Can you spot a scam? (screenshots)
Image 1 of 12
ntA theft of names and email addresses like the recent one from marketing firm Epsilon doesn’t sound that bad but that information is valuable for scammers to use in further attacks, notably in phishing scams.
n
ntIf an attacker knows your name, the companies you deal with and your email, then it can craft some convincing emails that have a much better chance of fooling you.
n
ntZDNet Australia’s Darren Pauli presents some fabricated examples of phishing emails to illustrate what users need to watch out for in order to protect themselves.
n
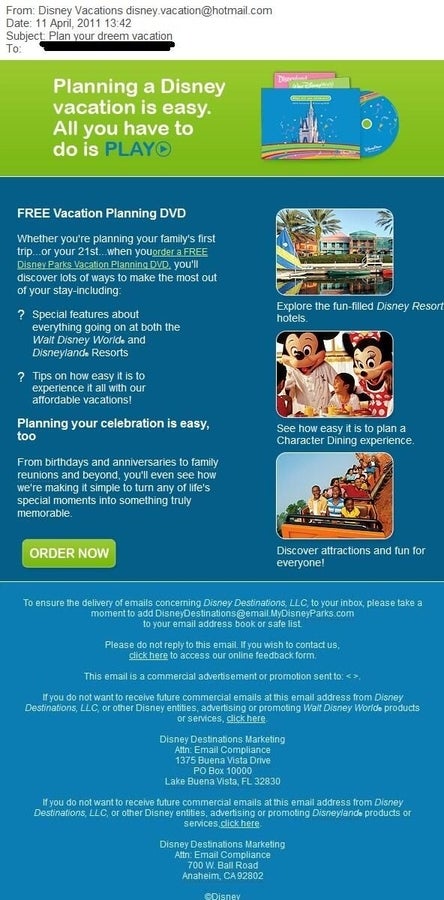
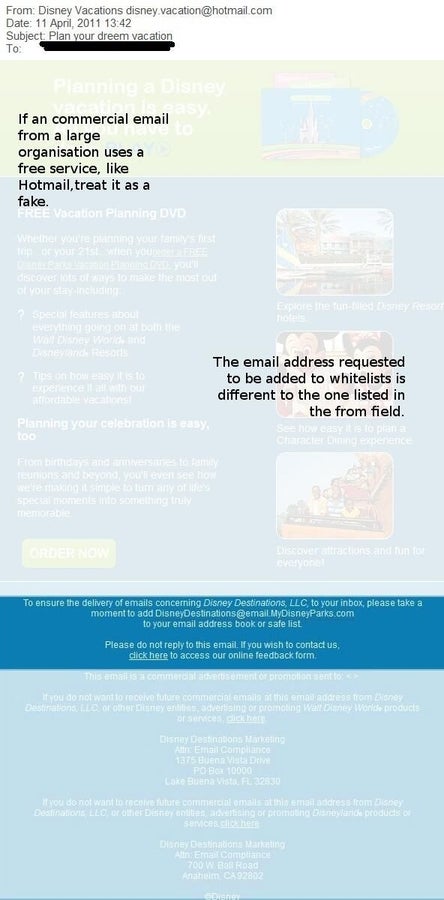
ntThe first one from Disney has mass appeal. The broad list of victims could be attractive for scammers.
