Five free encryption apps to help secure your Android device
Image 1 of 7


Introduction
Introduction
Do your hats tend to fall into the tinfoil range? Are yournafraid there is always somebody watching you? If so, rest assured that thernAndroid ecosystem offers plenty of apps to soothe your paranoia. But which appsrnare the must-haves? Here are five apps you should immediately install and putrnto work. They’ll bring you peace in the knowledge that your mobile data is farrnmore secure than those around you.
Note:rnThis gallery is also available as an article.
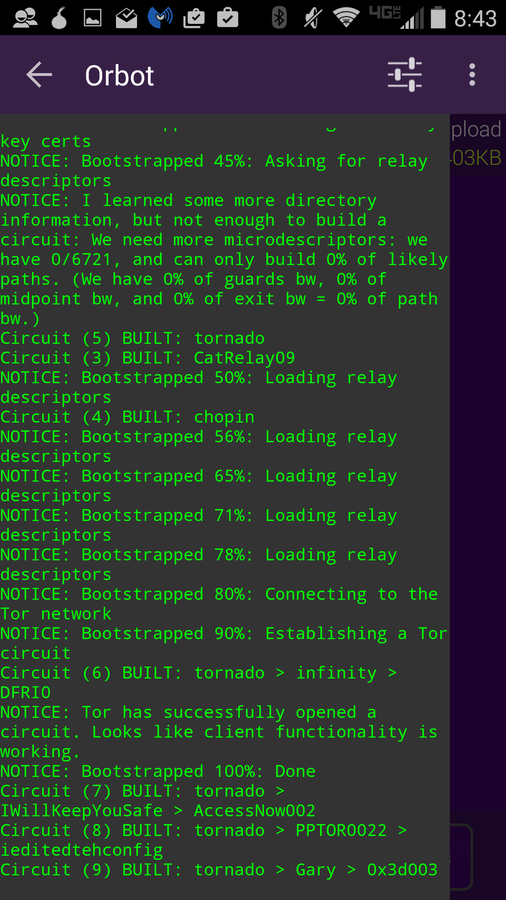
Orbot Proxy with Tor
To use Tor on Android, your best bet is Orbot Proxy withrnTor. Once you have it installed and connected, it will encrypt all internetrntraffic leaving your device. This is the onlyrnapp that produces a truly secure and encrypted connection for your Androidrndevice. If you are really paranoid, you need Orbot Proxy with Tor. It’s free…rnwhat do you have to lose?
CSipSimple
CSipSimple lets you do encrypted SIP callingrnvia your Android device. It’s open source and free, and it offers an easy-to-usernWizard for setting up the app. You are required to have an account on a SIPrnserver, and I highly recommend using Ostel. It works seamlessly and has its own wizard for setting up the SIP accountrnwithin CSipSimple. Even the Ostel account is free—so the only cost associatedrnwith this will be any data usage from your provider.
CSipSimple
You can set up CSipSimple to only usernWi-Fi, to avoid any charges whatsoever. CSipSimple uses rewrite/filtering rulesrnto integrate with Android and allows you to record calls.
ChatSecure
With ChatSecure, setting up an OTR session is simple. Whenrnyou start a chat with someone, you can first verify the contact and then startrnthe encryption. This app isn’t perfect. You might run into instances where thernencryption won’t start or the connection with Orbot isn’t made. But shouldrneither happen, you can restart the app and try again. It doesn’t occur often,rnbut when you’re dealing with the need for 100% security, you don’t want to usernthe app without the aid of Tor.
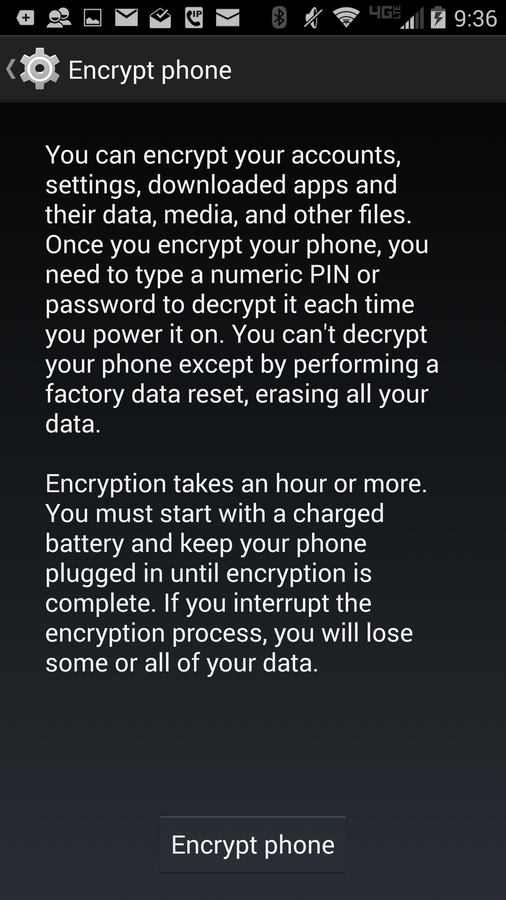
Built-in device encryption
This option is for those who want to ensure the privacy ofrntheir device should it fall into the wrong hands. This built-in encryptionrnsystem works with all data—including app data, downloaded files… everything on yourrndevice.
Built-in device encryption
This level of security does come with its drawbacks. First, older (or lower-end) devices might see a hit on thernperformance. (Newer and flagship devices shouldn’t so much as hiccup withrnsystem-wide encryption.) Second, you’ll have to enter the encryption passwordrnon every startup of the device—but that’s a small price to pay for this levelrnof security. Pay it and be safe. Also understand that once you’ve encryptedrnyour Android device, the only way to disable the encryption is to do a factoryrnreset. Note: Android Lollipop defaults to device encryption.
-
-
Account Information
Contact Jack Wallen
- |
- See all of Jack's content