
Phishing for credentials is a common threat that has been around for many years. It uses different social engineering techniques to persuade an unsuspecting user to click on a link or open a document and provide their credentials, which are then sent to the attacker. Now a new phishing technique has been exposed recently by a penetration tester and security researcher known as “mr.d0x” on their website.
What are BITB attacks?
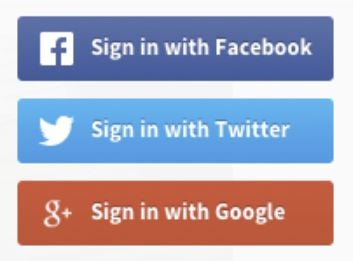
Browser in the browser attacks consist of simulating a browser window within the browser to spoof a legitimate domain. The attack takes advantage of third parties’ single sign-on (SSO) option, which has become increasingly common for users to log into many different websites. The principle is pretty straightforward: The user connects to a website, which in turn opens a new browser window that asks for Google, Apple, Microsoft or other third parties’ credentials, to allow the user to log in (Figure A). This benefits the user because they don’t need to remember or use an additional password to log into the website.
Figure A
That’s where the BITB attack comes in. In a BITB attack, the user is being served a fraudulent pop-up window that will request their SSO password. The main difference from a usual phishing case lies in the fact that in addition to popping up that window, it can show any URL, including a legitimate one (Figure B).
Figure B
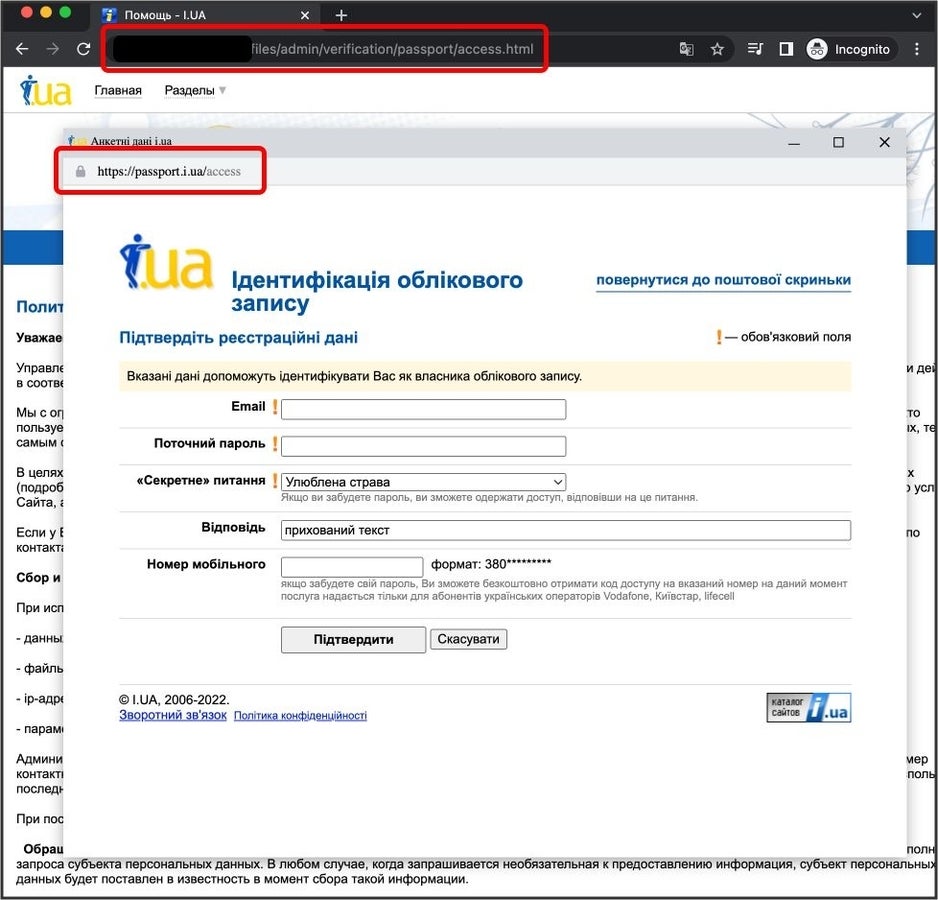
The trick works well. People have become so used to this authentication model that they do not really pay attention to it anymore and just type their credentials to log in.
SEE: Cyber threat intelligence software: How to choose the right CTI tools for your business (TechRepublic)
How does it work?
In this attack, as with usual phishing, the threat actor needs to have the user first visit a malicious or compromised page. To attract the user to the fraudulent page, the attackers generally choose to send links via emails or instant messaging software. That page will contain an iframe pointing to the malicious server hosting the phishing page.
JavaScript code can make the pop-up page appear on a link, button or page-loading screen. JavaScript also makes it possible for the attacker to show any URL for the pop-up window.
According to mr.d0x, “once landed on the attacker-owned website, the user will be at ease as they type their credentials away on what appears to be the legitimate website (because the trustworthy URL says so).”
Attacks already seen in the wild
Google’s Threat Analysis Group (TAG) reported a new attack campaign from known threat actor Ghostwriter. The threat actor originates from Belarus and has deployed BITB attacks with the phishing pages being hosted by a compromised website. Once a user provides their credentials, they are sent to a remote server controlled by the attacker. Some of the recently observed phishing domains used by Ghostwriter focus on Ukraine.
We suspect a lot more threat actors will quickly adapt and use this new technique in their attack campaigns.
SEE: Best encryption software 2022 (TechRepublic)
Recommendations
It seems unreasonable to ask users not to use SSO anymore. They have gotten used to it and it works nicely in most cases. Adding multi-factor authentication (MFA) is a good way to improve security for SSO authentication, yet it could still be bypassed by attackers, by using malware, for example. When it comes to increasing security in phishing cases, the best MFA solutions are hardware devices or tokens.
The use of password managers might also help in the particular case of the BITB attacks. Since the phishing page is in fact not a real browser window, password managers with autocomplete options might not react to them, alerting the user who will wonder why the autocomplete function does not work.
The best ways to avoid BITB attacks are actually the same as for usual phishing. Users should not click on links or attached files coming from unknown sources via email or instant messaging software. If they have doubts about an email coming from a seemingly legitimate entity or colleague, the user should call and verify they were indeed the sender and that the shared link or file is safe.
Anti-phishing solutions should also be deployed and used. If possible, those solutions should allow the user to easily report to the IT department or even to anti-phishing organizations.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.


