Data security is of the utmost importance in your data center. To that end, you may have deployed Linux servers. It makes sense. Linux offers an unrivaled combination of security and flexibility. It is that flexibility which makes Linux so ideal for your data center. However, as with any platform, the out-of-the-box experience might not be up to your standards. Fortunately, there are plenty of tools available that can beef up the security of your server.
One such tool is Tripwire, a security and data integrity tool that is used for the monitoring and alerting of specific file changes. Tripwire is available as an enterprise and an open source solution. The biggest difference between the two is that the enterprise solution is available for Linux, Solaris, AIX, and Windows (whereas the open source solution is only available for Linux). There is, of course, also commercial support available for the enterprise edition.
I’m going to demonstrate how to install and configure the open source version of Tripwire on the Ubuntu Server 16.04 platform, such that it will monitor for modified files and alert you of any changes.
SEE: Securing Linux policy (Tech Pro Research)
Installation
Tripwire can be found within the standard repositories, so installation is as simple as issuing the command:
sudo apt install tripwire
During the installation, you will be presented with a number of ncurses-based windows (Figure A), that require you to:
- Configure Postfix for SMTP configuration (you can choose between No configuration, Internet Site, Internet with smarthost, Satellite system, Local only).
- Configure the mail system name (leave the default)
- Create both site and local authentication keys
- Rebuild the Tripwire Configuration and Policy (choose Yes for both)
- Enter both the site- and local-key passphrases
Figure A
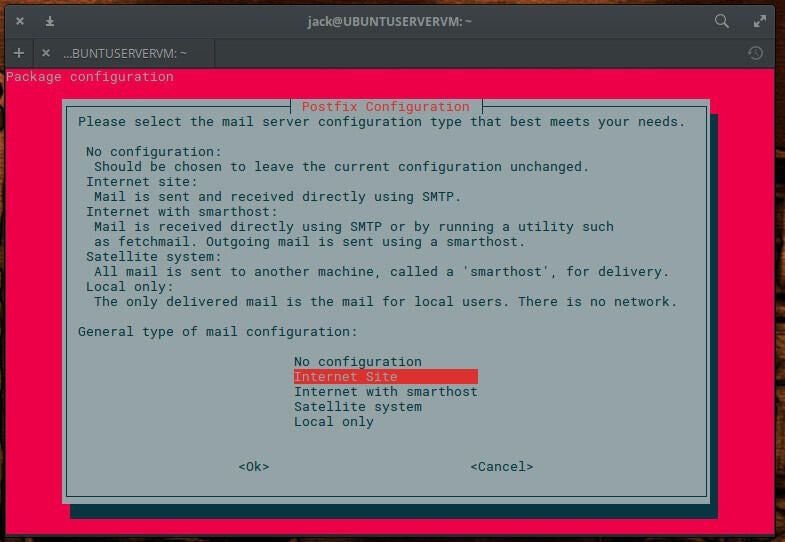
Configuration
Next we begin the configuration process. To start this, initialize the database with the command sudo tripwire –init. You will immediately be prompted for your sudo password and then the local passphrase (created during installation). The initialization process will proceed, only to error out with “No such file or directory” (Figure B).
Figure B
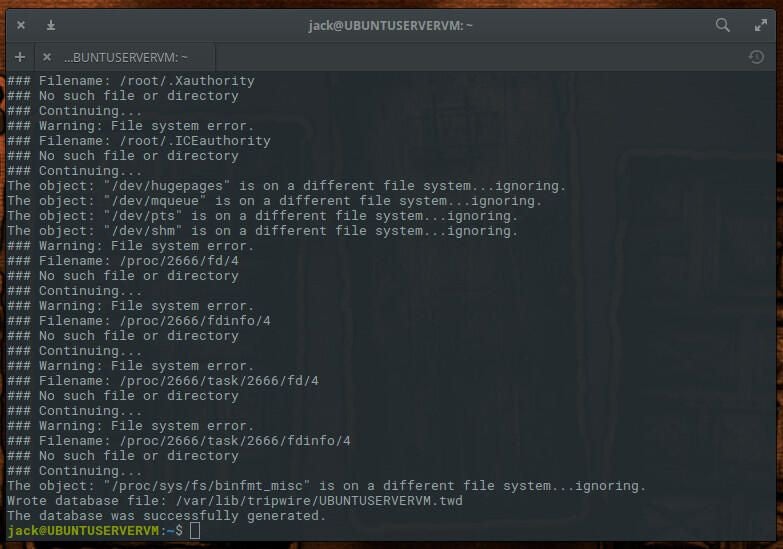
To get around this error, the Tripwire configuration file must be edited. However, before we do this, we need to first find out what directories are missing. To do that, issue the command:
sudo sh -c "tripwire --check | grep Filename > missing-directory.txt"
There will now be a text file, called missing-directory.txt, that you can refer to. Open the Tripwire configuration file (in your text editor of choice) and prepare to make a number of changes. The configuration file in question is /etc/tripwire/twpol.txt. The first section to edit is found under rulename = “Boot Scripts”. Comment out the line /etc/rc.boot by placing an # character at the beginning of the line (Figure C).
