
Ukraine is suffering from a wide range of cyberattacks. One of the most interesting ones is a previously unknown malware with destructive payload that has popped up on hundreds of Ukrainian machines lately.
On Feb. 23, a tweet from ESET Research claims they discovered a new malware that wipes data, used in Ukraine. The timeline follows the DDoS attacks aimed at several important Ukrainian websites (Figure A). The research was quickly confirmed by Symantec, a division of Broadcom Software.
Figure A
A complex timeline of cyber events targeting Ukraine
Prior to the DDoS operations and the discovery of this new wiper, another attack struck Ukraine in the middle of January, dubbed WhisperGate, exposed by Microsoft on Jan. 15.
Microsoft reported that WhisperGate had been dropped on victim systems (multiple government, non-profit and information technology organizations) in Ukraine on Jan. 13. The malware has been designed to look like a ransomware, but it actually had no ransom recovery code in the binary file. It has been developed to be destructive and render its targets unusable.
SEE: Password breach: Why pop culture and passwords don’t mix (free PDF) (TechRepublic)
In parallel to this first wiper operation, a series of website attacks happened in the night between Jan. 13 and 14, as reported by the CERT-UA, the official government team for responding to computer incidents in Ukraine.
Several Ukrainian websites were defaced to show a message written in Ukrainian, Russian and Polish languages (Figure B). WhisperGate was also dropped and used on those websites. According to the Ukrainian State Service for Special Communication and Information Protection, on Jan. 13-14, 2022, nearly 70 Ukrainian websites (domestic and international) were attacked.
Figure B

The message roughly translated to English, is:
“Ukrainian! All your personal data has been sent to a public network. All data on your computer is destroyed and cannot be recovered. All information about you stab public, fairy tale and wait for the worst. It is for you for your past, the future and the future. For Volhynia, OUN UPA, Galicia, Poland and historical areas.”
The message shown on the defaced websites was an image. Images, unlike text, have metadata, sometimes including physical coordinates. In this case, the image had a specific latitude and longitude: a parking lot of the Warsaw School of Economics in Poland. The choice of using an image rather than text was probably done to send a false flag, such as that GPS position.
Serhiy Demedyuk, the deputy secretary of the national security and defense council of Ukraine, blamed the attack on a group dubbed UNC1151. He added that UNC1151 is a cyber-espionage group affiliated with the special services of the Republic of Belarus.
On Feb. 15, new DDoS attacks started against the Ukrainian Ministry of Defense in addition to other targets.
The next event in this massive series of events was the appearance of the HermeticWiper malware.
HermeticWiper: A very efficient, destructive malware
Feb. 23 saw the appearance of reports about HermeticWiper, as ESET started a Twitter thread about it.
Technical analysis quickly followed. HermeticWiper is a piece of malware whose purpose is to render Windows devices unusable by wiping parts of it (Figure C).
Figure C
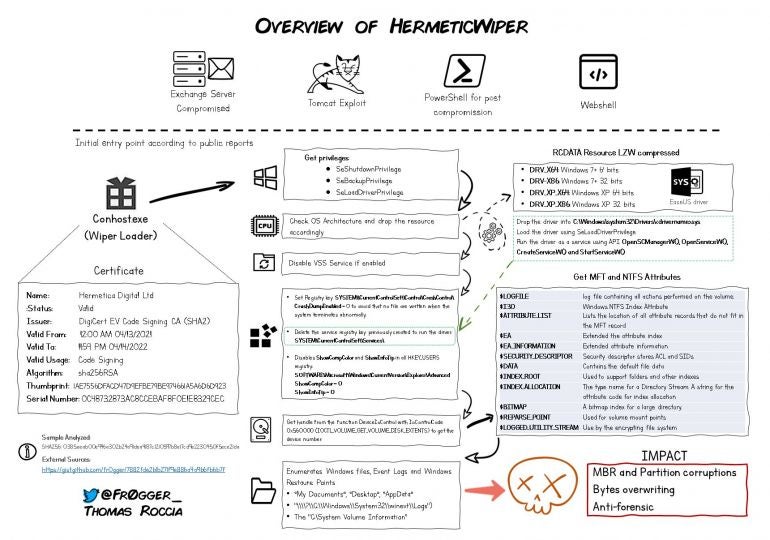
One particularly interesting characteristic of this wiper is that it is a very well-written malware with very few standard functions, unlike most of the other malware spread around.
The method it uses for wiping data has been used in the past by a few threat actors with the infamous wipers Shamoon and Destover: It abuses a legitimate Windows partition manager driver to perform its writing operations. In the case of HermeticWiper, an EaseUS partition manager (empntdrv.sys) was abused.
The malware contains several different versions of the driver and uses the appropriate one depending on the operating system version and architecture it runs on. These different driver versions are compressed as ms-compressed resources within the malware binary. Since the malware is only 114KB, this driver data takes more than 70% of it.
One of the first actions done by HermeticWiper consists of disabling the volume shadow copy, a system that can help administrators to restore a crashed system.
HermeticWiper then corrupts the Master Boot Record (MBR) of the device, and wipes files in different strategic folders of the Windows operating system:
- C:\Documents and Settings\
- C:\System Volume Information\
- C:\Windows\SYSVOL\
- C:\Windows\System32\winevt\Logs
The last destructive action consists of determining if the hard drive’s partition file system is FAT or NTFS and corrupts the partition accordingly. Once done, the system is forced to shut down and will never be able to boot again.
By doing this, the malware ensures the system is totally unusable.
So far, HermeticWiper has only been spread and used in Ukraine. On a sidenote, the name of this malware comes from the fact that it uses a signed certificate from company name Hermetica Digital Ltd and was valid as of April 2021. According to SentinelOne’s research on HermeticWiper, “it’s possible that the attackers used a shell company or appropriated a defunct company to issue this digital certificate.”
How to stay safe from HermeticWiper?
Usage of HermeticWiper outside of Ukraine is not expected. Indicators of compromise (IOC) have been shared together with YARA rules to help detect the malware on systems.
Unlike other malware whose actions are generally controlled by a threat actor via network communications, HermeticWiper does not need any. Therefore, there is no network pattern to analyze for detecting the malware, except if it is downloaded from a network, in which case it might be useful to deploy deep packet inspection (DPI) to detect the binary. Endpoints should be scanned for these IOCs.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.


