
This may sound like a crazy way of enhancing security on a server, but if you can get away with it–as in you don’t need any USB devices such as keyboards, mice, external drives–disabling USB support can be an added means of ensuring malicious files do not find their way onto your servers. Obviously, this will only work for headless machines, so you better make certain you can SSH into those servers, otherwise, you’ll find yourself in trouble trying to input anything via keyboard or mouse.
However, if your Linux server is setup as headless, this can be a pretty handy way to prevent data breaches. I have two reliable ways to disable USB. There is another method, but it actually removes the USB driver. Personally, I’d rather make it such that USB support can be easily added back, on the off-chance it is again needed for some reason. With that said, let’s first disable USB support on our headless Linux servers. I’ll be demonstrating this on Ubuntu Server 16.04, but the process works on most modern Linux distributions.
Disabling USB
First we’ll disable USB by way of tricking the system into not installing the usb-storage module. This is called a “Fake Install.” To do this, open up a terminal and issue the command sudo nano /etc/modprobe.d/block_usb.conf. Within that new file, add the following contents:
install usb-storage /bin/true
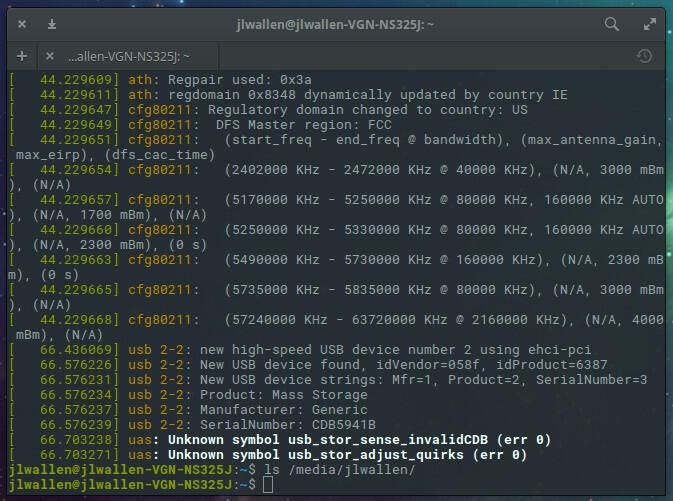
Save and close the file. Reboot the system and the change will take effect. When a user attaches a USB device, it will not be recognized. For example, a plugged in USB device will not show up in either the GUI file manager or in the directory hierarchy. The one caveat to this is the USB device will show up in the dmesg command output (Figure A).
Figure A
The next method is a bit more harsh, but it works. What we’re going to do is change the permissions of the /media folder, such that an external device simply cannot be mounted to this directory, which happens to be the default for modern Linux distributions. This isn’t perfect–as someone with the right skills and user privilege could simply change the permissions or mount the USB drive to another location. But for those without the necessary Linux skills, this will certainly slow them down a bit.
The first thing you must know is that the original permissions for the /media folder are 755. That’s important if you need to restore the ability to mount into that folder. With that said, open up a terminal and issue the command:
sudo chmod 000 /media
After issuing that command, plug in an external USB device and try to mount it. It will not work.
Should you need to restore the ability to mount into the /media directory, issue the command:
sudo chmod 755 /media
Once you’ve done that, everything will be fine.
A quirky addition to security
These methods aren’t perfect, and are a bit quirky, but they will help prevent just anyone from plugging in an external USB device and either loading malicious files to your Linux servers or taking data from them. If you’re looking for a means of security not found in the traditional routes, give these methods a try and see if they don’t help. Just remember, this isn’t a means to an end, it’s just a possible method to add additional security to a server that should already be hardened.
Of course, if all else fails, you could employ something like these Kensington Port Lockers.