How to configure ACS 5.2 for 802.1x authentication on a Cisco switch
Image 1 of 17
Log in to ACS
ntTo log in to the ACS server (I’m assuming its already running on the network) you can browse to the IP address or name of the server.
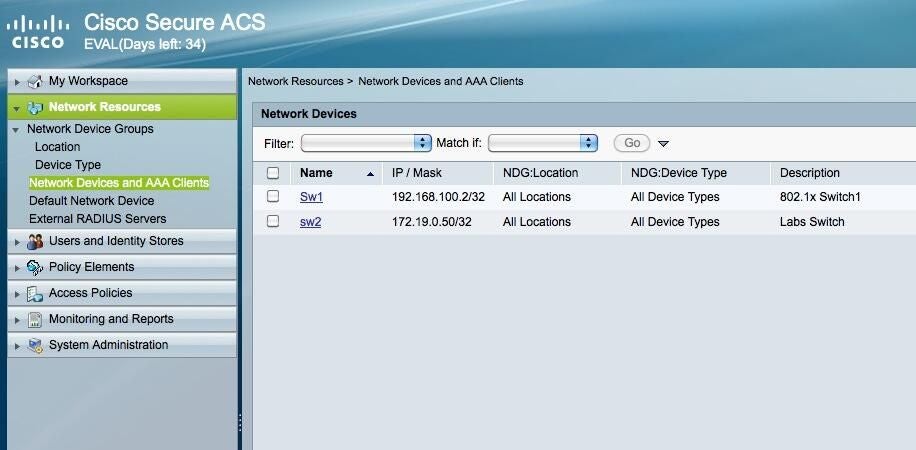

Navigate to Network Resources | Network Devices and AAA Clients
Navigate to Network Resources | Network Devices and AAA Clients
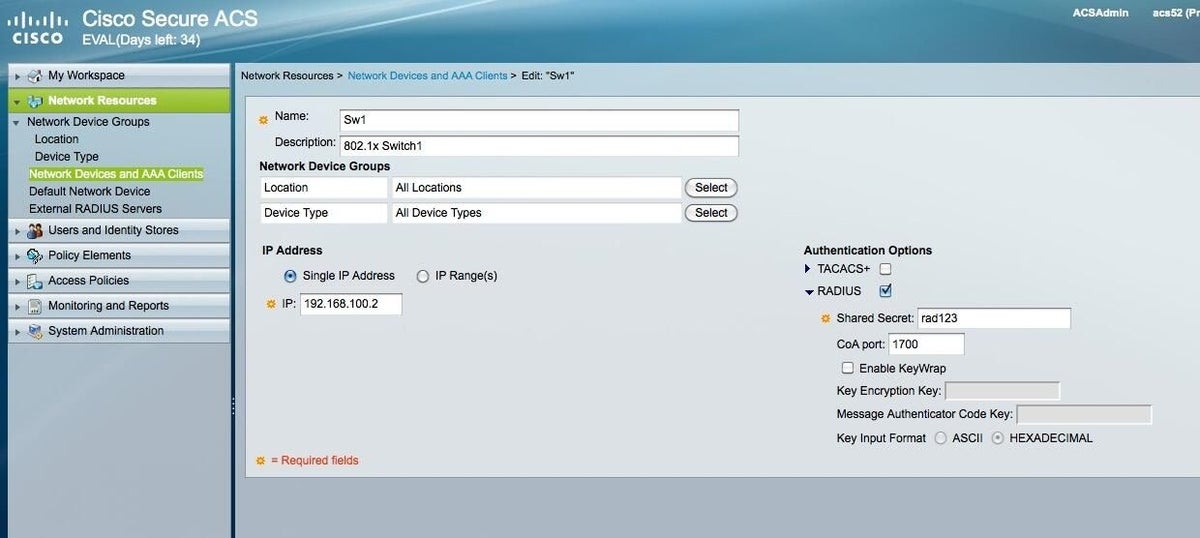

Select the switch you are working with
