High volumes of malware and other malicious content are being delivered to networks in APAC, Australia, New Zealand and across the globe as a result of a set of large-scale malicious cybercriminal partnerships led by the largely secret yet insidious threat actor, VexTrio.
Renée Burton, head of threat intelligence at Infoblox and a former senior executive with the U.S. National Security Agency, told TechRepublic that VexTrio’s international network includes relationships with ClearFake, SocGholish and over 60 more underground affiliates.
Burton recommends the cyber security industry in the region focus more on uncovering and knocking out secretive middle layer players like VexTrio, rather than endpoint malware or phishing threats, and implement protective Domain Name System measures to block malicious domains.
What is VexTrio, and why is Australia and APAC in its sights?
Formed more than six years ago, VexTrio has been revealed by Infoblox as one of the world’s oldest and largest malicious web traffic brokers targeting business and consumer internet users. The VexTrio threat is estimated by Infoblox to have been worth $10 trillion USD in 2023 ($15 trillion AUD), and this is predicted to surge to $25 trillion USD ($38 trillion AUD) by 2025.
VexTrio acts as a traffic distribution system, a term lifted from similar web traffic services in the marketing world. Users lured through its international affiliate network are passed on to other criminal entities, where they can be targeted with malware and phishing (Figure A).
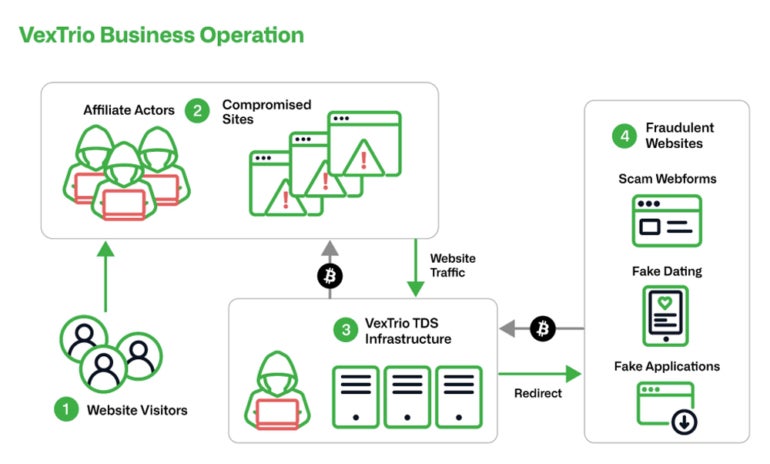
Infoblox’s research revealed VexTrio has formed strategic partnerships with SocGholish and ClearFake, which make use of malicious JavaScript frameworks, as well as over 60 other underground affiliates. SocGholish is considered to be one of the top three global threats today.
VexTrio wants APAC and Australian business and consumer internet users
Burton said APAC Australian and New Zealand business and consumer internet users are at risk because, unlike some threat actors that have a bias against targeting certain countries or regions, VexTrio was essentially “after the internet,” including in APAC and Australasia.
SEE: Australian organisations should stay atop these cyber security trends.
Operating in 32 languages — revealed through the network’s use of robo capture to identify the language of a user’s browser — Burton said there are a volume of complaints coming from the region. She said users in Japan in particular are a source of high numbers of complaints.
“If you think about one of the main ways VexTrio and their affiliates get their initial victims, well one of the main ways is through WordPress compromise,” Burton said. “They search the internet looking for websites that are vulnerable to do different kinds of attacks. They don’t care where they are.”
Opening a limited window onto the operations of global cybercrime
The partial unveiling of VexTrio is a window into how cybercrime operates globally and in APAC. While cybercriminals are often portrayed as gangs of hackers or lone brilliant coders, instead, more often they “buy and sell goods and services as part of a larger criminal economy.”
“Some actors sell malware services, and malware as a service allows buyers easy access to the infrastructure to commit crimes,” Burton said. “These service providers also form strategic partnerships, similar to the way legitimate companies do, to extend the limits of their operations.”
However, “such relationships are forged in secret and may include a number of partners,” she said, making them difficult to untangle and understand from an outside perspective. Burton said that, despite some knowledge of VexTrio, their identity and location is still a mystery.
What are the common signs of a VexTrio attack on a business?
The most common attack method deployed by VexTrio and its affiliates is a “drive-by compromise,” where actors compromise vulnerable WordPress websites and inject malicious JavaScript into their HTML pages. This script typically contains a TDS that redirects victims to malicious infrastructure and gathers information, such as their IP address.
Often, Burton said users in businesses are finding these pages through Google search results, with VexTrio affiliate websites sitting at the top of search results sending employees “down a rabbit hole.” After they have compromised a machine, and in particular through Chrome browser extensions, then they can deliver “anything they want,” including spear phishing emails.
Users who have been the subject of an attack via VexTrio typically report seeing lots of advertisements and pop-ups and/or not being able to control their browsers anymore after they have been taken over. They can have their credentials or financial information stolen.
What can APAC IT pros do to protect themselves from VexTrio?
Infoblox has called for more collective industry action targeting the middle man like VexTrio rather than destination malware or phishing pages, which have the ability to “rotate over left and right.” She said that is where the industry is focused rather than traffic distribution systems.
PREMIUM: Businesses may want to develop a security risk assessment checklist.
“As an industry, whether that is among governments or commercial enterprises, we really focus on malware — there are classes on malware, conferences on malware,” Burtons said. “We don’t focus on the infrastructure. Most products work at the endpoint security, firewall and IP layer.”
Burton added that education had been successful with the likes of business email compromise. She said it could be similarly deployed to warn users against typical VexTrio-related threats, such as saying no when pop-ups come up asking users to allow them to show notifications.
Implement available DNS protection mechanisms
Infoblox defines protective DNS as any security service that analyses DNS queries and takes action to mitigate threats leveraging existing DNS protocol and architecture. It can prevent access to malware, ransomware, phishing attacks at the source, improving network security.
Burton said countries like Australia had a history of offering protective DNS for free, and if this effort were expanded or there was more adoption, TDS domains could be blocked. This would stop threats at the middle layer, regardless of the endpoint malware or phishing page.
She recommended APAC-based IT professionals make use of the protective DNS software that is available for commercial use to control threats at the DNS level, whether that was sourced through their local governments, commercial providers or by “rolling your own.”
