
Web browsers use Secure Sockets Layer (SSL) to encrypt traffic between client systems and server computers to protect confidential data such as social security information and credit card details. For an SSL certificate to work properly, the entity that issued the certificate (also known as a certificate authority) must also be trusted by the web browser, which involves installing the issuer certificate so the browser knows that issuer is valid and reliable.
Commonly used certificate authorities, such as Verisign, DigiCert, and Entrust, are automatically trusted by most browsers. However, if you use an untrusted internal certificate authority to generate SSL certificates for internal resources, you will be nagged by your browser when you attempt to connect.
The Chrome web browser will show something similar to Figure A.
Figure A
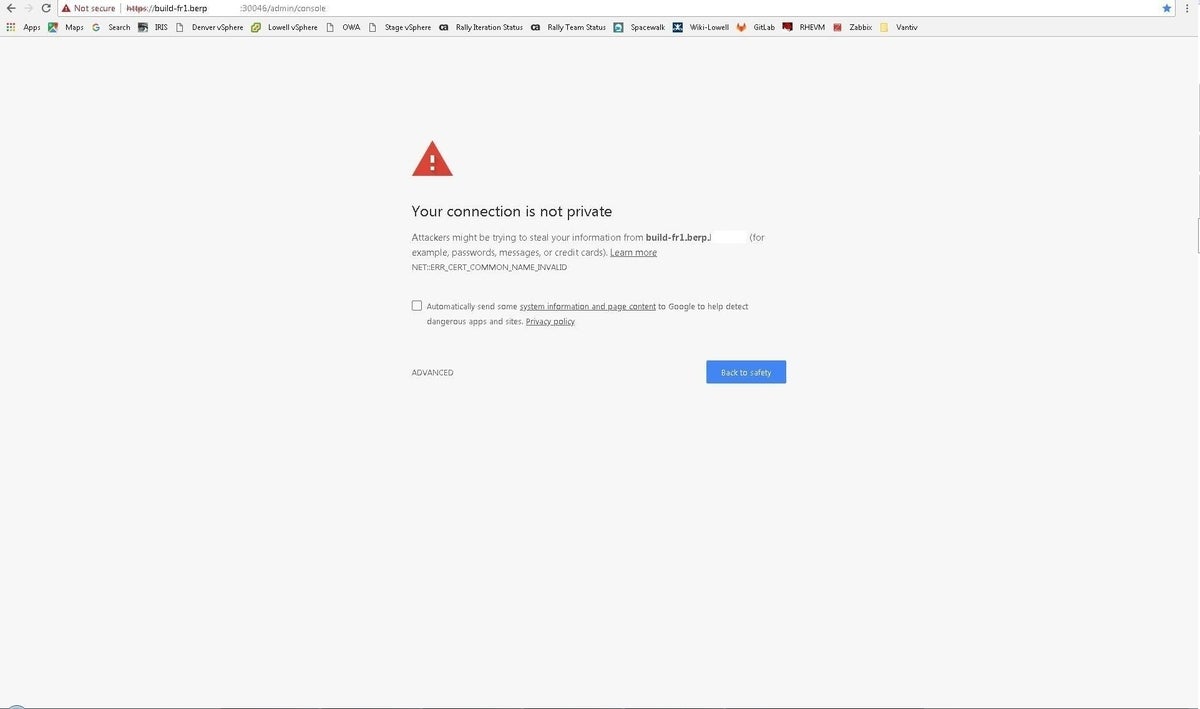
This necessitates clicking Advanced (Figure B). Then you must click Proceed To [host name] to continue.
