Images: ReadNotify’s tracking service
Image 1 of 4
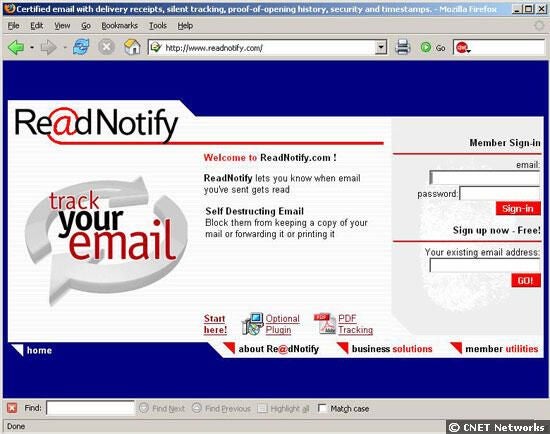
During congressional hearings, Hewlett-Packard investigator Fred Adler specified how the company bugged the e-mail it sent to CNET News.com reporter Dawn Kawamoto. HP used the services of rnReadNotify.com, one of several online companies that let people plant bugs in e-mail messages and files. This is a screenshot of the rnReadNotify home page.
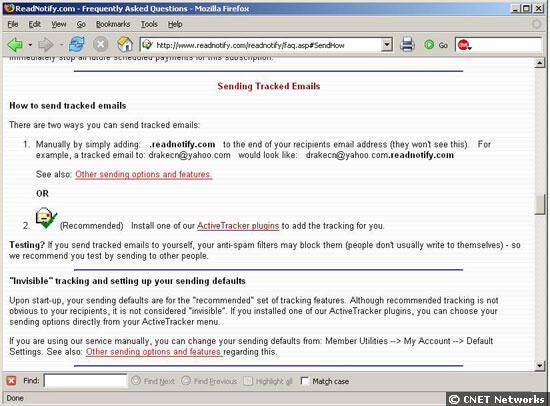
This is a screenshot of the ReadNotify page that instructs users how to send a bugged e-mail. Users of the service register their e-mail rnaddresses with ReadNotify and then simply append “.readnotify.com” to any e-mail address they send mail to if they wish the message to be rntracked. Recipients won’t see this, but could tell from the e-mail headers that the message was relayed.rn
rnReadNotify also offers plug-ins for various e-mail clients, including Web-based e-mail, to make bugging a message easier.
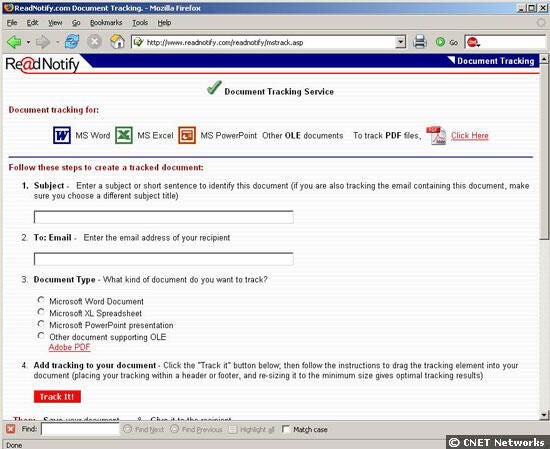
Paying users of ReadNotify.com get the ability to add bugs to files, such as Office and PDF documents. This is a screenshot of the ReadNotify rnWeb page that will generate a document with an image. This image, a green check mark, can simply be dragged-and-dropped into the document rnthat needs to be traced. The check mark becomes transparent after it is dropped.
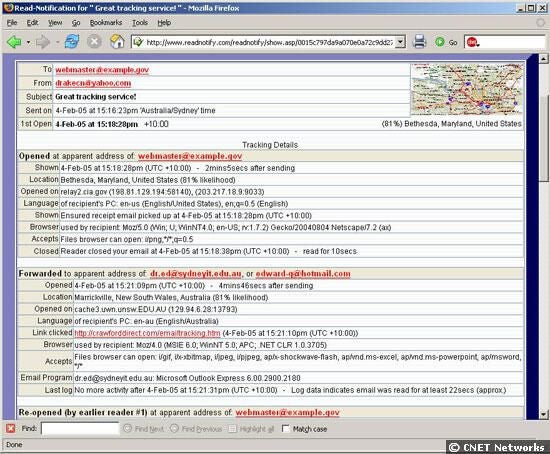
ReadNotify.com offers a detailed report of what happens with tracked e-mail messages or documents. The report includes details on rnwhen, where, on what type of PC, and for how long the traced information was viewed. It even includes a small map of where the individual who rnopened the mail or file is likely located, based on the Internet Protocol address of the computer.rn
rnAdditionally, if a message is forwarded, the report states the probable e-mail address of the individual it was sent on to. It also displays if a message is reopened by anyone.

-
-
Account Information
Contact Bill Detwiler
- |
- See all of Bill's content