Select the switch you are working with
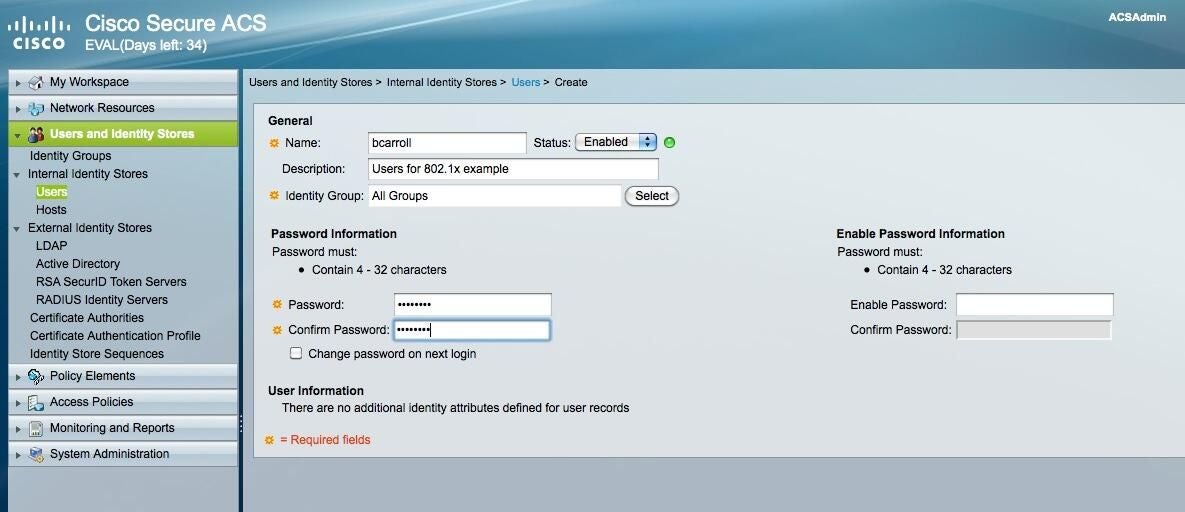
Add a user
ntBrowse to Users and Identity Stores | Internal Identity Stores |Users.
n
ntOnce there, click the Create button on the bottom and add your users. I’ve added a user with the name bcarroll.
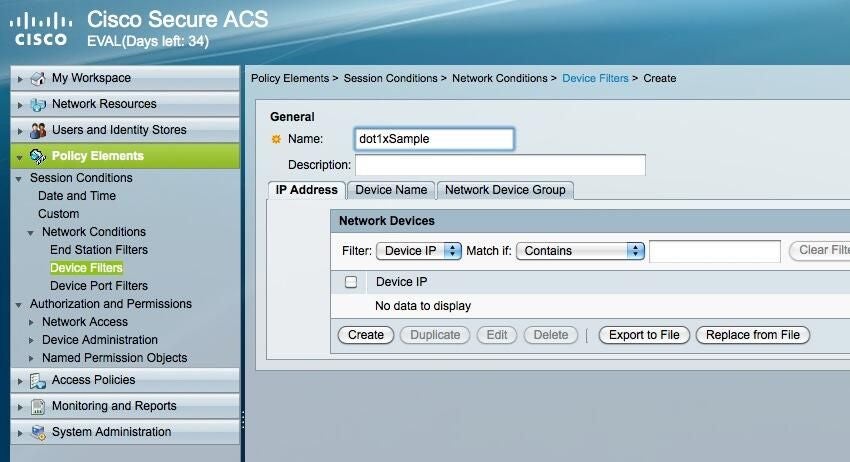
Create a device filter
ntNavigate to Policy Elements | Session Conditions | Network Conditions | Device Filtersand click Create.
