A new report from Mandiant reveals details about an ongoing cyberespionage operation run by a threat actor dubbed UNC3524, monitored by Mandiant since December 2019.
The targets are individuals working in companies heavily involved in mergers and acquisitions, corporate development and large corporate transactions. While such targeting may suggest financial motivations, Mandiant believes it’s instead motivated by espionage, because the threat actor maintains its access and remains undetected for an order of magnitude longer than the average dwell time of 21 days.
The operation’s modus operandi indicates a strong motivation to stay undetected and persistent: Each time a victim cleans their environment, the threat actor immediately re-compromises it with a variety of mechanisms, restarting the data theft campaign.
Strong persistence on network appliances
While the initial compromise remains unknown at this point, UNC3524 deploys a previously unreported backdoor tracked by Mandiant as QUIETEXIT immediately after gaining initial access.
The QUIETEXIT malware is based on the open-source DropBear SSH client-server tool.
According to the developer of this software, “Dropbear is particularly useful for ‘embedded’-type Linux (or other Unix) systems, such as wireless routers” and can run on a large variety of systems. This is probably one of the reasons why UNC3524 decided to develop their malware based on this software.
For instance, UNC3524 decided to install the QUIETEXIT backdoor on opaque network appliances within the victims environments: Backdoors on SAN arrays, load balancers and wireless access point controllers.
As Mandiant mentions, “these kinds of devices don’t support antivirus or endpoint detection and response tools, subsequently leaving the underlying operating systems to vendors to manage.”
By installing their malware on such trusted systems that do not support security tools, UNC3524 remained undetected in victim environments for at least 18 months.
How does the QUIETEXIT backdoor work?
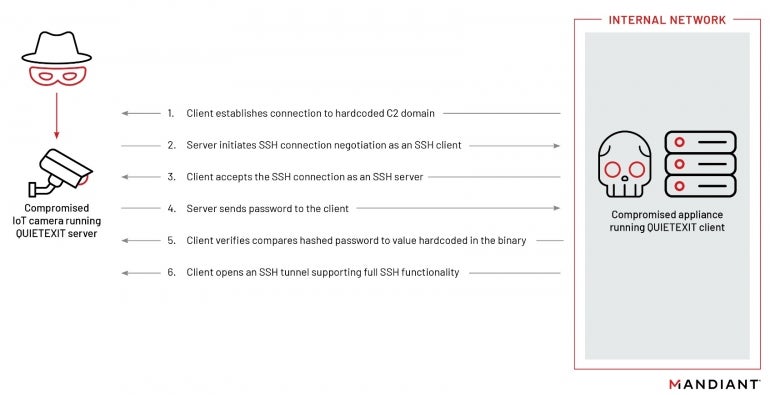
The malware works in a traditional SSH client-server mode but reversed. The component running on the compromised system establishes a TCP connection to a server before performing the SSH server role. The component running on the attacker’s side initiates the SSH connection and sends a password. Once the connection is established, the attacker can use any of the usual SSH client options, including proxying traffic via the SOCKS protocol (Figure A).
Figure A
The backdoor has no persistence method of its own, yet the attackers install a run command for it and hijack legitimate application-specific startup scripts to launch the malware.
Mandiant reports that the domains used for the C2 servers are intended to blend in with legitimate traffic originating from the infected devices. As an example, the researchers mention an infected load balancer whose C2 domains contained strings that could plausibly be related to the device vendor and branded operating system name, once again showing that UNC3524 is very cautious and determined to stay undetected with careful preparation.
Second backdoor: REGEORG malware
In some cases, UNC3524 uses a second backdoor playing the role of an alternative access into victims’ environments. The REGEORG malware is a web shell and is placed on a DMZ web server. This web shell creates a SOCKS proxy that can be used for tunneling.
The malware was named to fit other application names in order to stay undetected. Mandiant also observed timestomping on some cases, where the web shell timestamps matched the legitimate files in the same folder.
This web shell was only observed when the QUIETEXIT malware stopped working and was only used to re-install QUIETEXIT on another system in the network. While a public version of REGEORG exists, the threat actor instead uses a heavily obfuscated and little-known version of it.
Lateral movements and email theft
The QUIETEXIT backdoor is used by the threat actor to establish a SOCKS tunnel into the victim environment with fully functional SSH encryption. The actor would then use the tunnel to trigger data theft tools running on their own infrastructure, leaving no trace of the tooling itself on the infected devices.
To move laterally inside the network, UNC3524 uses a customized version of WMIEXEC, allowing them to establish a semi-interactive shell on a remote host and save registry hives while extracting LSA secrets offline.
SEE: Password breach: Why pop culture and passwords don’t mix (free PDF) (TechRepublic)
Once the threat actor is in possession of valid privileged credentials, requests are sent to the Exchange Web Services API to either the on-premise Microsoft Exchange version or Microsoft 365 Exchange Online environment, targeting a subset of mailboxes.
Mandiant observed the mailboxes targeted by UNC3524 belonged to executive teams and employees working in corporate development, mergers and acquisitions, or IT security staff, possibly to check if they were detected or not.
Once authenticated to the Exchange infrastructure, the threat actor extracts emails selected by specific filtering based on folder names and a date corresponding to the last time they accessed it.
C2 servers on cameras
All QUIETEXIT C2 domains observed by Mandiant used Dynamic DNS providers, allowing attackers to update their DNS records very quickly and easily.
On a few occasions, the dynamic DNS domains changed to lead to VPS infrastructure rather than the compromised camera botnet, maybe due to network communication issues.
The most interesting aspects of this infrastructure are the servers which act as C2: According to Mandiant, they are “primarily legacy conference room camera systems sold by LifeSize, Inc. and in one instance, a D-Link IP camera.”
These servers are likely compromised servers running the server component of the QUIETEXIT malware. Mandiant suspects these camera systems might be running older firmware or allow default credentials.
How to detect and protect from this threat
While discovering such an operation is difficult, it is not impossible.
Network detection
One key element to hunt for is the use of the SSH protocol on other ports than the usual port 22, particularly from network appliances and even more from network appliances which are not centrally managed. Large volumes of network traffic originating from such appliances should also be investigated.
Host detection
At the host level, it is possible to hunt for the QUIETEXIT malware based on several byte strings provided by Mandiant.
Protection
It is advised to enable multi-factor authentication for emails and enforce a strong password policy. It is also advised to change any default password on every network appliance and take hardening actions that are vendor-specific.
Logging should also be enabled for every appliance, with logs being forwarded to a central repository. Update and patch every system to stay up-to-date and avoid falling for an old vulnerability. More mitigation and hardening strategies are provided by Mandiant in another report.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.