Figure B
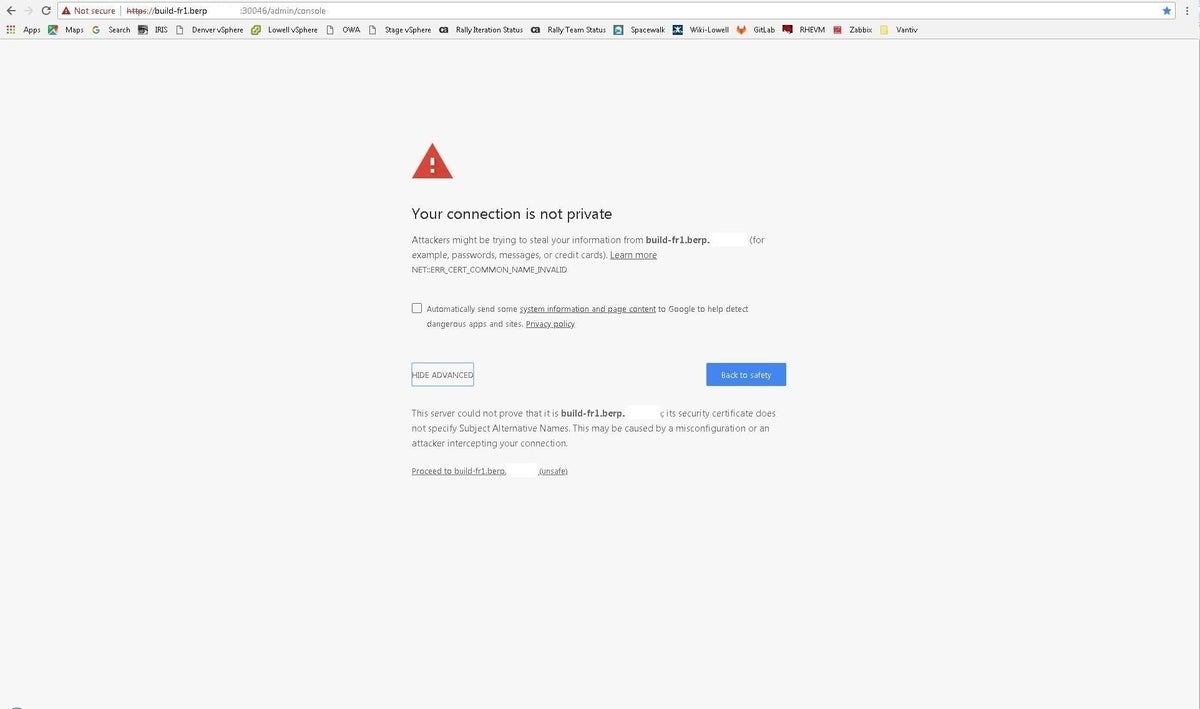
The Firefox browser will display content resembling Figure C. Click Advanced, then Add Exception (Figure D). Clicking Confirm Security Exception will permit the access.
Figure C
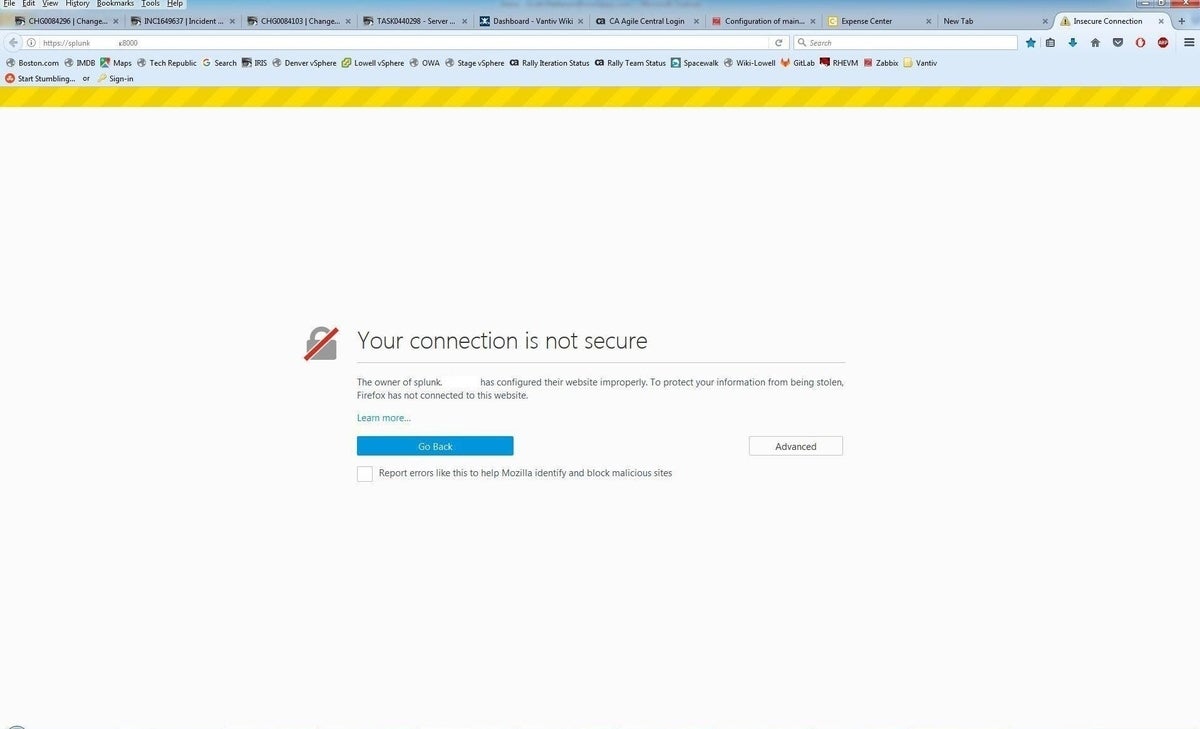
Figure D
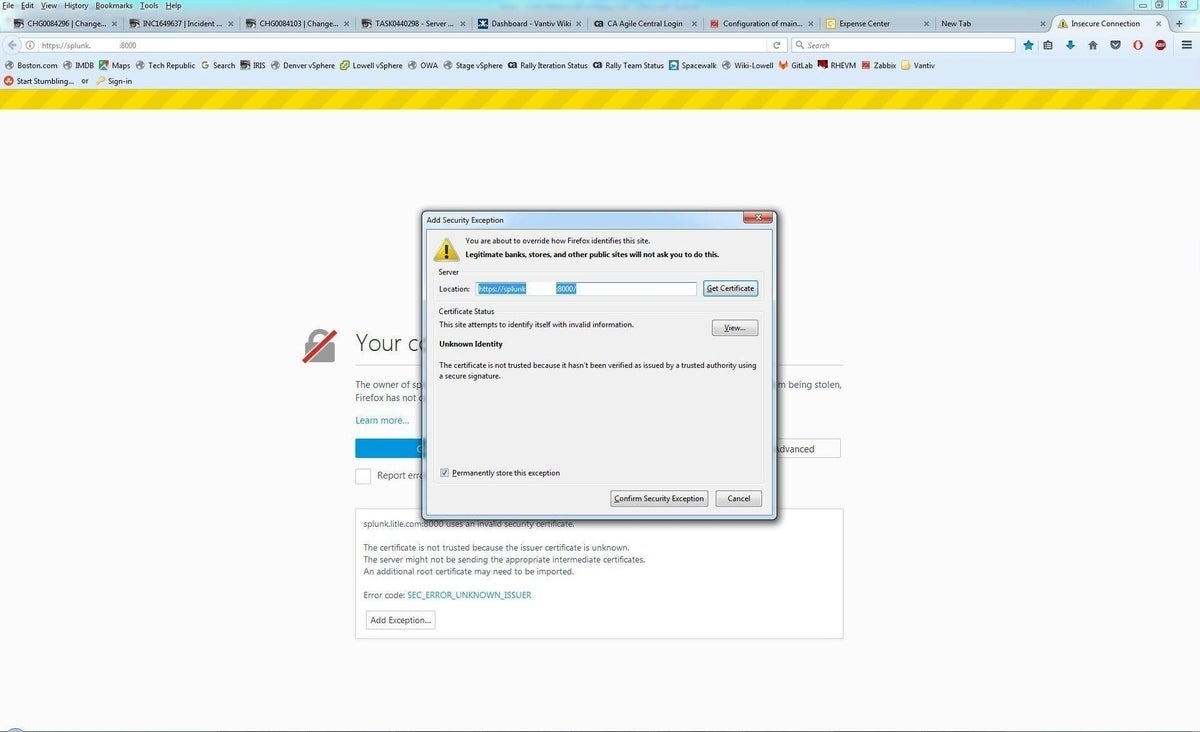
However, while these tips for both browsers will let you get to the site, you’ll have to do this for EVERY site for which your internal CA issued an SSL certificate.
Fortunately, there’s a better way. You can configure your system(s) to trust all certificates from a certificate authority by installing that system’s SSL certificate as a trusted root certificate authority. That way, Chrome and Firefox will never prompt you again about accessing any site with a certificate from that CA.