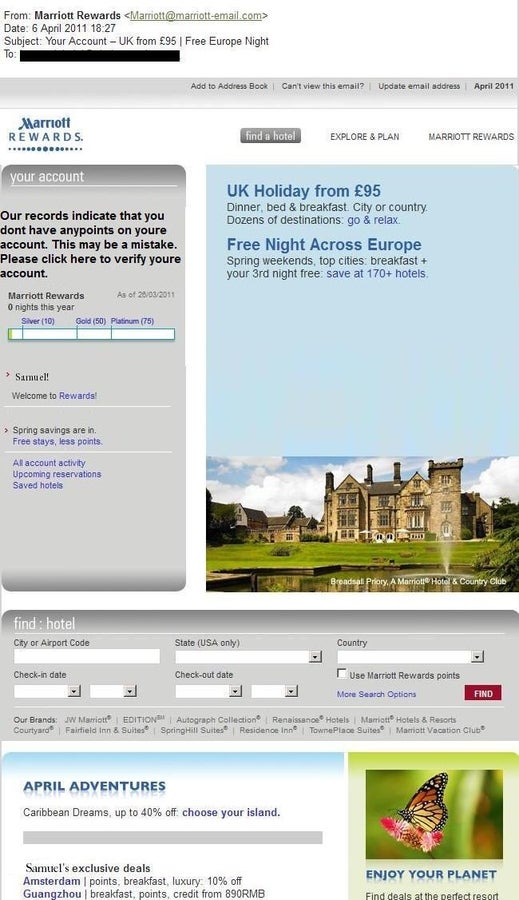
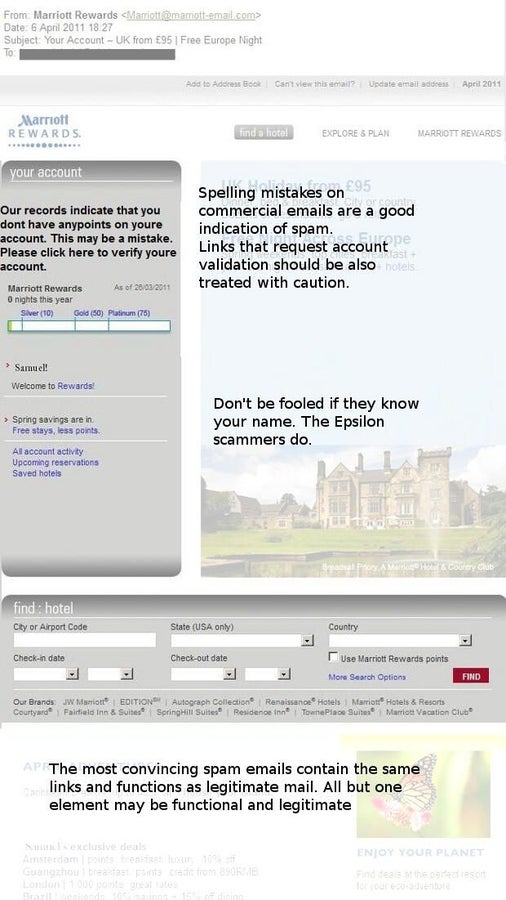
ntPeople love a good deal, and these exist in abundance for hotel chains like the Marriott.
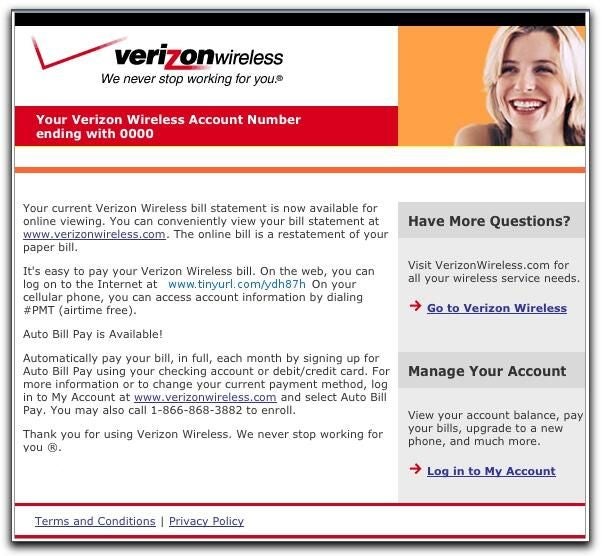
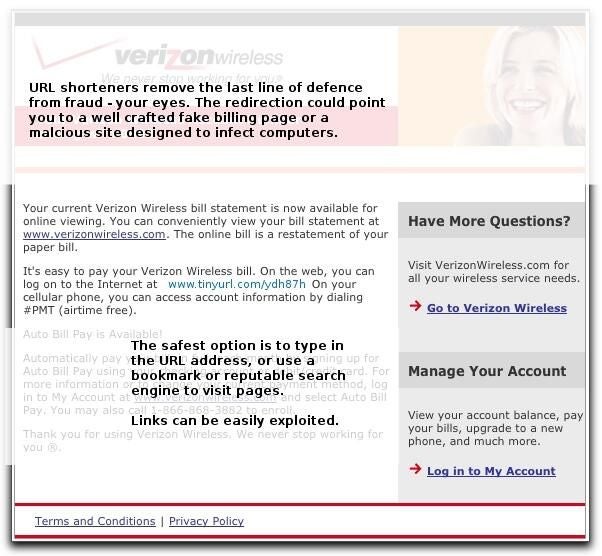
ntTelcos like Verizon have millions of customers.
ntA link could be inserted that points to a fake web page where customers are requested to enter billing information and promptly scammed.
ntPeople love a good deal, and these exist in abundance for hotel chains like the Marriott.
ntPhishing scams like this could direct users to fake booking sites in order to swipe financial details.
