such a strategy, since, if they did, our origin (IP address) verification would have failed.”
CloudPiercer is now available for administrators using CBSP services to test their website’s exposure (owner verification is required).