Note: This article focuses on these two third-party browsers; a future article will cover Internet Explorer/Microsoft Edge. Steps listed here are accurate at the time of this writing, but future versions of these browsers may involve different menu options.
SEE: Hiring kit: IT audit director (Tech Pro Research)
Obtain your CA certificate
First, you need to get a copy of that SSL certificate from your CA in DER format. If your CA runs Windows, follow the steps below. (If not, you’ll need to research the details for your particular operating system.)
Go to Control Panel and open the Administrative Tools folder.
Double-click Certification Authority (Figure E).
Figure E
Right-click the server and choose Properties (Figure F).
Figure F
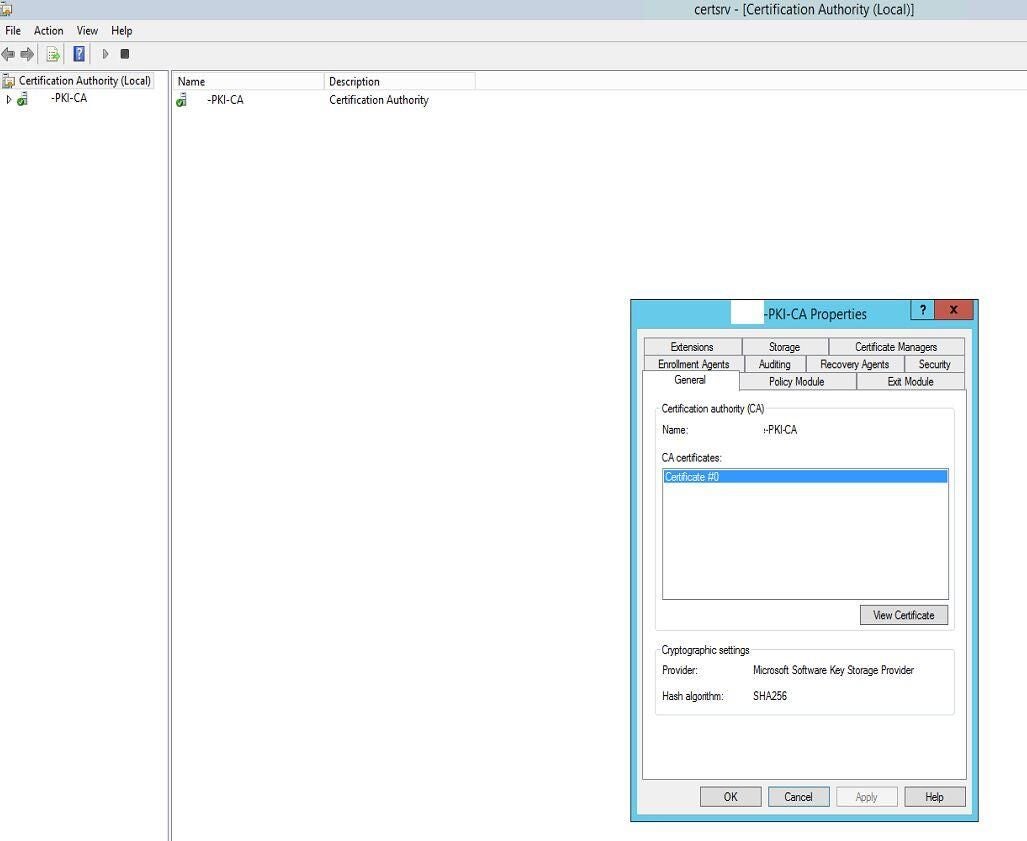
Click View Certificate (Figure G).
