Gallery: The top zero day Dark Web markets
Image 1 of 11


How zero day exploits are bought and sold
How zero day exploits are bought and sold
Kapustkiy won’t buy malware, but the hacker claims to sell zero day exploits, software loopholes that allow attackers to exploit software and networks. “I can’t name the site I use, but I think that most hackers would use the same [sites],” he said. Kapustkiy is a young, ideologically driven hacker who frequently tunnels into government and corporate sites. “I hack for political reasons,” he said in translated, broken English, “but make money sometimes from selling hacks.”
Zero day exploits are a major profit center for many hackers and are at the heart of underground cyberwar ecosystem. Though bug bounty programs are a common white hat practice for major websites and software vendors, under the clearnet is a thriving Dark Web market for malicious code. Malware and software bugs can sell for tens or hundreds of thousands of dollars on the Dark Web.
SEE: IT leader’s guide to the blockchain (Tech Pro Research)
Zero day bugs are valuable because of the high stakes for victims. Bugs in Flash or Windows grant hackers easy access to corporate systems. Malware in the form of Stuxnet was allegedly developed and deployed by the United States and Israel to attack Iran’s nuclear program, and Sandworm was allegedly used by Russian hackers to attack NATO.
To hack a major foreign embassy Kapustkiy claimed, for example, he “started by scanning the websites from the [embassy] websites to see which were related to the [primary site]. I got a huge list of around 20 domains and I saw that all of them were running on the same server and also had the same vulnerability. So I found a exploit in the web-server and I managed to hack [several sites]. It was very simple because all of the websites were running on the same server.”
WATCH: New search engine exposes the Dark Web (CBS News)
Enterprise companies and SMBs are vulnerable to a similar attack, he said, and sensitive corporate data is frequently swiped then sold on the Dark Web. “I just found a SQL [hole] in the website,” Kapustkiy said, “nothing special. They fixed [the hole] but I could still manage to hack the website with social engineering. The administrator was still using the same password and I could get access to a lot of his personal information.”
The hackers and groups in the market for zero day exploits are as diverse as the code they’re selling. Each actor has different methods of exploitation and uses a variety of sites to offload code in exchange for Bitcoin. Though Dark Web malware markets tend to appear then vanish, these are ten of the most well-known and widely used hacker websites and forms.
Before you hop on Tor and begin poking around, novices and experts alike should remember to exercise care and caution when visiting the Dark Web. Though many of these sites return benign content, much of the Dark Web is NSFW. TechRepublic does not condone illegal or unethical activity. Offensive material can sometimes be just a click away. Browse at your own risk. Never break the law. Use the Dark Web safely, and for legal purposes only.
Use the green arrows above to swipe between gallery items.
Read more:
- Zero Days: Why the disturbing Stuxnet documentary is a must-see (TechRepublic)
- Interview with a hacker: S1ege from Ghost Squad Hackers (TechRepublic)
- ‘Down the Deep Dark Web’ is a movie every technologist should watch (TechRepublic)
- Dangers of the Deep, Dark Web (TechRepublic / IBM white paper)
- Infographic and interview: The explosion of cybercrime and how to protect your business (TechRepublic)
- Inside the secret digital arms race: Facing the threat of a global cyberwar (TechRepublic)
- Cyberwar: The smart person’s guide (TechRepublic)
- How the Dark Web works (ZDNet)
- Online sales of illicit drugs triple since Silk Road closure (CNET)
0day.today
A multisignature market, 0day.today (links requires Tor) is one of the most well-known exploit markets. It is frequently used to buy and sell leaked data and zero day exploits by independent, institutional, and government hackers.
0day.in
Another multisig market, 0day.in is frequented by the underbelly of black hat hackers.
