
Security
SecurityHow to Go Passwordless with NordPass Passkeys
With passkeys, you no longer need to use a password to log into supported websites. Here's how to use them with password manager NordPass.
You're on page 49, See the latest articles on Security.

With passkeys, you no longer need to use a password to log into supported websites. Here's how to use them with password manager NordPass.
Learn about the features available with iOS 16 and how to download and install the latest version of Apple's mobile operating system.
AI-powered personalization rescues you from unwanted calls and texts, providing protection and stopping spam calls and texts waste your time.

Data from the human vs. machine challenge could provide a framework for government and enterprise policies around generative AI.

At the Google Next '23 conference, the company announced a slew of AI-powered cybersecurity solutions for the cloud, featuring Duet AI, Mandiant and Chronicle Security Operations.

A new study found that 4.31% of phishing attacks mimicked Microsoft, far ahead of the second most-spoofed brand PayPal.

Data from ChatGPT Enterprise will not be used to train the popular chatbot. Plus, admins can manage access.

The Cisco Talos report exposes new malware used by the group to target Internet backbone infrastructure and healthcare organizations in the U.K. and the U.S.

A new variant of malware called XLoader is targeting macOS users. XLoader’s execution, functionalities and distribution are detailed.

This QR code phishing campaign is targeting multiple industries and using legitimate services such as Microsoft Bing to increase its efficiency and bypass security.

Google announced security enhancements to Google Workspace focused on enhancing threat defense controls with Google AI.
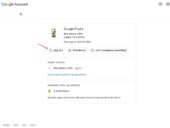
Follow this guide to learn how to easily remove any device from your Google account and keep your account secure.

A new study by Critical Insight shows that cybersecurity attacks in the health care sector are hitting more individuals and finding vulnerabilities in third-party partners.

Cybersecurity expert Kayne McGladrey speaks about why AI cannot do what creative people can, and the important role of generative AI in SOCs.

Explore enterprise applications and infrastructure, AI, tools for the remote workforce, machine learning, and more from VMware Explore 2023.