
If you have Linux data center servers that require users to be able to send and receive files via SFTP, you might want to consider securing that system via a chroot jail. By doing this, you ensure that those who need to work with SFTP are locked into a specific directory and cannot access the server’s directory structure.
How do you do this? By using a chroot jail. Let me show you how.
SEE: Windows 10 security: A guide for business leaders (Tech Pro Research)
What you need
The only things you need are a running Linux server and a user with sudo privileges. That’s it. You’re ready to rock.
Creating a new group
The first thing to do is to create a new group for SFTP users. Open a terminal window and issue the command:
sudo groupadd sftponly
Adding and modifying users
Next, we need to add users to this new group. If you need to create a new users (and add them to the group), this can be done with the useradd command like so:
sudo useradd -g sftponly -s /bin/false -m -d /home/USERNAME USERNAME
Where USERNAME is the name of the user to be added.
The above command will ensure the user is unable to log in via SSH, as it assigns /bin/false as the user’s shell. Once you add a new user, make sure to set a password with the command:
sudo passwd USERNAME
Where USERNAME is the name of the user just added.
If you already have users you want to add to the group, you can do so with the command:
sudo usermod -aG sftponly -s /bin/false USERNAME
Where USERNAME is the user to be added and their shell will be changed. Do note, however, if the user does require SSH login, they won’t be able to do this once you make that change. If that’s the case, consider creating a new user specifically for their SFTP needs.
The user’s home directory permissions must now be changed. To do this, issue the following commands:
sudo chown root: /home/USERNAME
sudo chmod 755 /home/USERNAME
With the user’s directories now owned by root, they won’t be able to create files and/or directories. To get around that (so they can upload and download files), create new subdirectories (within their home directory) that they will have access to with the following commands:
sudo mkdir /home/USERNAME/{ftp_up,ftp_down}
sudo chmod 755 /home/USERNAME/{ftp_up,ftp_down}
sudo chown USERNAME:sftponly /home/USERNAME/{ftp_up,ftp_down}
Note: You can name the ftp_up and ftp_down anything you like.
Configuring SSH
Now we need to configure SSH. Issue the command:
sudo nano /etc/ssh/sshd_config
In that file, look for the line:
Subsystem sftp /usr/lib/openssh/sftp-server
Change that line to:
Subsystem sftp internal-sftp
Scroll to the bottom of the file and add the following:
Match Group sftponly
ChrootDirectory %h
ForceCommand internal-sftp
AllowTcpForwarding no
X11Forwarding no
Save and close the file. Restart the SSH daemon with the command:
sudo systemctl restart sshd
Testing
Now we can actually test our new setup. Log in with one of the newly created users (or an existing user) with the command:
sftp USERNAME@SERVER_IP
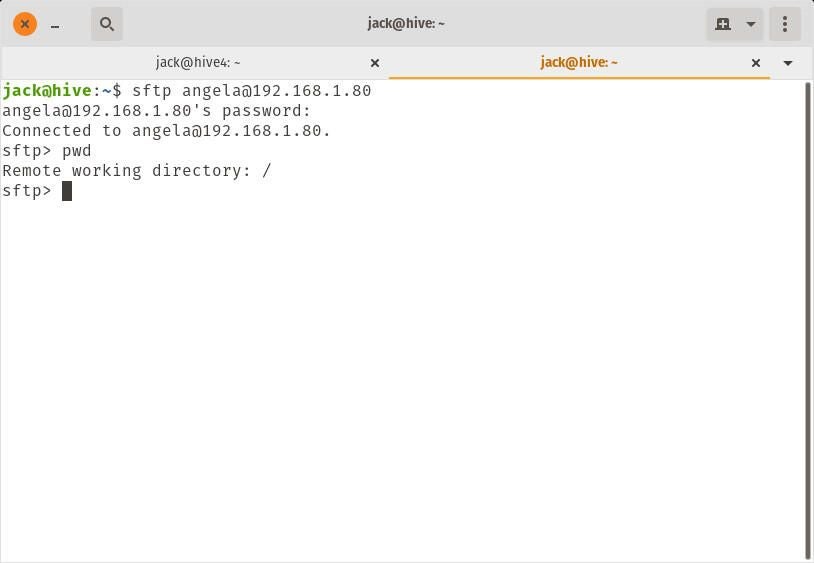
Where USERNAME is the username and SERVER_IP is the IP address of the hosting server. Once you’ve successfully authenticated, issue the command pwd to check the current working directory. It should report / (Figure A) and will not allow that user to access anything outside of that directory.
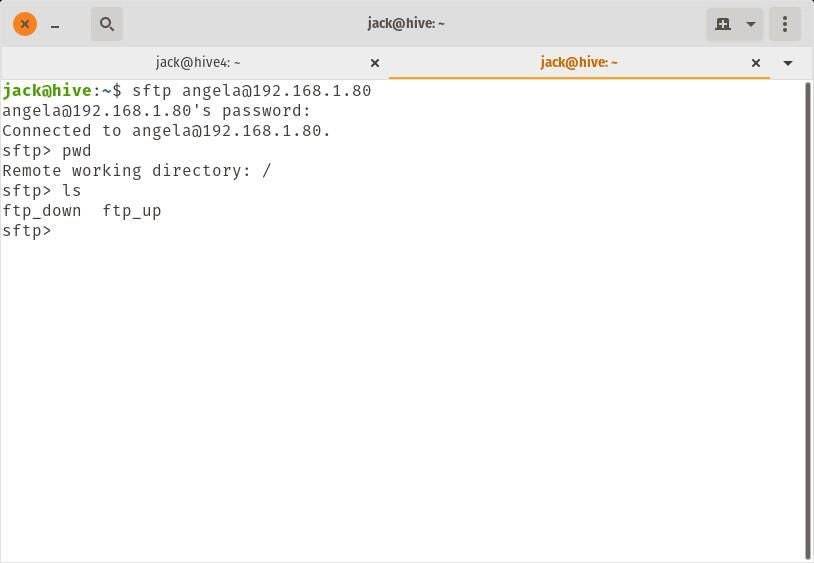
Next, issue the command ls to see the newly created directories the user is allowed to access (Figure B).
And that’s all there is to it. You now have an SFTP setup that enables users to only access specific directories. Make sure to lock down every user who needs to work with SFTP on that server, and you’ll be good to go.