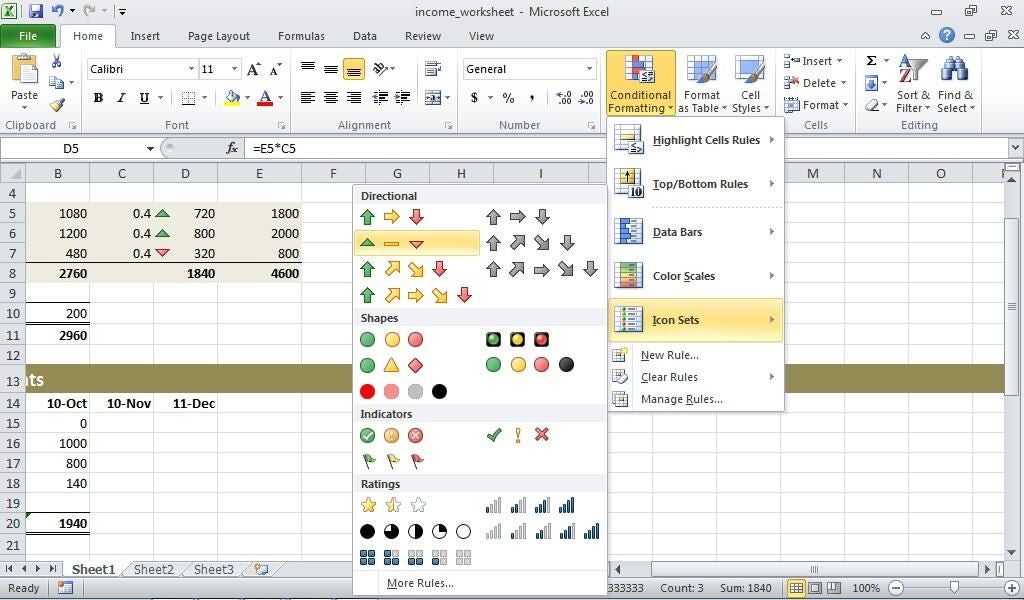
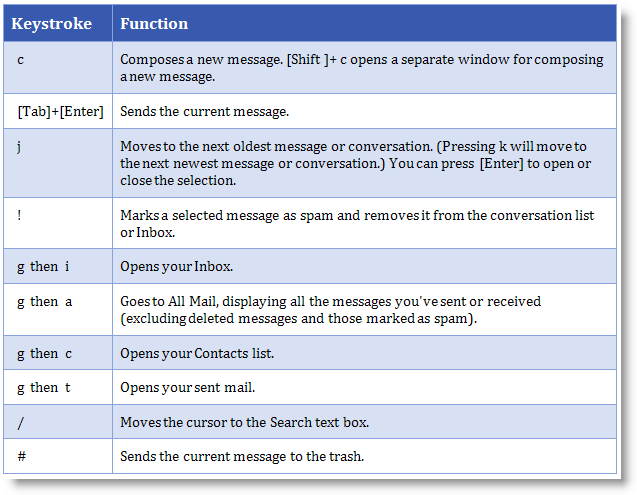
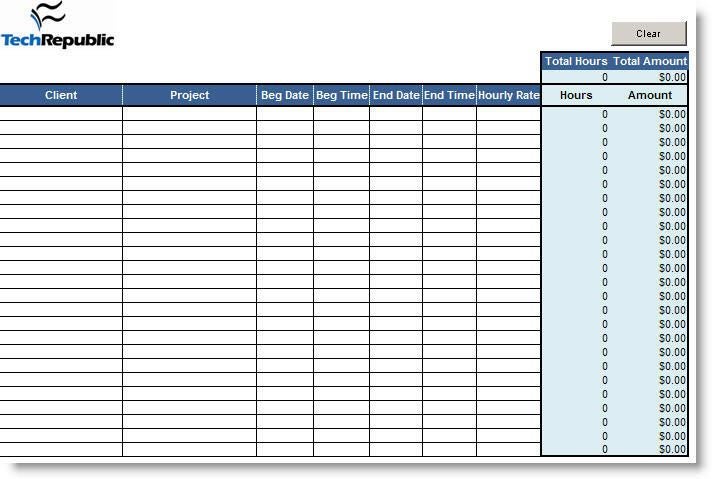
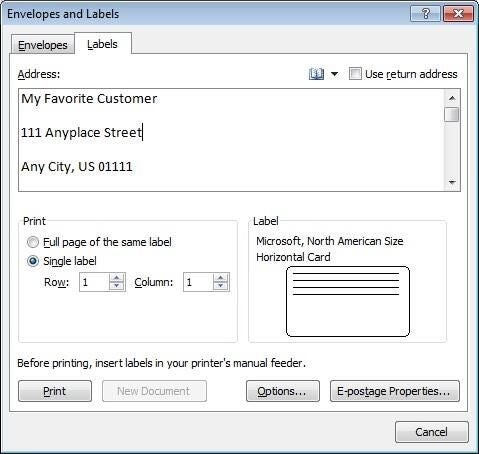
MiscPix 3
By
Jody Gilbert
Image 1 of 167
By
Jody Gilbert
Jody Gilbert has been writing and editing technical articles for the past 25 years. She was part of the team that launched TechRepublic.
-
-
Account Information
Contact Jody Gilbert
- |
- See all of Jody's content