
You have Apache set up and serving your sites to perfection. Or so you thought.
A team member informs you she can navigate through the folder hierarchy of your Apache server. This could end in security issues you don’t want to face.
The fix for this is quite easy and allows you to do it for individual sites or for your document root (i.e., the default location where your Apache sites are served from). There are two easy methods of achieving this; I’ll show you both.
I assume you have Apache running and serving up sites. I also assume you have sites in standard and nonstandard locations. For the sake of this example, our server will have a document root of /var/www/ and our nonstandard sites will be served from /srv/www. My demo will be with Apache2 on Ubuntu Server 16.04.
SEE: Network Security Policy (Tech Pro Research)
Working with the Apache configuration file
Our document root is /var/www. Let’s say (for testing purposes) we have the folders /var/www/html/test and /var/www/test/test1.
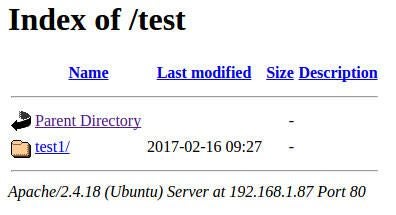
Before making these changes, if we point a browser to http://IP_OF_SERVER/test (IP_OF_SERVER is the IP address of the server), we’ll see the test1 folder displayed (Figure A).
Figure A
Let’s prevent this from happening. Open a terminal window and change into the /etc/apache2 directory. Open the file apache2.conf in your favorite text editor (you’ll need admin rights to edit the file). Scroll down until you see the <Directory /> section (Figure B).
Figure B
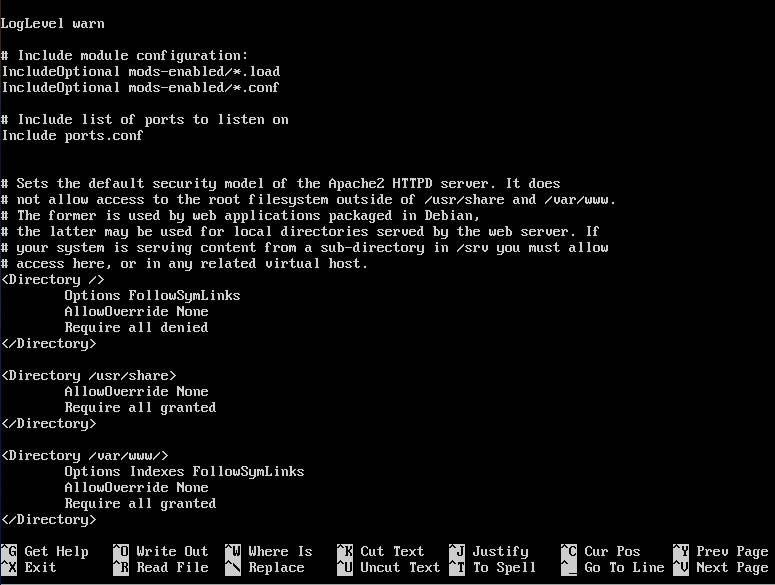
We’ll edit this section:
â Options Indexes FollowSymLinks
â AllowOverride None
â Require all granted
â
Switch off Indexes by removing the Indexes option. The new section will look like this:
â Options FollowSymLinks
â AllowOverride None
â Require all granted
â
Save and close that file. Restart the web server with this command:
sudo service apache2 restart
Point your browser back to the same directory, and you’ll be presented with a 404 Not Found error.
Using htaccess
Let’s look at a different method of handling this problem. This time around we’ll use htaccess, so you can easily block a directory listing on any folder, in any defined virtual host on your server.
We’ll configure a site served up from /srv/www. You will have already configured the .conf file for this site in /etc/apache2/sites-available (and linked it to /etc/apache2/sites-enabled). Open that .conf file in your favorite editor and in the Directory section change AllowOverride None to AllowOverride All. Save and close the file.
Now we must create a new .htaccess file in the target folder (in our case /srv/www). From your terminal window, issue the command sudo nano /srv/www/.htaccess. In this new file, add the line:
Options -Indexes
Save and close the file. Restart Apache with this command:
sudo service apache2 restart
Your nonstandard site will show a 403 Access Forbidden error when you try to view a sub-directory.
Done and done
Congratulations! Your Apache site no longer lists directories. This is a very simple step you can take to secure your Apache web server and prevent people from seeing directories and files they shouldn’t see.