
The U.K. government recently released its 2023 Cyber Security Breaches survey. The survey provides an interesting snapshot on the state of cybersecurity in the U.K. in 2022 and delivers actionable information for improving cybersecurity, which can be applied to any organization in the world. In addition, the new report aligns with the U.K.’s National Cyber Strategy.
The survey is based on interviews conducted over the phone and online between September 27, 2022, and January 18, 2023, of 2,263 U.K. businesses, 1,174 U.K. registered charities and 554 education institutions.
Jump to:
- How are businesses identifying cybersecurity risks?
- How are businesses treating supply chain risks?
- Cyber hygiene is a must, yet difficult for small, medium businesses
- What are the top cybersecurity threats?
- How are these security incidents handled?
- 2 ways to improve cybersecurity practices
How are businesses identifying cybersecurity risks?
The survey revealed the percentage of businesses that are taking the following actions to identify cybersecurity risks (Figure A):
- Used security monitoring tools (30%)
- Assessed cybersecurity risk (29%)
- Tested staff (e.g., with mock phishing exercises) (19%)
- Completed a cybersecurity vulnerability audit (15%)
- Performed penetration testing (11%)
- Invested in threat intelligence (9%)
Figure A
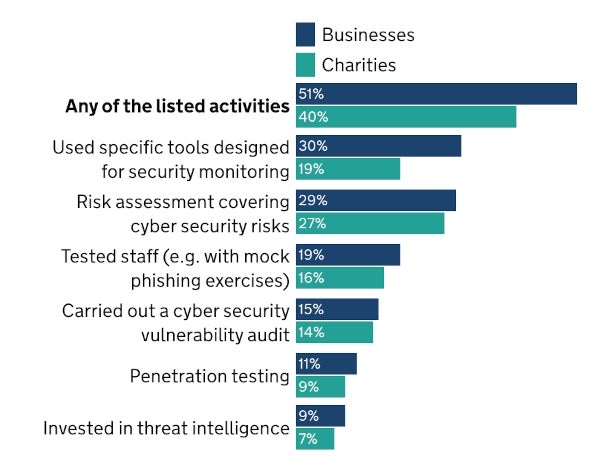
It is not expected for an organization to take all of these measures, depending on its profile. Organizations in health, social care and social work are significantly more likely than the average business to have taken any of these actions (74% versus 51%), followed by finance and insurance businesses (71%), and information and communication businesses (67%).
How are businesses treating supply chain risks?
Despite the fact that supply chain attacks have increased, only 13% of the businesses overall say they review the risks posed by immediate suppliers; the number decreases to 8% when it comes to reviewing risks associated with the wider supply chain (Figure B).
Figure B
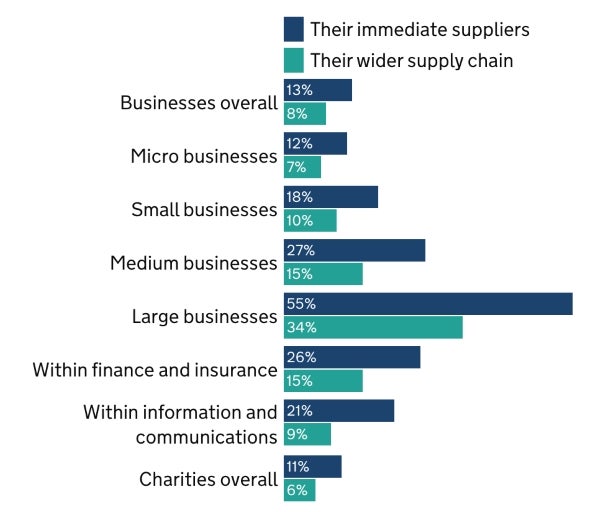
Businesses in the finance and insurance sectors are more likely (26%) to monitor risks associated with their suppliers, followed by information and communications (21%) sectors.
