Royal ransomware is malware that first appeared around September 2022. The people behind this ransomware are probably a subgroup of the infamous Conti threat actor. This subgroup, which is called Conti Team 1, released the Zion ransomware before rebranding it as Royal ransomware.
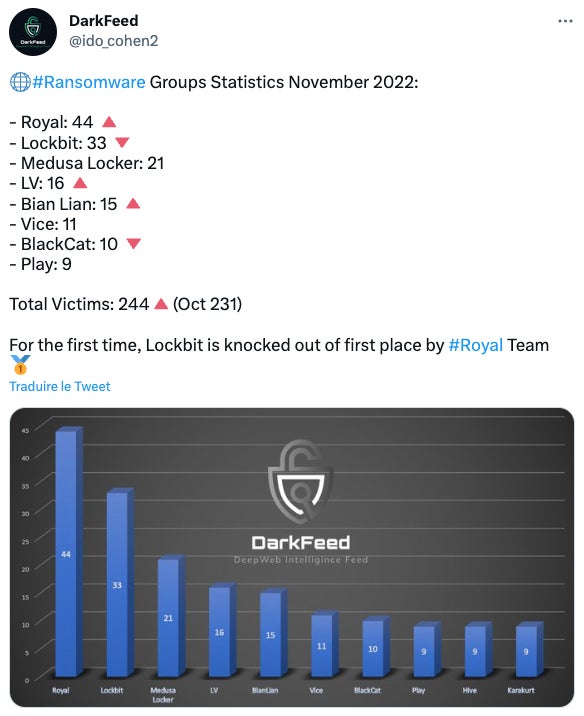
Royal spread so fast because it became the ransomware making the biggest number of victims in November 2022 (Figure A), taking the lead in front of the LockBit ransomware.
Figure A
Jump to:
- Royal ransomware’s delivery techniques
- Royal ransomware’s targets
- A new Linux threat targeting VMware ESXi
- How to protect from this Royal ransomware threat
Royal ransomware’s delivery techniques
The Royal ransomware is spread via multiple ways with the most common technique being phishing, according to Cyble Research & Intelligence Labs.
The malware was reported in November 2022 by insurance company At-Bay as being likely the first ransomware to successfully exploit a Citrix vulnerability, CVE-2022-27510, and gain access to devices with Citrix ADC or Citrix Gateway to operate ransomware attacks. The threat actor used the Citrix vulnerability before any public exploit, showing that the ransomware group is amongst the most sophisticated ransomware threat actors.
Royal ransomware also might be spread by malware downloaders, such as QBot or BATLOADER.
Contact forms from companies were also used to distribute the ransomware. The threat actor first initiates a conversation on the target’s contact form, and once a reply is provided by email, an email containing a link to BATLOADER is sent to the target in order to operate Royal ransomware in the end.
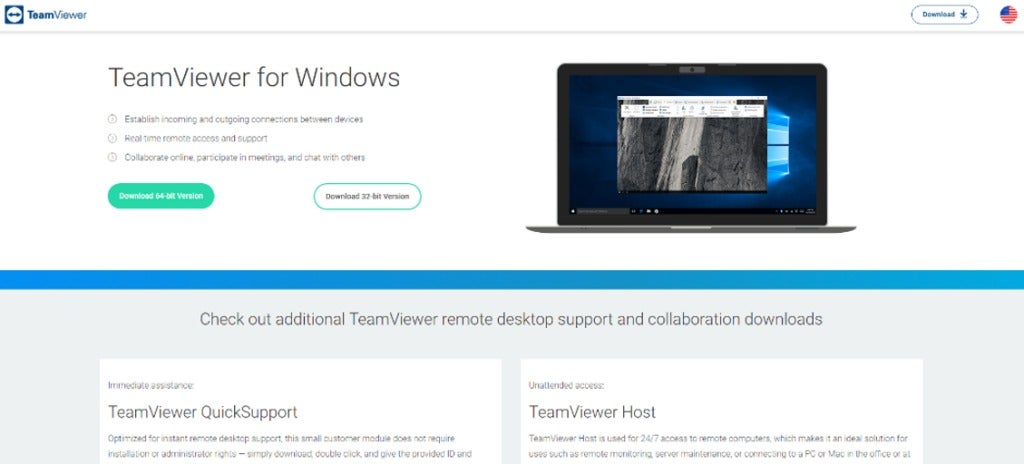
Royal ransomware has also been distributed via Google Ads or via the installation of fake software pretending to be legitimate such as Microsoft Teams or Zoom, hosted on fake websites looking legitimate. Microsoft reported about a fake TeamViewer website that delivered a BATLOADER executable that deployed Royal ransomware (Figure B).
Figure B
Uncommon file formats such as Virtual Hard Disk impersonating legitimate software have also been used as first stage downloaders for Royal ransomware.