Figure G
Click the Details tab (Figure H).
Figure H
Click Copy To File, then click Next (Figure I).
Figure I
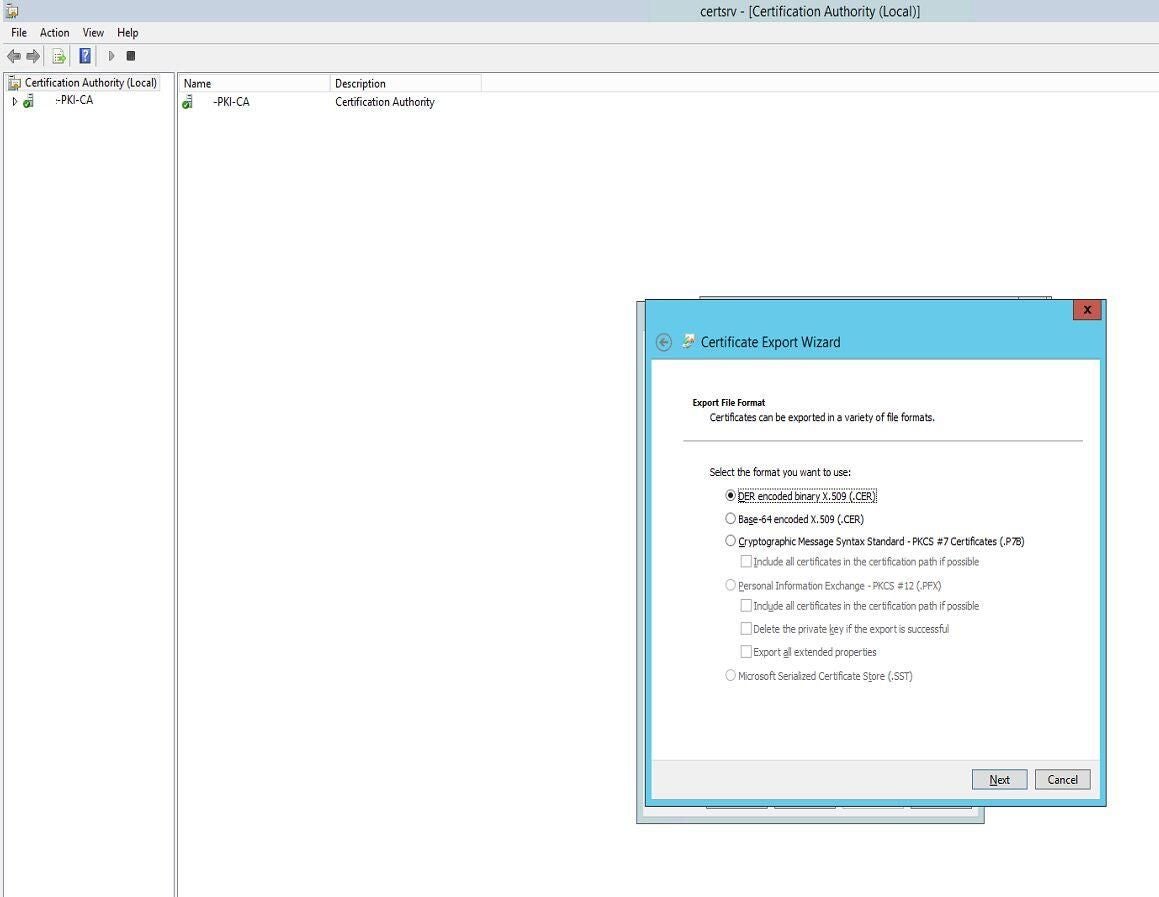
Leave DER Encoded Binary X.509 (.CER) checked and click Next.
Specify the filename (c:\CA_certificate.cer, for instance) and click Next, then click Finish.