The immediate supplier risk has seen an increase in its monitoring, growing from 36% to 55% between 2021 and 2023. It is still hard to address the main limitations, which are:
- The time and money needed to achieve the task.
- The inability to collect information from suppliers.
For the first time, a majority of large businesses took action for reviewing their suppliers’ cyber risks, encouraged by information and guidance (e.g., from the National Cyber Security Centre) and feedback from auditors. Yet, smaller organizations do not often review that risk.
Awareness of these supply chain security risks still needs to be increased, as some interviewees mentioned that the interview was the first time they had thought about it.
Cyber hygiene is a must, yet difficult for small, medium businesses
As stated in the report, the most common cyber threats are relatively unsophisticated. A set of cyber hygiene measures can be taken to help protect organizations, such as updating malware protection, backing up data on the cloud, restricting privileges and more (Figure C).
Figure C
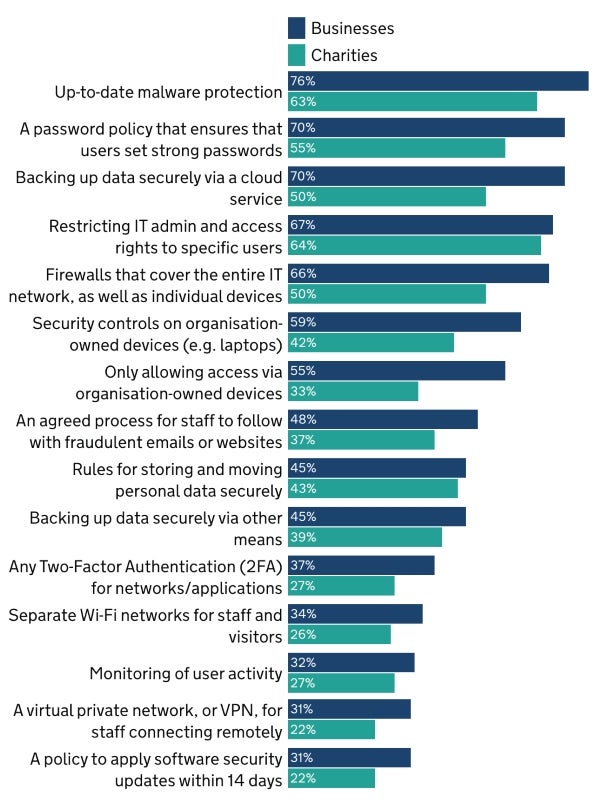
The least common cybersecurity measures are two-factor authentication for networks and applications, separated Wi-Fi networks for staff and visitors, user monitoring, VPN for remote employees, and applying software updates.
The research indicates there is an increasing cyber hygiene challenge among small to medium enterprises. Those companies report facing higher costs at different levels since the start of the COVID-19 pandemic due to inflation, higher energy prices and overall economic uncertainty, which brought small businesses and low-income charities to reduce various cyber hygiene measures. By comparison, large businesses maintained their cyber hygiene level and did not reduce measures around it.
What are the top cybersecurity threats?
Around a third of businesses and a quarter of charities reported a cybersecurity breach or attack, with larger businesses being more likely to detect breaches or attacks. The most common types of breaches or cyberattacks were (Figure D):
- Phishing remains the biggest threat at 79% for businesses and 83% for charities.
- Impersonation represents 31% of cybersecurity attacks for businesses and 29% for charities.
- Malware risks account for 11% for businesses and 9% for charities.
- Hacking or attempted hacking of online banking accounts is 11% for businesses and 6% for charities.