Royal ransomware’s targets
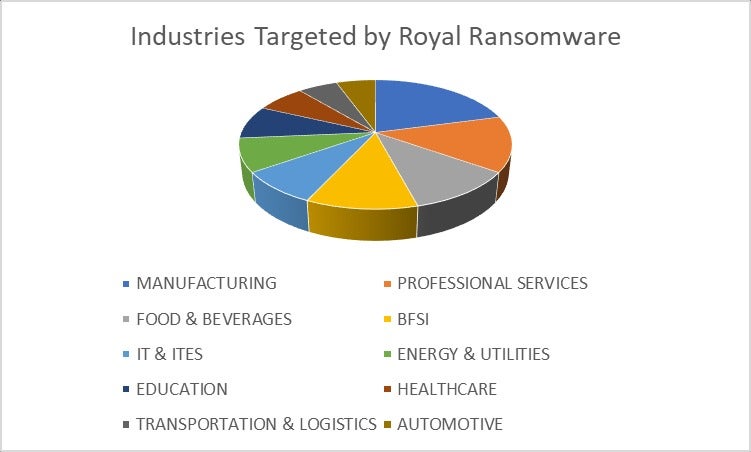
The most impacted industries targeted by Royal ransomware are manufacturing, professional services, and food and beverages (Figure C).
Figure C
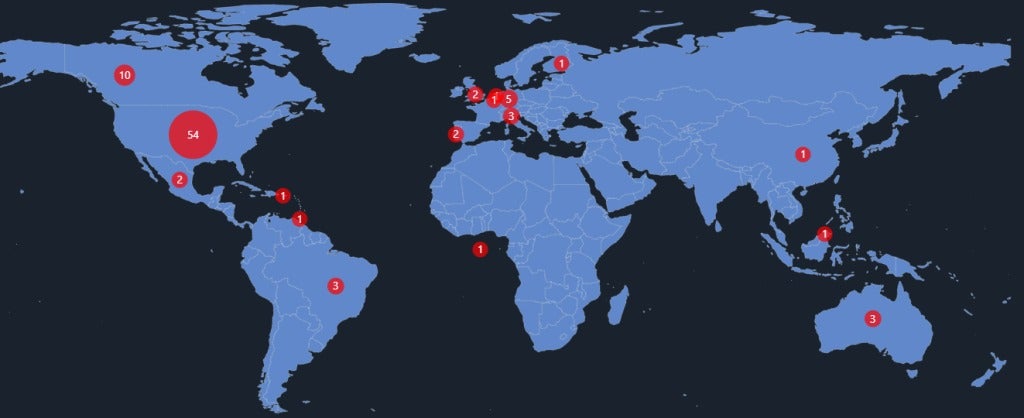
As for the location of those industries, Royal ransomware mostly targets the U.S., followed by Canada and Germany (Figure D).
Figure D
The financial range for the ransoms requested by the group varies depending on the target from $250,000 USD to over $2 million USD.
A new Linux threat targeting VMware ESXi
The new Royal ransomware sample reported by Cyble is a 64-bit Linux executable compiled using GNU Compiler Collection. The malware first performs an encryption test that terminates the malware if it fails; it consists of simply encrypting the word “test” and checking the result.
SEE: Massive ransomware operation targets VMware ESXi (TechRepublic)
The malicious code then collects information about running VMware ESXi virtual machines via the esxcli command-line tool and saves the output in a file before terminating all of the virtual machines by using once again the esxcli tool.
Multi-threading is then deployed by the ransomware to encrypt files, excluding a few files such as its own files: readme and royal_log_* files and files with .royal_u and .royal_w file extensions. It also excludes .sf, .v00 and .b00 extensions. A combination of RSA and AES encryption algorithms is used for the encryption.
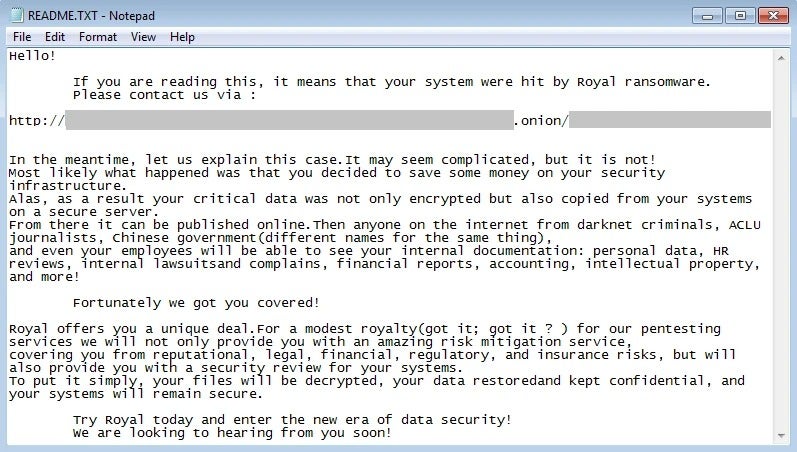
As the malware encrypts data, it creates the ransom notes in a parallel process (Figure E).
Figure E
How to protect from this Royal ransomware threat
Since the threat actor uses a variety of techniques to breach companies and deploy the Royal ransomware, several vectors of infection need to be secured. Further, the threat actor has already proved it was able to trigger non-public exploits on software, so all operating systems and software need to be always up to date and patched.
Emails are the most commonly used way for breaching companies, and this is true for the Royal ransomware gang. Therefore, security solutions need to be deployed on the web servers, and admins should check all attached files and links contained inside emails for any malicious content. The check should not only be an automated static analysis but also a dynamic one via sandboxes.
Browsers’ content should be analyzed, and browsing to unknown or low-reputation websites should be blocked, as the Royal ransomware gang sometimes uses new fake websites to spread their malware.
Data backup processes should be established, with backups being regularly done but kept offline.
Finally, employees should be made aware of this ransomware threat, particularly those who manipulate emails from unknown sources, such as press relations or human resources.
Read next: Security Awareness and Training Policy (TechRepublic Premium)
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.