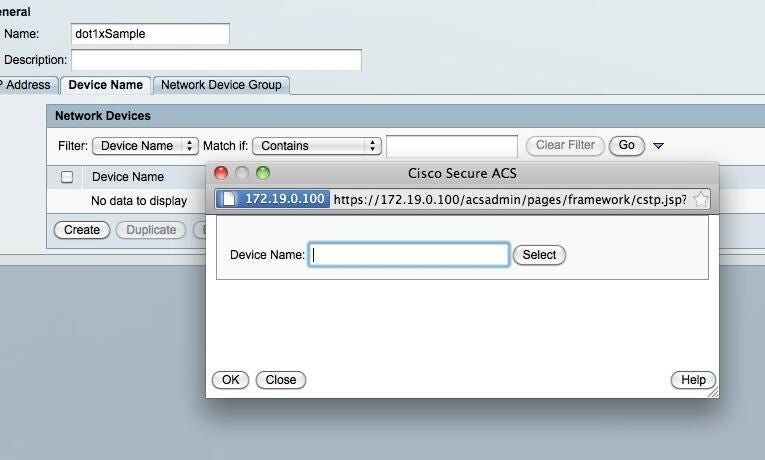
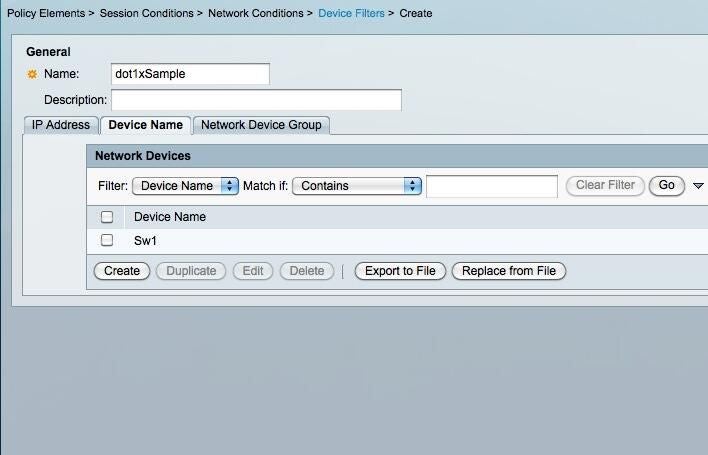
Add the Device Name
ntNow add the device name by selecting the Device Name tab and again clicking Create. This part can cause some issues. If you are not allowing pop-ups it may appear that nothing happens. In my case, I had to switch from a Safari browser to a Firefox browser.
n
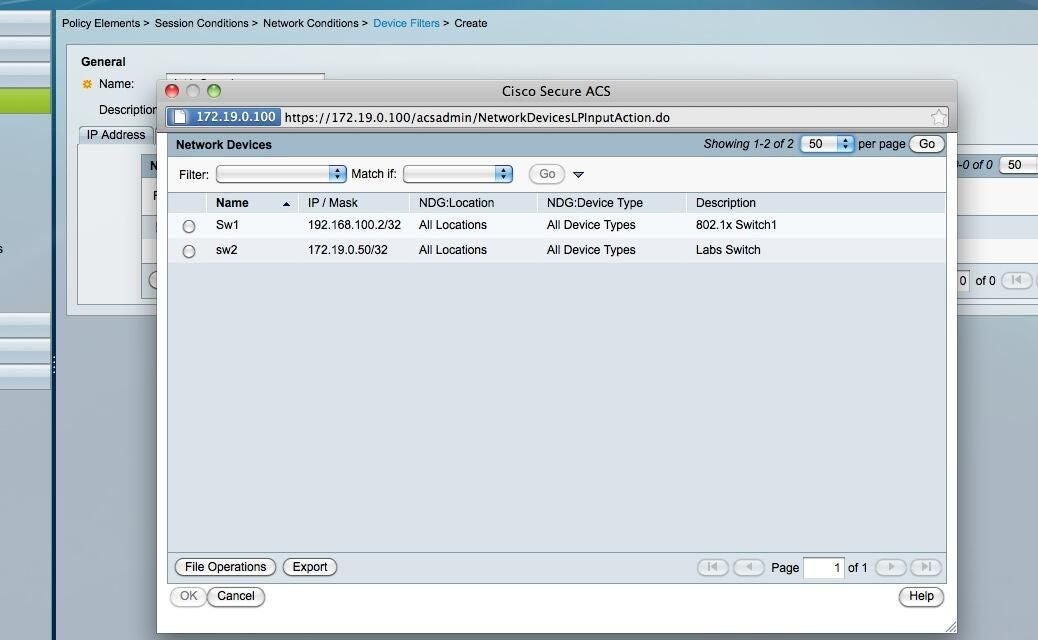
ntOnce the pop-up appears you will see an empty form box to add the device to. You can’t type in the box, rather you click the Select button and select the device from the list.
Select the device
Switch is now added to list
ntOnce your switch is selected you will click ok a few times until you get back to the main ACS page and the switch is reflected in the list.