The certificate will be saved to the location you specified.
Adding the CA certificates as a trusted root authority to Chrome
If you’re using Active Directory, your best best is to use Group Policy so all systems in your organization will trust certificates from the CA. Chrome will trust the certificate if deployed in this manner.
Utilizing Group Policy to configure Windows systems to trust your CA
Copy the certificate to your domain controller.
Go to the Control Panel and open Administrative Tools.
Open Group Policy Management (Figure J).
Figure J
Right-click your domain and choose Create A GPO In This Domain And Link It Here.
Provide a name for the Group Policy Object, such as CA Certificate, and click OK (Figure K).
Figure K
Right-click the new GPO and click Edit.
Expand Policies.
Expand Windows Settings.
Expand Security Settings.
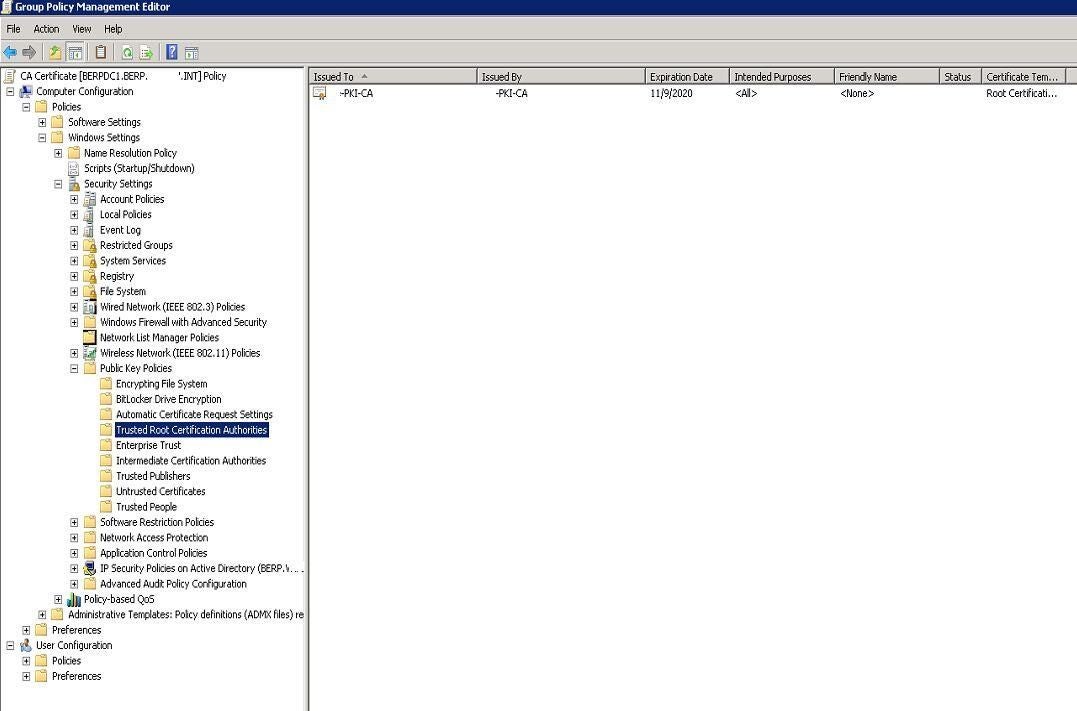
Expand Public Key Policies (Figure L).
Figure L
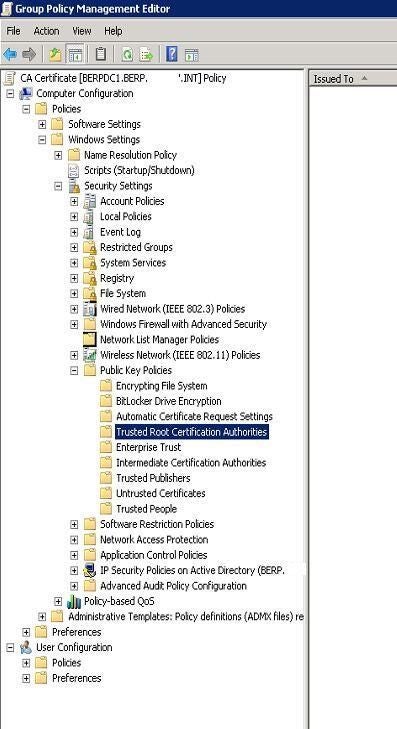
Right-click Trusted Root Certification Authorities and choose Import.
Click Next.
Click Browse, then browse to and select the CA certificate you copied to this computer.
Click Next, click Finish, then click OK.
You should now see the certificate shown in the right-hand field (Figure M).
Figure M
If you’re not running Active Directory in your organization, you can’t leverage Group Policy, but you can manually add the CA certificate on a host to trust the related SSL certificates.
Note that you can add the certificate in Chrome, but it’s advisable to add it in Windows itself, since that will cover other apps that might connect to the website.
SEE: IT pro’s guide to effective patch management (free TechRepublic PDF)
Manually configuring a Windows system to trust your CA
First, copy your CA certificate to the host machine you want to work on.
