
There may be plenty of times and reasons why you might want or need to digitally sign a file. For instance, say you’re sharing sensitive information and you want to ensure the recipient can trust the file that contains the data. One way is to digitally sign that file prior to sending it to the client. Once the client receives the file, they can verify the signature and if they trust the digital signature, extract the file within and use the data.
On Linux, this is pretty easy to accomplish. All you need is gnupg installed, a gpg key, and the file to sign. Let me walk you through each of these steps.
Installing the software
I’ll be demonstrating on Elementary OS, but the process will be the similar with every Linux distribution (you’ll only need to modify the installation command to suit your distribution of choice).
To install gnupg, open a terminal window and issue the following command:
sudo apt install gnupg
The above command will pick up any necessary dependencies and complete without issue.
Generating a key
The next step is to generate a gpg key that will be used for the signing. The command for this will be run by the user that will do the signing of the files. To do this, issue the command:
gpg --gen-key
You will be prompted to answer the following questions:
- The kind of key you want (press Enter to accept the default RSA).
- The desired key size (go for the maximum key size, which is 4096).
- The length of time the key should be valid.
NOTE: If you want to use this key for only one file, you could set the key to expire after a single day.
You will then be prompted to fill in the following:
- Real name
- Email address
- Comment (optional)
- Passphrase
Once you’ve finished filling out the above, you will need to do some work so gpg can collect entropy for the creation of the key. Since I’ve recommended going with 4096-sized keys, you’ll need to do quite a bit. Once the key is created, you’re ready to sign.
Signing the file
The signing of a file is quite simple. From terminal window, change into the directory containing the file to be signed. I’ll demonstrate with the file ~/Downloads/gpg.docx. From the terminal window, issue the command:
gpg --sign gpg.docx
You will be prompted for the passphrase you used when generating your gpg key. If you have multiple gpg keys on your system, you can specify which key via associated email address, like so:
gpg --sign --default-key email@address gpg.docx
Where email@address is the address associated with the key to use. If you’re not sure what keys you have on your system, issue the command:
gpg --list-keys
Once you’ve entered they passphrase for the key, the file will be signed and a new file generated with the .gpg extension. With that file signed, you can verify the signature with the command:
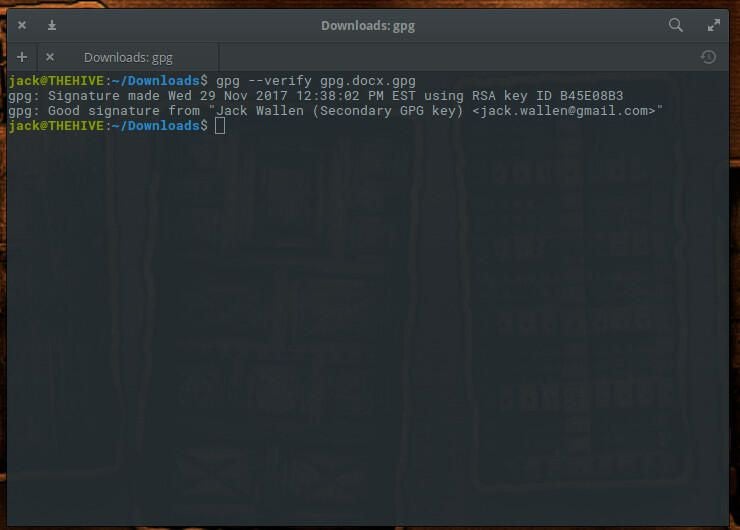
gpg --verify gpg.docx.gpg
The output of the above command will display the relevant information for the key (Figure A).
Figure A
You can send the file to the recipient, who can then verify the file and extract the file with the command:
gpg --output gpg.docx --decrypt gpg.docx.gpg
The recipient will not be asked for the passphrase for the signing key. Once the decryption is complete, they will have the document ready to use.
But wait…
You might be asking yourself this question, “What’s to stop anyone from generating a gpg key with my information and then sending bogus data to a client?” Truth is, not much. However, I do have one very easy “work around” for this. What I do is create a new signing key that lasts only a day, and then in the comment section during the creation, enter a unique phrase. When I send the file to the recipient, I will have them verify the file and have them repeat the comment. If the comment is correct, I will give them the go-ahead to decrypt and use the file. If the comment isn’t correct, they have a bogus file on their hands.
A simple path to document verification
If you like to keep things on the cheap (and in house), making use of tools like gpg for document signage makes perfect sense. It’s an easy route to helping your clients know they are getting reliable data. It’s not a perfect system, but it’s cost effective and reliable.