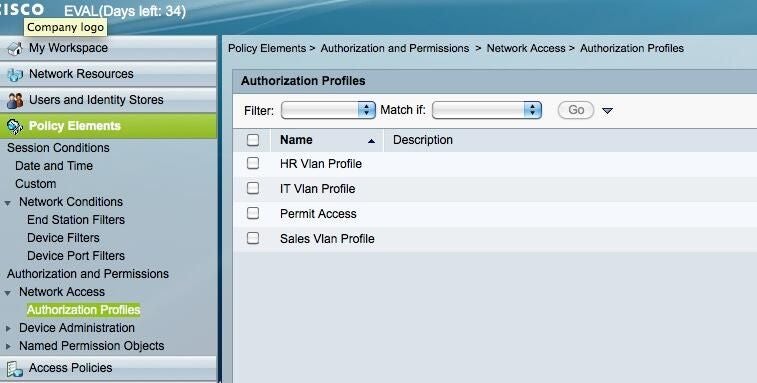

Create authorization profiles by department
Create authorization profiles by department
ntBrowse to Policy Elements | Authorization and Permissions | Network Access | Authorization Profiles.
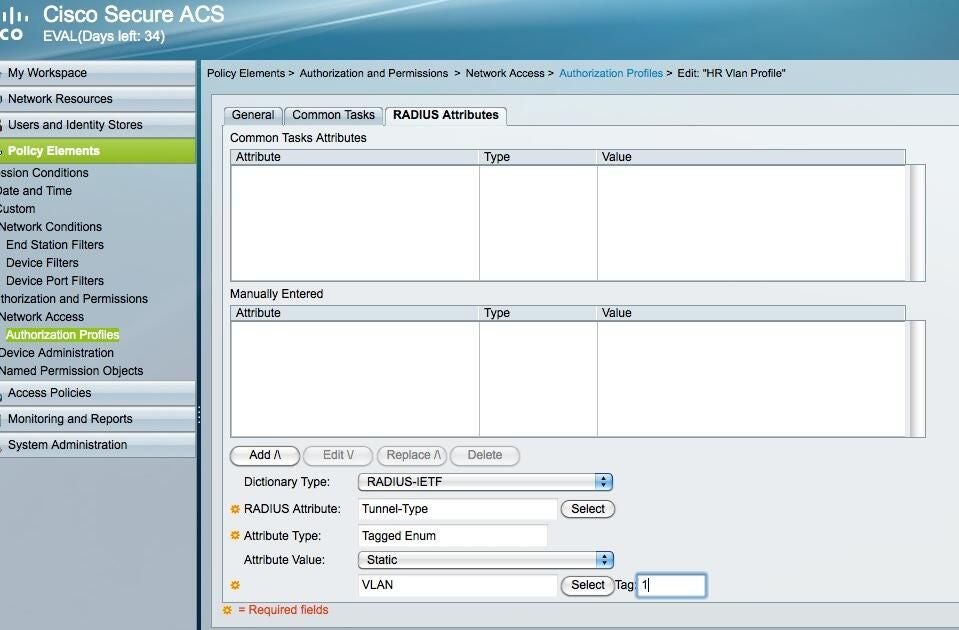

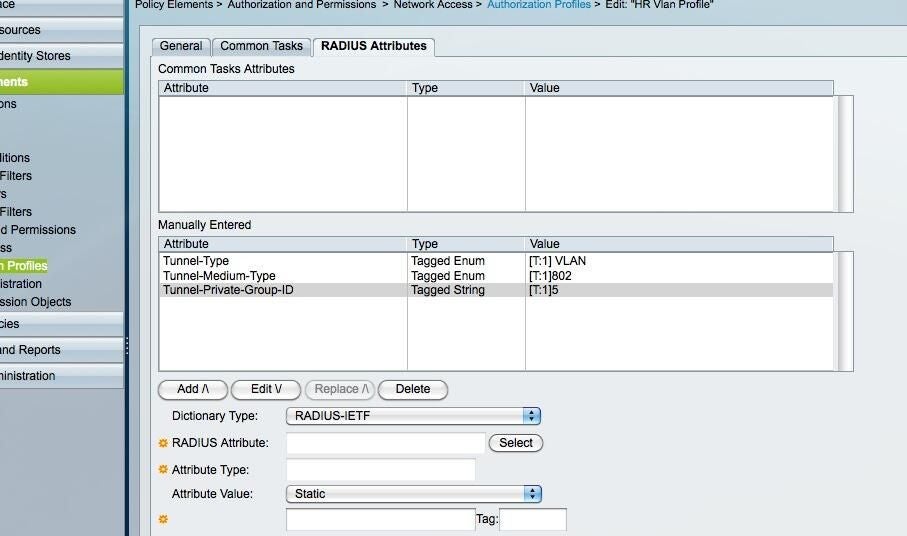
Authorization profile page for HR Vlan
Authorization profile page for HR Vlan
Define profile attributes
ntIn the example, I’ve defined a few attributes for HR, specifically:
n
- nt
- nttTunnel-Type
- nttTunnel-Medium-Type
- nttTunnel-Private-Group-ID
nt
nt
n
n
ntYou have to define attributes for each profile separately.