Figure C
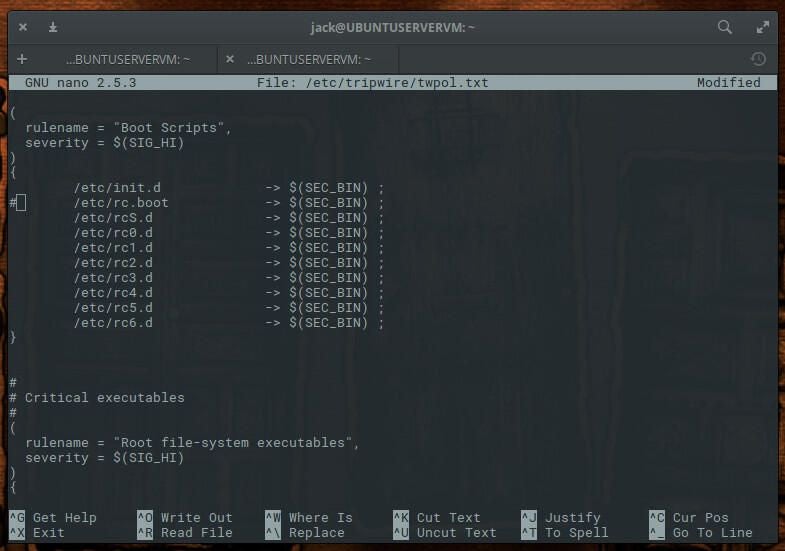
Next scroll down to rulename = “System boot changes” and comment out the following lines:
/var/lock
â/var/run
Scroll down to rulename = “Root config files” and comment out everything but:
/root
/root/.bashrc
Scroll down to rulename = “Device & Kernel information” and comment out:
/proc
Save and close the file.
Regenerate the encrypted policy file with the command:
sudo twadmin -m P /etc/tripwire/twpol.txt
You will be prompted for your site-key passphrase. Once you authenticate that passphrase, the policy file will regenerate. You then must reinitialize the Tripwire database with the command:
sudo tripwire --init
You will be prompted for your local-site passphrase. Once you’ve authenticated that passphrase, the database will be initialized, without error.
SEE: Defending against cyberwar: How the cybersecurity elite are working to prevent a digital apocalypse (free PDF) (TechRepublic)
Testing integrity
Let’s run a test with our newly installed Tripwire system. Issue the command sudo tripwire –check. Once the command completes, you should see No Errors reported (Figure D).