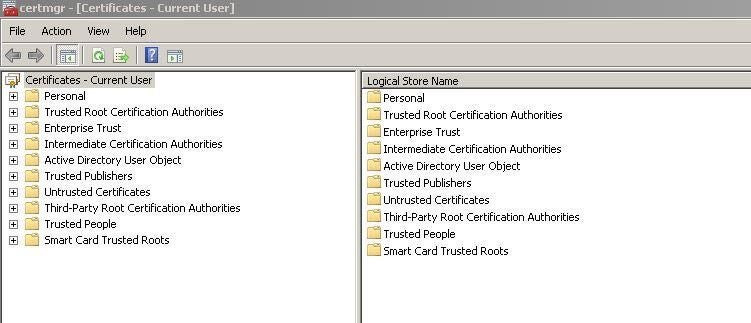
Open a Command Prompt and run Certificate Manager with the following command (Figure N):
certmgr.msc
Figure N
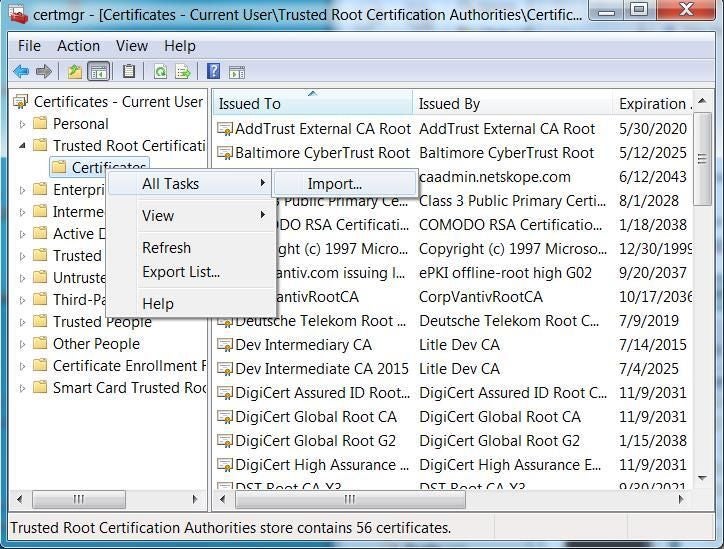
In the left-hand frame, expand Trusted Root Certificates, then right-click on Certificates and select All Tasks >Import (Figure O).
Figure O
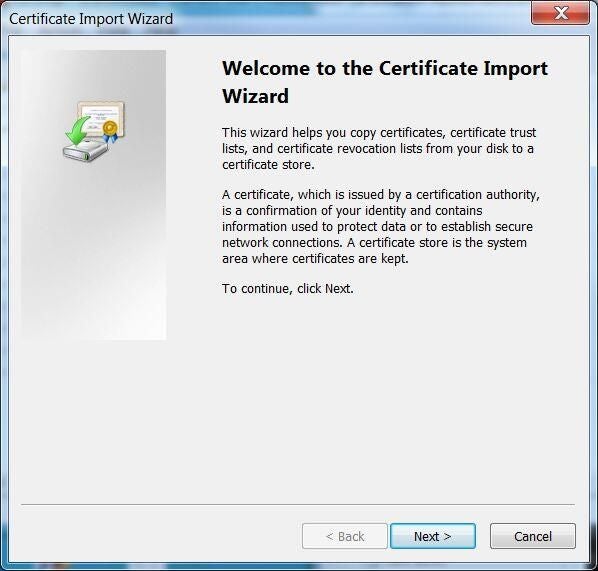
In the Certificate Import Wizard, click Next (Figure P).
Figure P
Click Next, then click Browse, then browse to and select the CA certificate you copied to this computer (Figure Q).
Figure Q
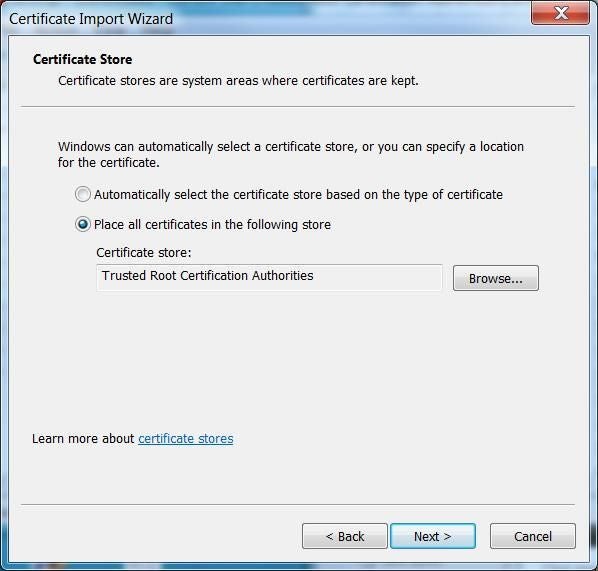
For Place All Certificates In The Following Store, select Trusted Root Certification Authorities.