Create an Access Service
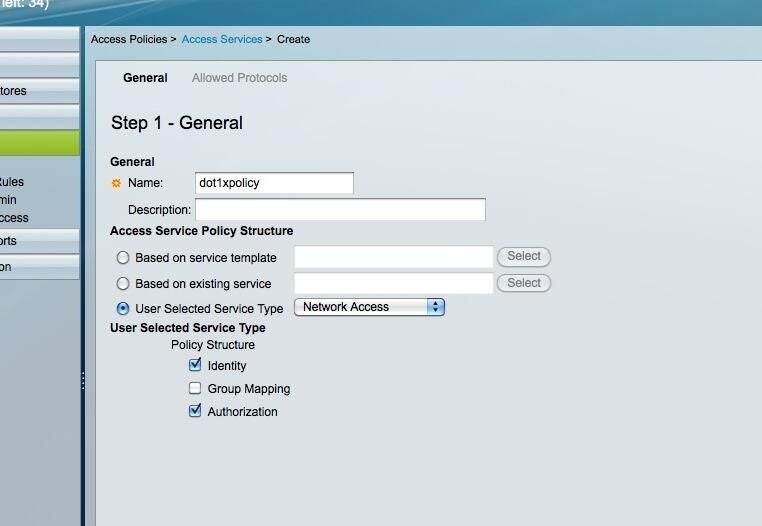
ntNavigate to Access Policies | Access Services. I’ve done a User Selected Service Type of Network Access and left the default selections of Identity and Authorization. At the bottom of the page, click Next.
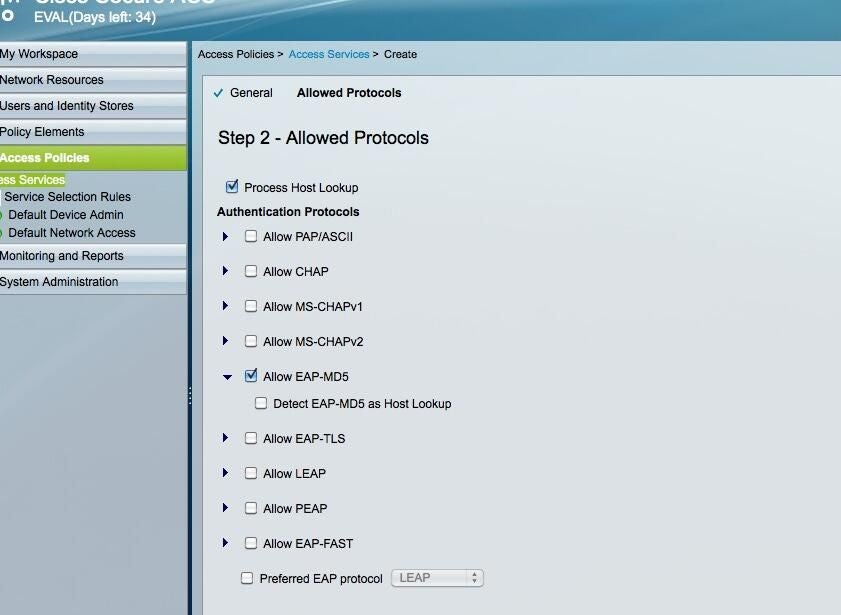
Allowed Protocols
ntThis is where you select the protocol you want to use., I am going to use EAP-MD5. Once you select your protocol, click Finish.