Figure D
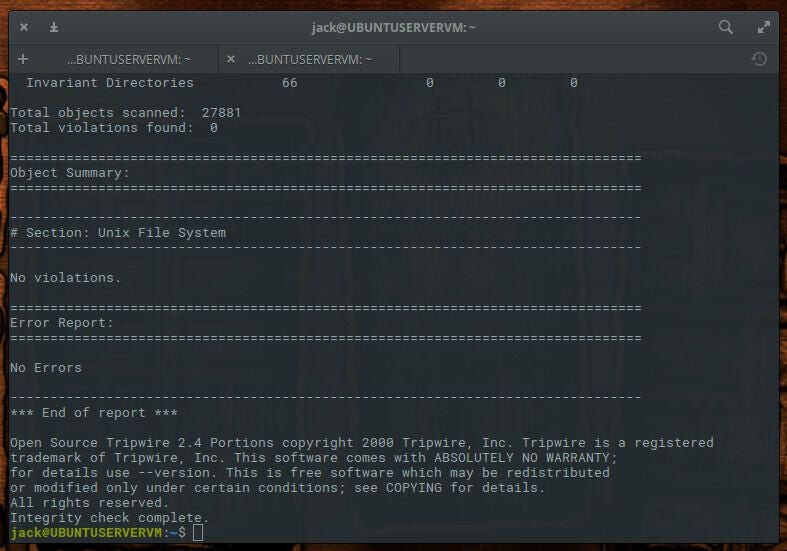
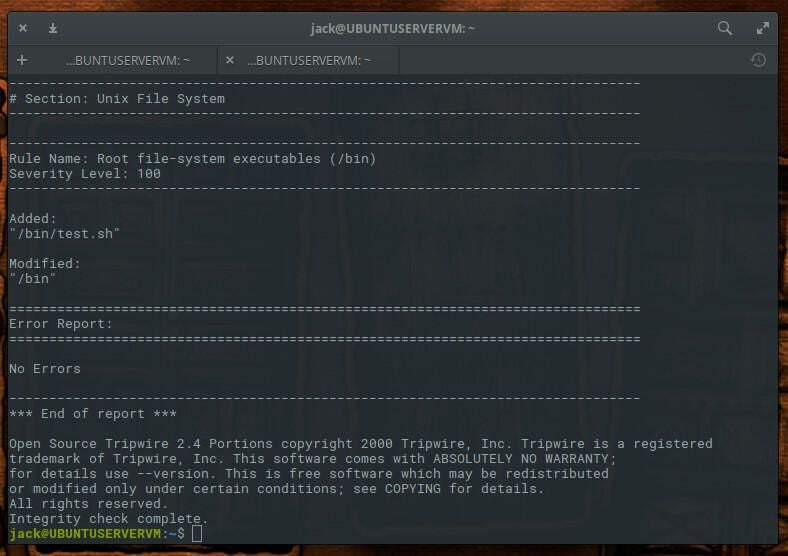
Let’s test this further. Add a sample file with the command sudo touch /bin/test.sh and then rerun the check with the command sudo tripwire –check. You should now see two violations (our added file and a modification to the /bin directory–Figure E).
Figure E
Create a new rule
Let’s say you use this server for web hosting and you want to create a tripwire rule to monitor the /var/www/ directory for any violations. To do this, open up the /etc/tripwire/twpol.txt file for editing and add the following:
# Rules for web hosting
(
rulename = "Web Hosting Ruleset",
severity = $(SIG_HI)
)
{
/var/www -> $(SEC_CRIT);
}
Save and close the file. Regenerate the Tripwire config file with the command:
sudo twadmin -m P /etc/tripwire/twpol.txt
Reinitialize the Tripwire database with the command:
sudo tripwire --init
Let’s test the new rule by adding a test file in /var/www with the command sudo touch /var/www/test. Rerun the check and your test file should be flagged.
Email notifications
Naturally, you don’t want to have to manually run Tripwire. That’s where cron and notifications come into play. What we want to do is first test to make sure email can be sent from the system. Issue the command:
tripwire --test --email EMAIL@ADDRESS
Where EMAIL@ADDRESS is an email address you have access to.
Once you receive the email, open up the Tripwire configuration file in your editor of choice and add the following line to any rule you want to monitor via email:
emailto = EMAIL@ADDRESS
Where EMAIL@ADDRESS is the actual email address. So, for example, our Web Hosting rule would look like:
# Rules for web hosting
(
rulename = "Web Hosting Ruleset",
severity = $(SIG_HI),
emailto = EMAIL@ADDRESS
)
{
/var/www -> $(SEC_CRIT);
}
Of course, since we’ve altered the configuration file, we have to regenerate the configuration and reinitialize the database with the commands:
sudo twadmin -m P /etc/tripwire/twpol.txt
sudo tripwire --init
At this point, you can now manually run a Tripwire check and have the results mailed to you, with the command:
sudo tripwire --check --email-report
Cron
It’s time to automate the system, with the help of cron. Open up your root user crontab for editing with the command sudo crontab -e -u root. At the bottom of the file, add the following:
0 0 * * * tripwire --check --email-report
Save and close the file. Restart cron with the command sudo systemctl restart cron.
That’s it. Tripwire will now perform a daily check on your system and email you the results.
Rest assured
With Tripwire monitoring your Linux server, you can rest assured you will be notified should a change be made to the system. If an alert was a planned change, you can ignore it. If, however, you did nothing to the system and still receive an alert, it’s time to start plowing through log files to see what happened.
