
New discoveries have been published by ESET about a cyberespionage threat actor dubbed TA410, active since at least 2018 and who targeted U.S. companies in the utilities sector and diplomatic organizations in Africa and Middle East.
SEE: Mobile device security policy (TechRepublic Premium)
This threat actor is loosely linked to APT10, a cyberespionage threat actor with ties to China’s Ministry of State Security.
TA410: Not a single group, but three
Initially thought to be a unique threat actor, ESET reports that TA410 is actually three different teams. Those teams differ by their toolsets and use of different IP addresses located in three different districts, while they use very similar tactics, techniques and procedures, which makes it harder to really separate the activities.
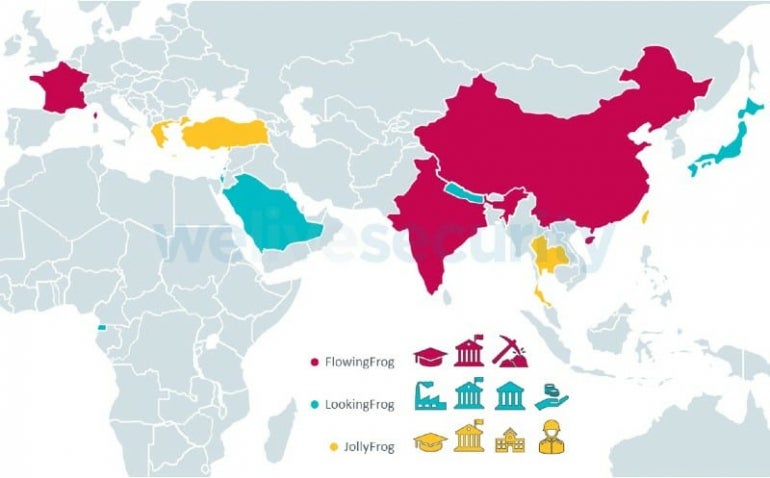
These teams are referred to as FlowingFrog, LookingFrog and JollyFrog.
It is ESET’s belief that the three work independently but may share intelligence. There is also an access team that runs the spear phishing campaigns and a team deploying their network infrastructure.
Who are the victims of TA410?
The targeting is different for every subgroup of TA410. FlowingFrog targets universities, mining and foreign diplomatic missions, while LookingFrog targets diplomatic missions, charities, government and industrial manufacturing. JollyFrog targets education, churches, military and diplomatic missions (Figure A).
Figure A
Additionally, ESET observed targeting at least twice foreign individuals inside China: one French academic and a member of a diplomatic mission of a South Asian country.
Interestingly, there is no clear segmentation among the three groups.
What is TA410’s attack scheme?
The three teams use a similar modus operandi.
For starters, spear phishing is used, but can also be replaced by the compromise of direct internet-facing applications like Microsoft Exchange or SharePoint.
Compromising such applications has the big advantage of providing an initial foothold inside an organization’s infrastructure without any need for user interaction, the opposite of spear phishing, where a user has to be enticed to click on a link or open an attached file. It is the most-seen approach used by TA410, according to ESET’s researchers.
Attackers leveraged vulnerabilities in Microsoft SharePoint servers in 2019 to gain code execution before dropping an ASPX web shell, which allowed them to install more malicious components on the server.
Further exploitation has been observed on Microsoft IIS and SQL servers running custom applications.
In August 2021, a IIS worker process loaded the LookBack malware used by TA410s LookingFrog after the ProxyShell vulnerability had been triggered. This shows that this threat actor maintains a vulnerability watch and is quick to use new vulnerabilities as soon as they pop up, in order to gain access to unpatched servers run by their targets.
More tools used by TA410
Additional tools are used by the threat actor, including vulnerability scanners, exploits from the Equation group leaks, proxying and tunneling tools (e.g., HTran, LCX, EarthWorm) and lateral movements scripts such as WMIExec, to help them move inside the compromised networks.
The infamous Royal Road malicious document builder is also used by the threat actor. An executable dubbed “Tendyron Downloader” is launched when the target opens the Royal Road-infected document. That downloader then grabs a backdoor based on Farfli malware and FlowCloud, a very complex malware used only by TA410.
It should be noted that Tendyron.exe is a legitimate executable that is prone to the DLL search-order hijacking vulnerability.
QuasarRAT and PlugX (aka KorPlug) are also used. Those malwares have been known for many years but are still used by several threat actors. QuasarRATs code is publicly shared online, making it easy to use it and tune it for different purposes.
TA410s exclusive arsenal
TA410 makes use of a few malware types that seem to be exclusive to it.
FlowCloud malware
FlowCloud is a three-components complex malware written in C++. The first component is a driver with rootkit capabilities, while the other ones are a simple persistent module and a custom backdoor.
FlowCloud is still a malware under development and can be configured differently according to the target. For example, a custom AntivirusCheck class has been found, whose purpose is to check for running processes of antivirus software. Yet that class was not used in the samples found by ESET.
The code also contains a lot of anti-debugging tricks and control flow obfuscation to render the analysis and detection harder.
FlowCloud provides full access to drives, can collect information related to mapped volumes and disk usage, but also collect files. It can also collect the list of installed software on the system it runs, in addition to process and services names.
FlowCloud can also monitor files, record audio using the computer’s microphone, monitor clipboard changes and save its data, take screen captures, and record mouse and keyboard activity. It also has a feature allowing to take a picture using the connected camera peripherals, if any.
X4 & LookBack malware
X4 malware is a custom backdoor that is used to deploy another malware dubbed LookBack.
X4 provides basic control over a compromised host: use encrypted shellcode, kill processes, list running processes or execute a command line.
LookBack is a backdoor written in C++ that relies on proxy communication to relay data between the infected host and the C2 server.
LookBack provides functionalities to list services, run processes, access files, execute command line, take screen captures or delete itself from the infected computer.
How to protect yourself from TA410
The first line of defense is to have all software patched and up to date, especially for internet-facing applications, as those are heavily targeted by attackers to get an initial foothold inside a target’s infrastructure. TA410 have shown they were monitoring new vulnerability releases and using them quickly, so patching needs to be done as soon as possible when a fix is released.
- All internet-facing servers should also be monitored for any change. New files dropped on such servers should be reported and checked carefully.
- Emails should also be carefully handled, as spear phishing is another method used by TA410 to try to compromise a system and get access to it.
- Multi-factor authentication should also be deployed, in order to avoid having an attacker get access to a system with a single username and password.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.