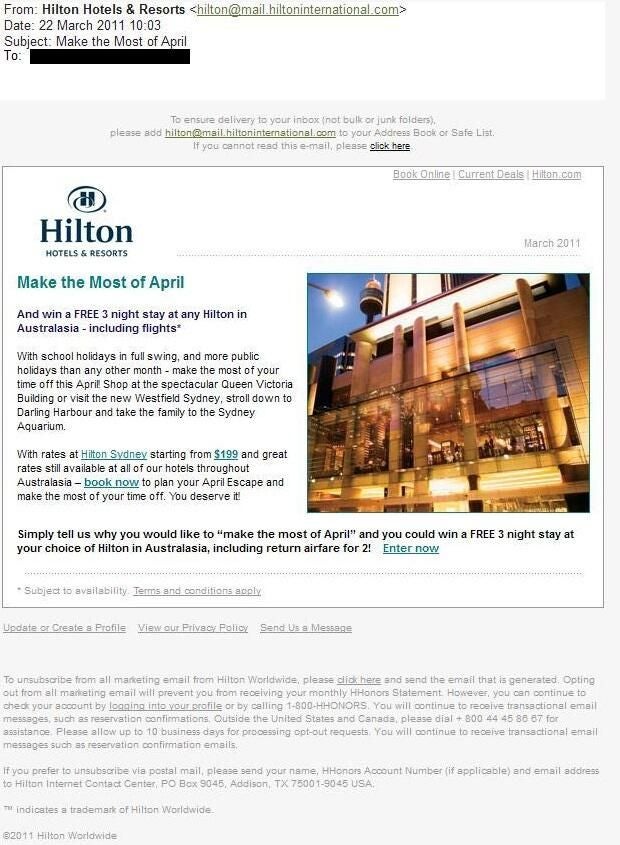
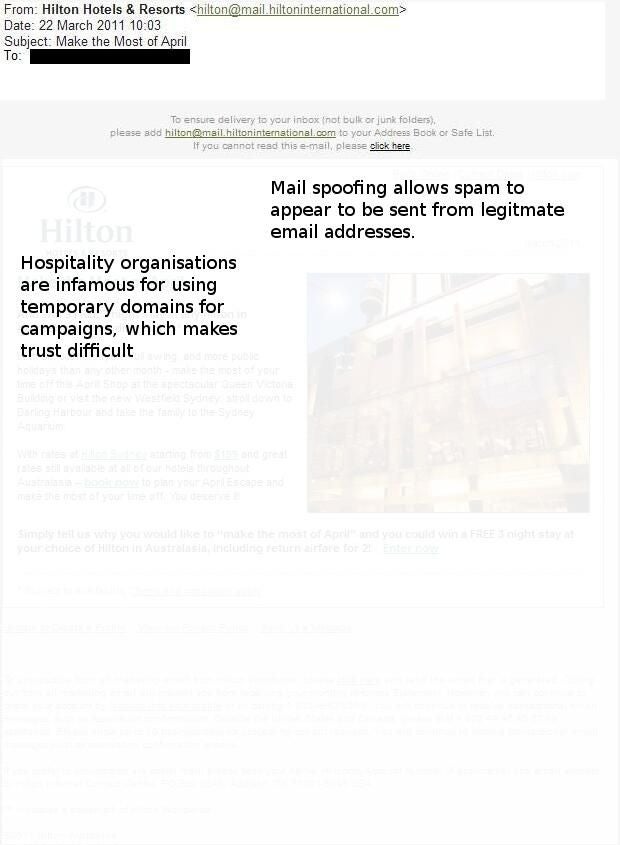
ntThe Hilton is another popular and trusted name in accommodation.
ntUnfortunately, its popularity is what could make it a good target. Even legitimate-looking email addresses will not necessarily be kosher.
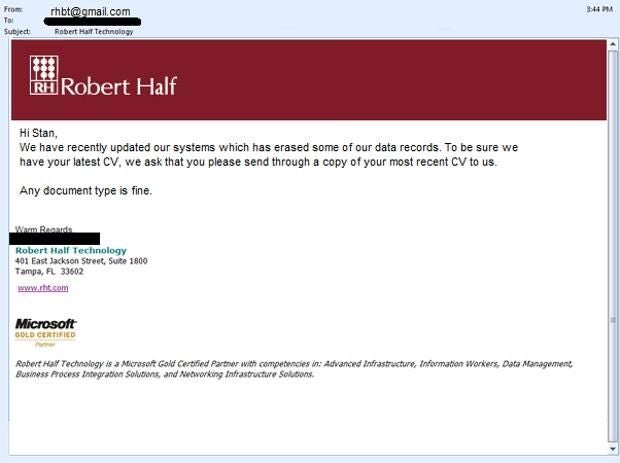
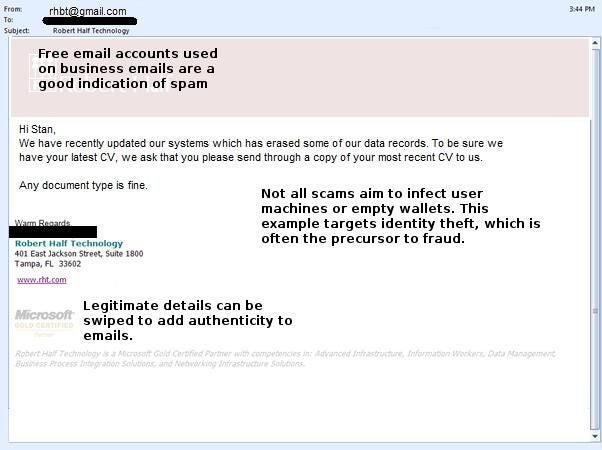
ntRecruitment and career agency Robert Half was another victim of the Epsilon breach.