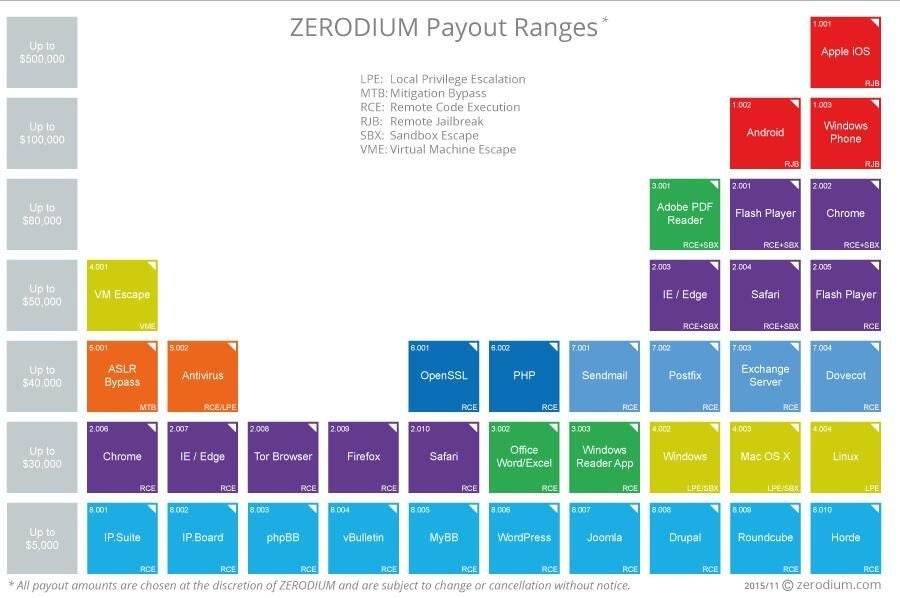
Zerodium
Founded by Vupen Security, a hacking group that exclusively sells exploits to government clients, Zerodium hopes to break open the burgeoning Dark Web market by listing and selling the top exploits with a clean and easy-to-use interface.
The Real Deal
The well-designed The Real Deal Dark Web market is as slick as it is ephemeral. The site is frequently down yet makes buying malicious code easy with an Amazon-like interface.
Darkmarket
Darkmarket is a popular Dark Web market that sells thousands of digital items, including stolen credit card information, corporate documents, and personal data.
Alphabay
With over a quarter million listings, including drugs and other illicit material, Alphabay is one of the largest Dark Web markets in the world. Though a bit passe for hardcore hackers, tens of thousands of stolen corporate documents are available on Alphabay at dirt cheap prices.
L33ter
L33ter is one of the oldest Dark Web markets. Though the site sells drugs and other illegal items, L33ter specializes in selling digital goods, hacker tools, and exploits
Rutor
Rutor.org is a Russian forum that serves as the middleman between Trust on the Dark Web, and Rutor, a Russian hacking forum, providing a place where sellers and buyers communicate.
Scan4you
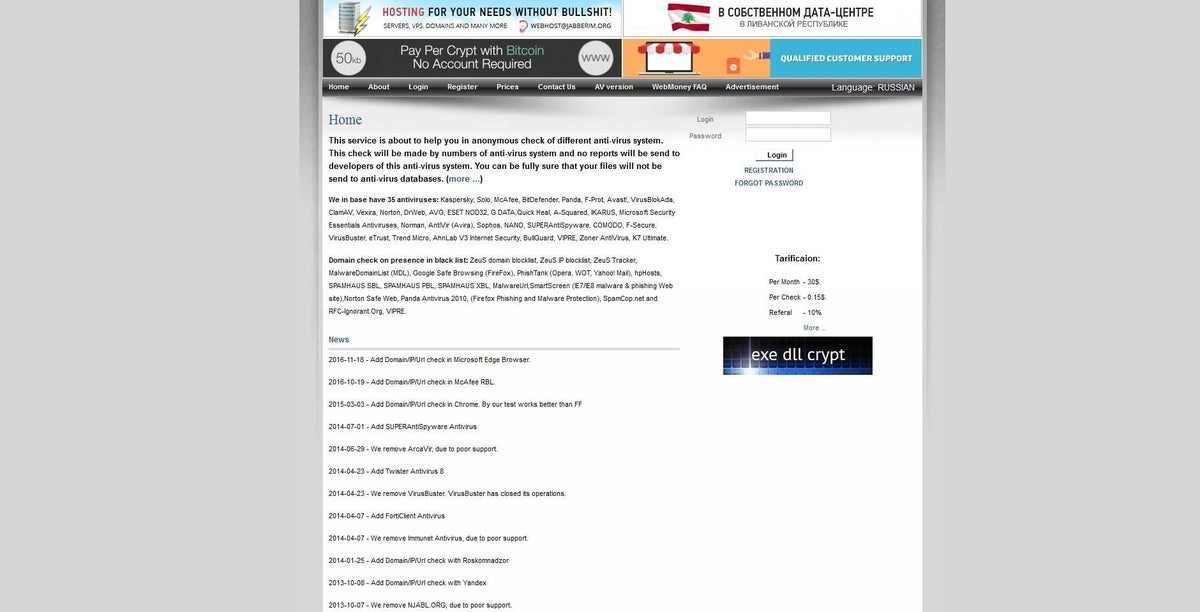
Scan4you is a clearnet market that specializes in selling botnets, hacking tools, and anti-malware software.