Click Next, then click Finish.
Click Yes to any final prompt.
Adding the CA certificates as a Trusted Root Authority to Firefox
Unfortunately, Firefox does not trust the CA certificates that Windows does by default, so the instructions in the section above will work only if you perform this setting change in Firefox:
In Firefox, type about:config in the address bar.
If prompted, accept any warnings.
Scroll down to the security.enterprise_roots.enabled entry, which should be set to False.
Double-click the value to change it to True.
Firefox should enact the setting immediately.
If you aren’t using Active Directory/Group Policy, you can still configure Firefox to trust your CA.
Manually configuring Firefox to trust your CA
Copy the CA certificate to the host machine you want to work on.
Click Tools (Figure R).
Figure R
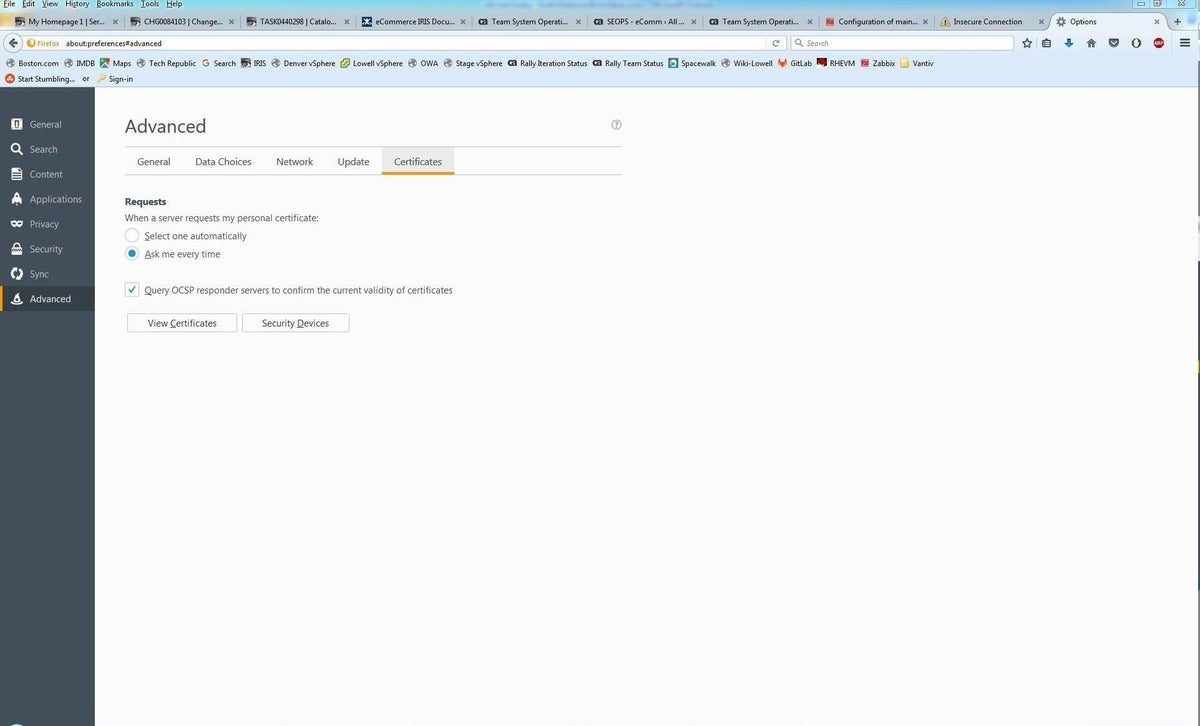
Choose Options and click Advanced, then select the Certificates tab (Figure S).
Figure S
Click View Certificates, then select Authorities (Figure T).
