You are what you browse. And chances are, advertisers know more than you realize about your digital hygiene. “Sometimes advertisers have your identity, but they really don’t need to know who you are in order to precision target you with advertising,” said the Electronic Frontier Foundation’s (EFF) William Budington. “Chances are your digital fingerprint is distinct.”
Ever shop for an item on Amazon then notice advertisements for related products on Instagram? Has a television ad popped up in Facebook? Most consumers are aware that browsing habits are used for programmatic advertising, Budington said, but most people are unaware how unique they are on the web. Through your browser alone, even in private browsing mode, web trackers can learn about your browser, your native screen resolution, your operating system, and the hardware powering your machine.
SEE: Cybersecurity in 2017: A roundup of predictions (Tech Pro Research)
“Advertisers can hit you with the right product at the right time on the right platform because your fingerprint stands out like a sore thumb,” Budington chuckled, “no pun intended.”
Budington manages and helped develop an EFF tool called Panopticlick, which checks web browser security for ad blocking, invisible tracker blocking, 3rd party trackers, and fingerprinting identifiers.
Web trackers present an even larger potential security threat to companies because sensitive browser data can unintentionally stream out to countless unknown entities. The 2017 Black Report, a white paper produced by security firm Nuix, found that the current average corporate data breach response time is between 250 and 300 days, and that a majority of hackers were able to infiltrate systems and exfiltrate data in under 24 hours.
SEE: How risk analytics can help your organization plug security holes (Tech Pro Research)
Many hackers work quickly, Budington said, because they do their homework and research the granular details of corporate systems. “Learning the details about corporate tech can enable easier phishing and social engineering attacks,” he said. Additionally, because corporate data is aggregated and sold on the Dark Web it’s possible that employee fingerprint data is more accessible to hackers than individual IT departments.
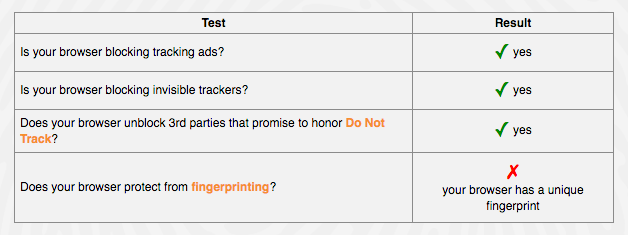
In addition to the EFF tool, Budington recommends installing Ghostery, a plugin that identifies all active trackers running on a page, and Privacy Badger, a plugin that allows end users and IT departments to customize browsing sharing preferences. In a series of tests without privacy software, Panopticlick was able to extract unique fingerprinting and some personally identifiable data, like my Google account identifier and the hash of canvas from my web browser. With proper security settings enabled, some fingerprinting data was present but limited.
SEE: New World Hackers group claims responsibility for internet disruption (CBS News)
Some personally identifiable information may be available to advertisers and web trackers using SilverPush, an emerging technology that connects television and streaming video advertising with mobile devices using an audio beacon. Applications with SilverPush enabled can connect mobile and PC identifiers, then relay mobile device data back to an advertiser. Despite FCC pushback Budington expects SilverPush-like technologies to be omnipresent on mobile apps by 2017. “Most people have no idea their mobile phone could be sending data to advertisers when it’s in their pocket and not in use,” he said.
SEE: Electronic data retention policy (Tech Pro Research)
Business users in particular should use apps like Panopticlick regularly to stay on top of powerful new monitoring software like SilverPush. “Panopticlick raises awareness about tracking technologies end users might not be aware of,” Budington said. “Privacy should be the default. [Privacy] should be the standard.”
Read more
- Video interview: Why your company should invest in cybersecurity infrastructure (TechRepublic)
- Why top ISPs don’t think your web history or app usage is ‘sensitive information’ (TechRepublic)
- The Black Report: Attacking your system, from the hacker perspective (TechRepublic)
- Experts predict 2017’s biggest cybersecurity threats (TechRepublic)
- Poll: What new cybersecurity trends will dominate 2017? (TechRepublic)
- 2017 cybercrime trends: Expect a fresh wave of ransomware and IoT hacks (TechRepublic)
- Gallery: The 10 biggest business hacks of 2016 (TechRepublic)
- Interview with a hacker: Gh0s7, leader of Shad0wS3c (TechRepublic)
- Five essential cybersecurity audiobooks (TechRepublic)
- Five essential cybersecurity podcasts for IT professionals (TechRepublic)
- Cyberwar: The smart person’s guide (TechRepublic)
- How to safely access and navigate the Dark Web (TechRepublic)
- IT Security in the Snowden Era (ZDNet)
- Russia’s role in political hacks: What’s the debate? (CNET)