Figure D
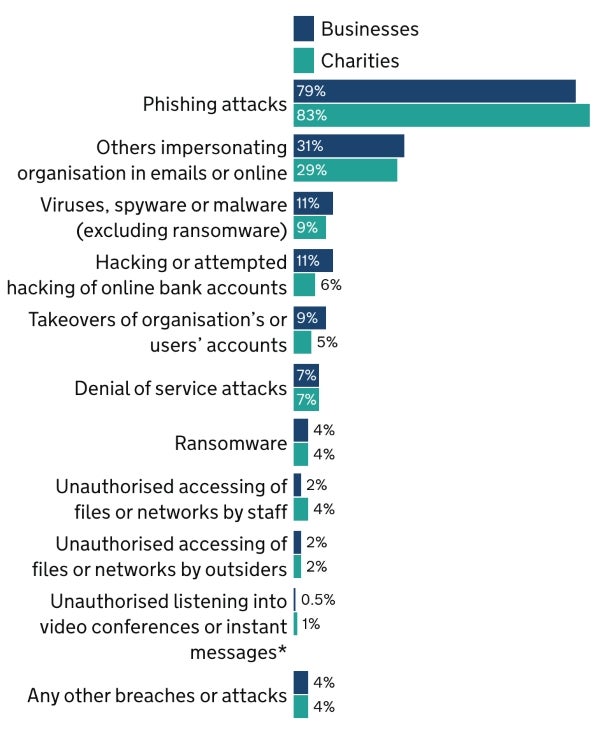
Ransomware is the seventh largest threat to organizations (4%). Fifty-seven percent of the businesses and 43% of the charities have a rule or policy not to pay ransoms; however, there is uncertainty about this topic, as 21% of businesses and 28% at charities answered that they did not know what their organization’s policy is regarding ransom payments.
How are these security incidents handled?
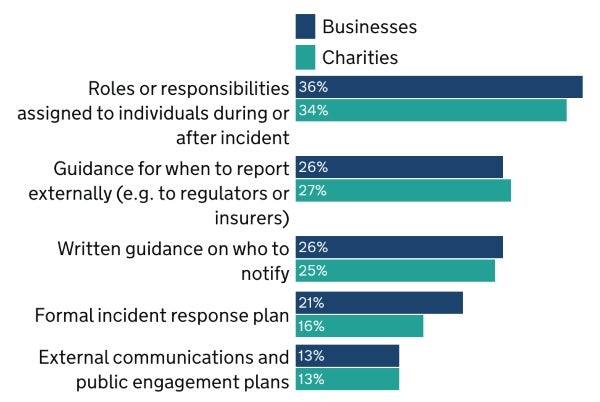
Between a quarter and a third of businesses and charities have defined specific roles and responsibilities during or after the security incident. About a quarter have guidance for external reporting and who to notify, yet only 21% of the businesses and 16% of the charities have a formal incident response plan. Thirteen percent of businesses and charities have external communications and public engagement plans (Figure E).
Figure E
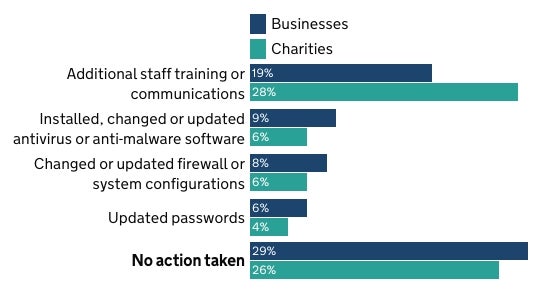
Preventing future incidents for organizations mostly consists of running additional staff training or communications. Less than 10% of businesses and charities installed, changed or updated antivirus or antimalware solutions, changed or updated firewall or system configurations, or updated passwords. More than a quarter of the organizations did not take any action (Figure F).
Figure F
2 ways to improve cybersecurity practices
The report from the U.K. government highlights rising costs and financial challenges for small organizations since COVID, which resulted in cybersecurity being deprioritized for some of those respondents. Larger organizations have not changed their security priorities, but some of them who have a strong international presence have acknowledged specific actions taken as a result of the geopolitical events and threats from state actors. In summary, cybersecurity best practices can improve for organizations of all sizes.
Better communication and more visibility between those in cybersecurity or IT roles and the wider staff, including management, can improve security, especially when IT and cyber teams can build trust in these relationships. This often goes together with good cybersecurity training and awareness raising.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.