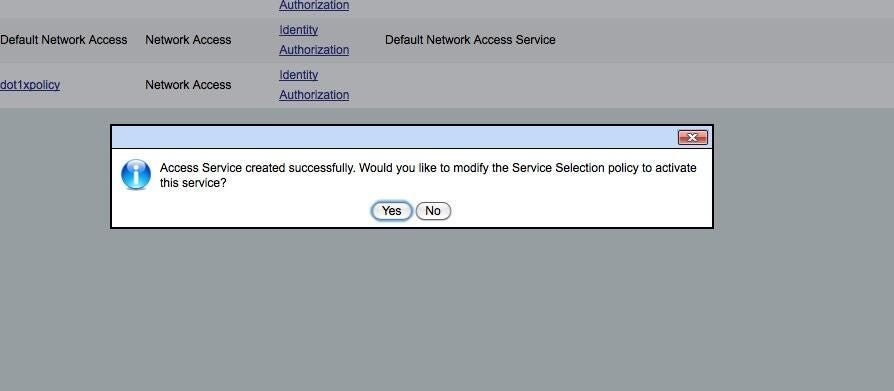
Confirm Service Selection
ntNext, you should see a pop-up asking if you want to modify the Service Selection policy to activate the server. You want to answer Yes here. This will then take you to the rules page.
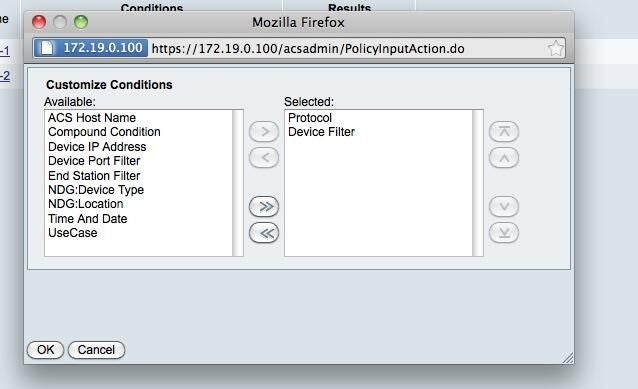
Customize Rules
ntOn the Rules page click Customize and add Device Filter to the right hand menu. If it’s not there, you will not see it as a condition.
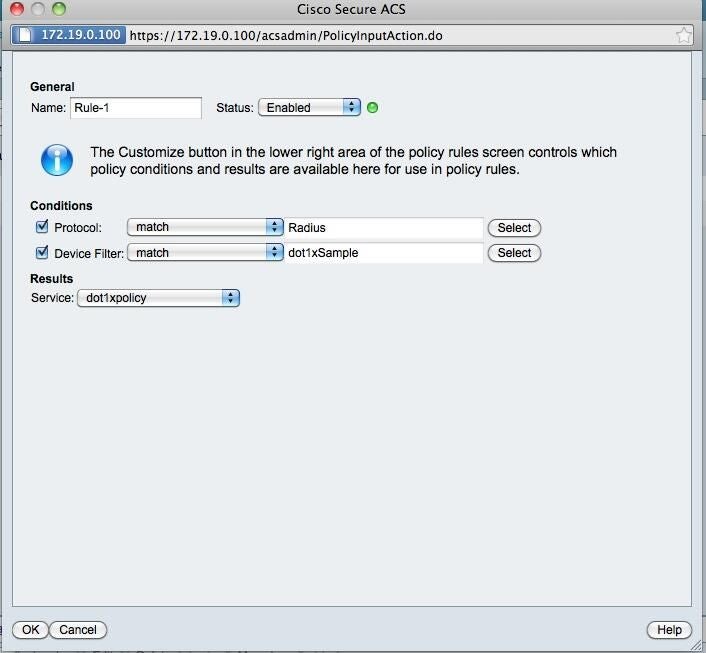
View Conditions for rule
ntAnd now when you add or modify Rule-1, you should see the conditions. You’re now done on ACS.
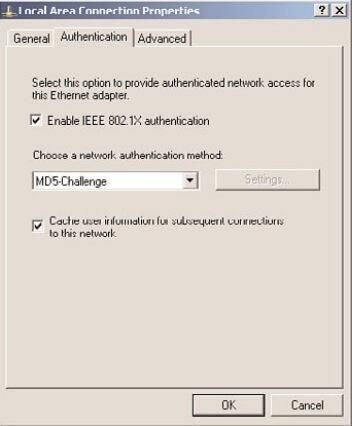

Edit Windows adapter for MD5 Challenge
Edit Windows adapter for MD5 Challenge
ntFinally edit your Windows adapter to enable 802.1x authentication and select MD5 Challenge. You’ll get a little balloon window to authenticate the next time you connect that host to the port configured for 802.1x.
-
Account Information
Contact brandoncarroll
- |
- See all of brandoncarroll's content