Figure T
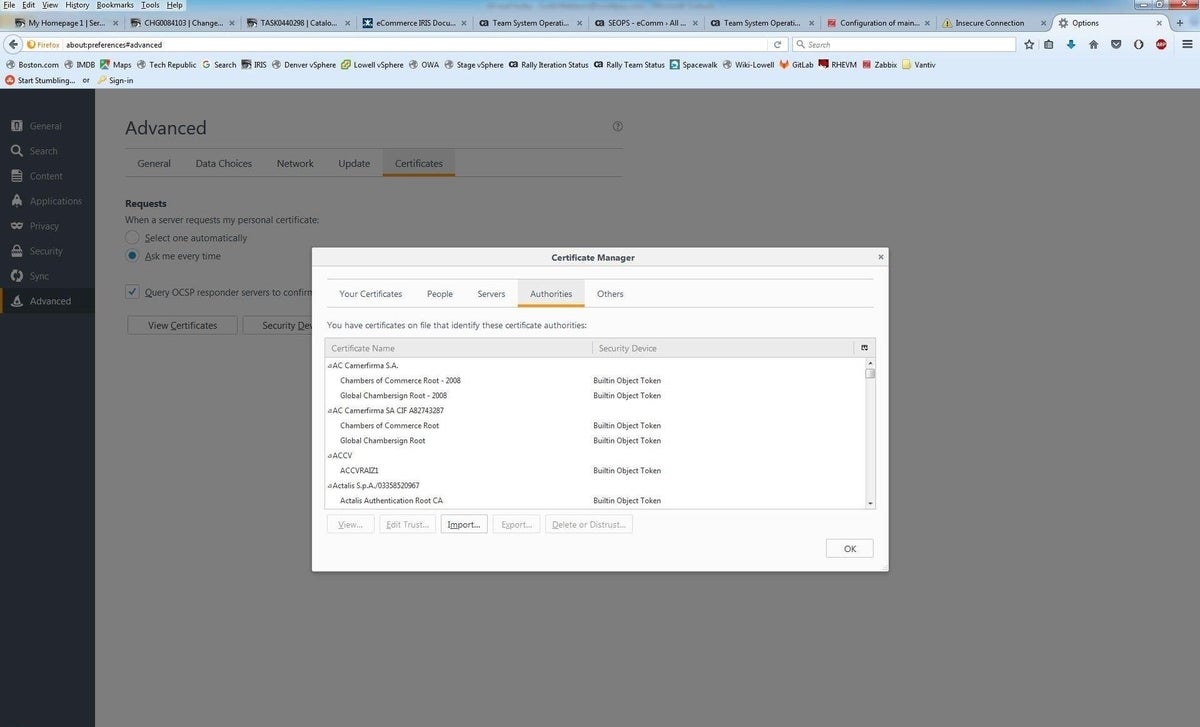
Click Import, then browse to your CA file and select it (Figure U).
Figure U
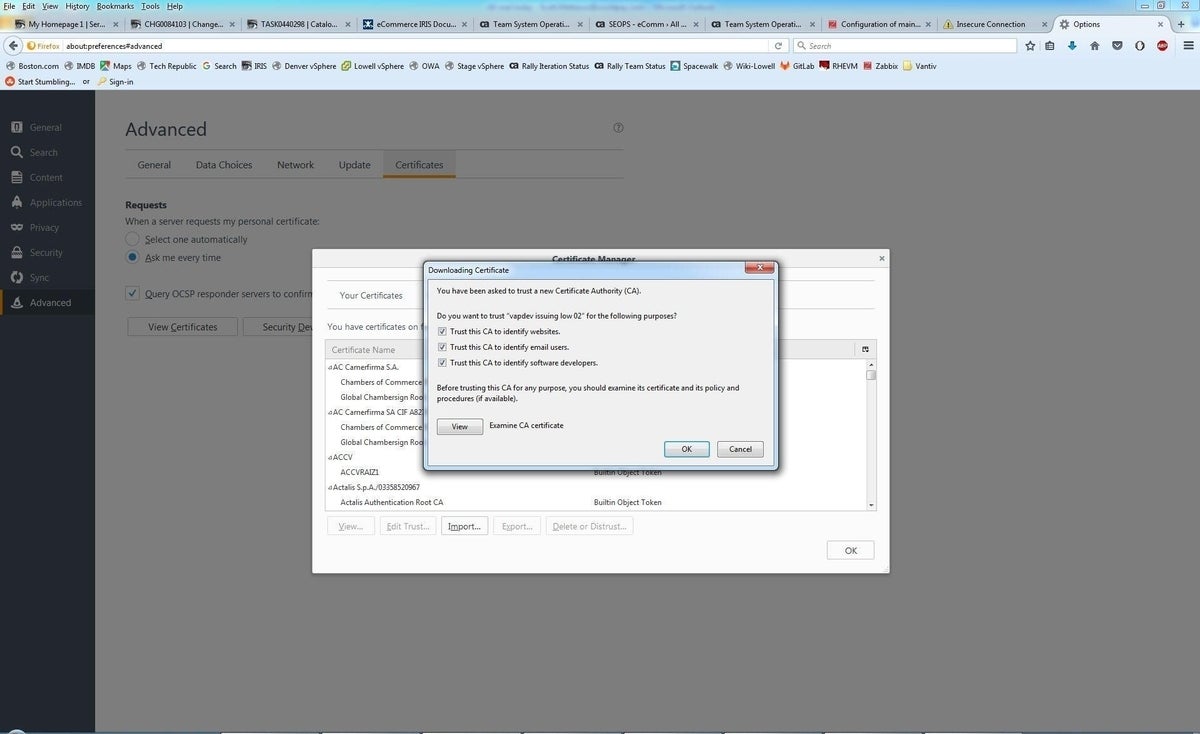
Check off all the Trust This CA options as shown above, then click OK.
Firefox should now trust the certificate authorities and stop providing security warnings.
Also read….
- Why your company should consider implementing DNS security extensions (TechRepublic)
- Let’s Encrypt brings free wildcard certificates to the web (ZDNet)
- Rampant spam, falling registrations show new gTLDs have limited business value (TechRepublic)
Your thoughts
Have you applied any of these techniques to add a trusted CA to Chrome and Firefox? Share your advice and experiences with fellow TechRepublic members.