ntCustomers should be wary of scams that seek to harvest details for identity crime.
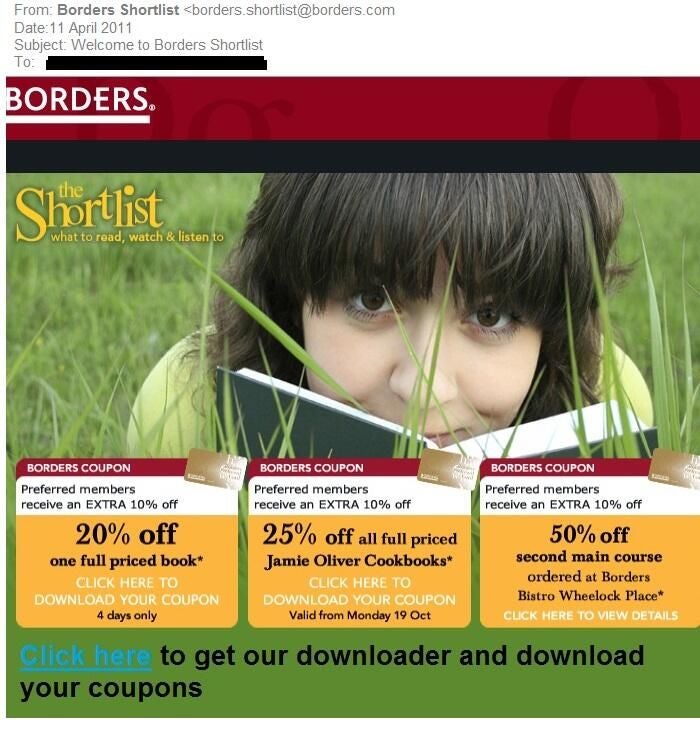
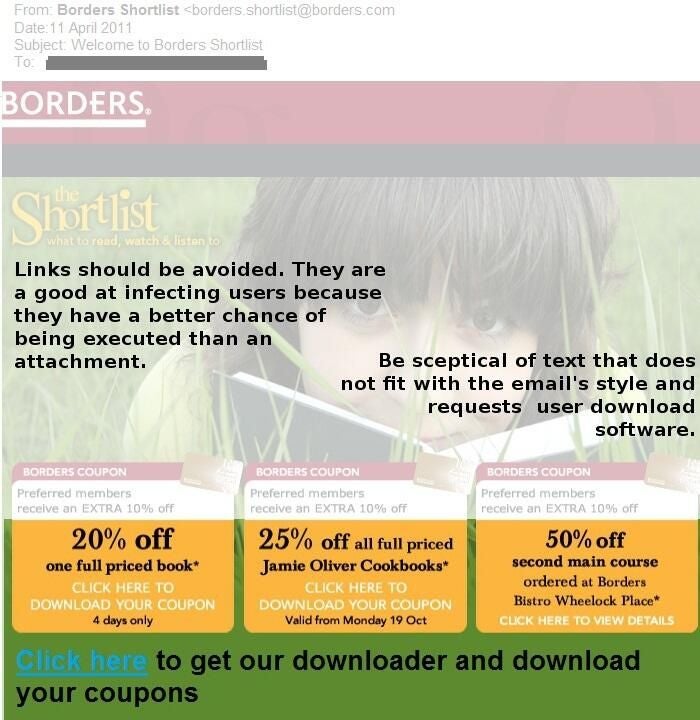
ntBorders sends out coupon offers to readers.
ntA link could be inserted that points to a fake web page where customers are requested to enter billing information and promptly scammed.
-
Account Information
Contact Sonja Thompson
- |
- See all of Sonja's content