Two familiar problems are increasing cybersecurity risks for companies that use software-as-a-service: a lack of visibility and too many cooks in the kitchen. A new survey from the Cloud Security Alliance found that IT teams don’t have a complete picture of SaaS in use by business units. That leads to the second big problem: Too many departments have access to security settings within SaaS apps.
The Cloud Security Alliance is a not-for-profit organization that promotes best practices for ensuring cybersecurity in cloud computing and IT technologies. Adaptive Shield commissioned the survey which included 340 IT and security professionals.
Causes of SaaS cybersecurity concerns
Misconfigurations seem to be the start of the security problems with 43% of respondents stating that they have suffered one or more security incidents because of a misconfiguration. Twenty percent were unsure if a misconfiguration was the cause of a breach.
The survey identified two leading causes of SaaS misconfigurations:
- Too many departments with access to SaaS security settings: 35%
- Lack of visibility into changes into the SaaS security settings: 34%
Forty percent of respondents said that business departments, such as legal, marketing and sales, have access to security settings.
Charlie Winckless, a senior director analyst on Gartner’s Infrastructure Protection team, agrees SaaS usage is rarely centralized with a single department like IT.
“This means that many organizations not only don’t have tooling and staff, they are not necessarily even aware of what business-critical SaaS applications are in use,” he said. “Without this central visibility and control, elevated privilege and excess access is relatively common.”
The survey also found that investment in business-critical SaaS applications is outpacing SaaS security tools and staff. Eighty-one percent of respondents said they have seen an increase in SaaS use but only 73% have increased security tools for SaaS deployments and only 55% have increased staff for SaaS security.
SEE: Do you need a SaaS platform to manage your “SaaS sprawl”?
Winckless said that many business people make the mistake of seeing SaaS as “Simple-As-A-Service.”
“SaaS is purchased but often not maintained, given due rigor in configuration, or otherwise treated like any other application due to this misperception,” he said.
There are signs that this attitude is changing, according to Winckless, who sees IT teams looking for ways to establish better control without denying the business flexibility.
“Bringing SaaS governance into fusion teams like a cloud center of excellence is one approach that seems to work here,” he said.
How to close SaaS security gaps
Winckless recommends that security teams should have tooling to help understand and discover all SaaS apps in use, not just those the business team reports.
Tools such as cloud access security brokers and SaaS security posture management tools can serve this purpose. SSPM is a set of security and automation tools that enables an organization’s security and IT teams to get visibility and manage the security posture of SaaS environments.
“One other key control is ensuring all SaaS is at least federated with enterprise identity and that access is protected by strong authentication such as MFA–a recommendation that goes at least double for administrative accounts,” he said.
Jay Heiser, a research VP of cloud security at Gartner, said he has been an early advocate of discovery tools, but he rarely gets questions on this topic. This suggests that IT pros don’t consider it their responsibility to find out what SaaS is in use.
“There are too many IT professionals who just wish that SaaS would go away and stop bothering them, but SaaS is here to stay,” he said. “People who want long-term careers would be well-advised to find ways to work within this new reality, helping their organizations optimize their use of cloud services.”
SEE: SaaS adoption is happening faster and slower than you think
The survey found that a lack of visibility into third party application access to the core SaaS stack is the top concern when adapting SaaS applications followed by a lack of visibility into security settings.
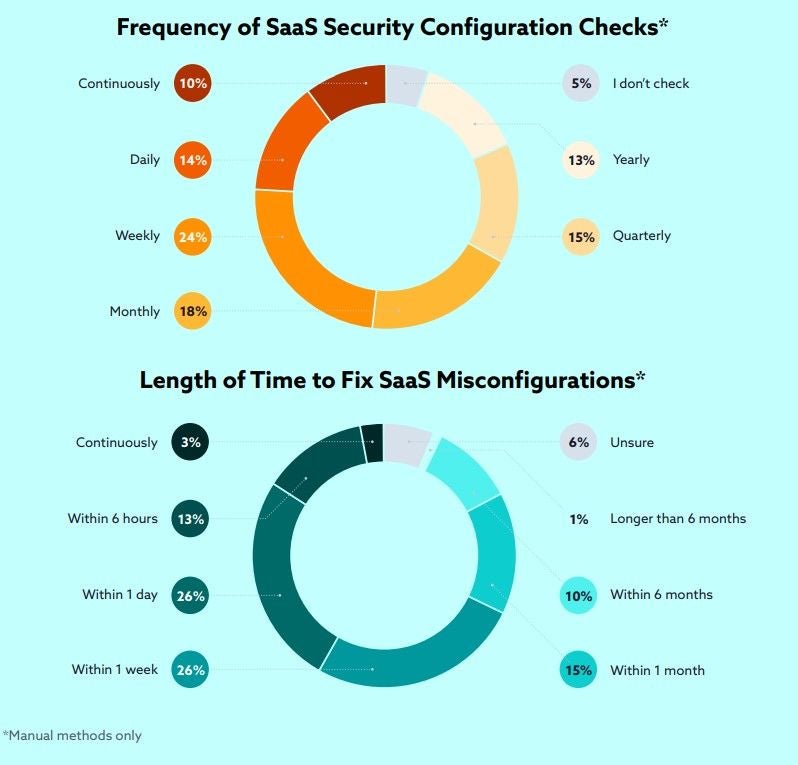
When an organization finds an unapproved SaaS installation, only 47% perform a full security review, while 24% conduct an abbreviated review. Fifty-seven percent said security reviews are manual with 26% using an automated approach. Fourteen percent said they do not monitor SaaS security misconfiguration.
A majority of survey respondents (59%) indicated that the security team is responsible for managing SaaS app security followed by the IT team (50%). Only 40% said the business application owner was responsible.