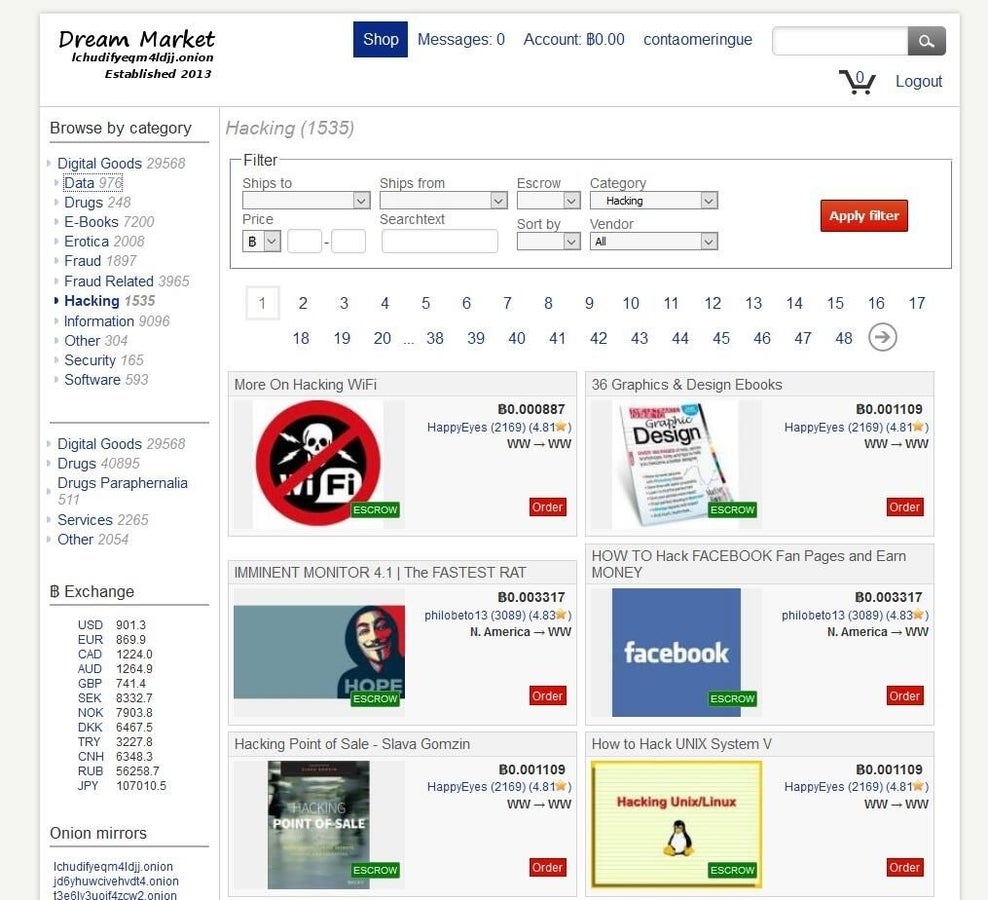
Dream Market
Dream Market is a Silk Road knock-off and sells everything from drugs to code to stolen corporate data.
-
Account Information
Contact Dan Patterson
- |
- See all of Dan's content