
Managing client devices remotely on a network is the Holy Grail of just about any system administrator. Given the reliance on technology, the number of systems being managed is expanding more than ever–meaning IT professionals have their work cut out for them.
But having many clients shouldn’t mean that you (or your staff) need to physically place a hand on devices anytime an issue presents itself. After all, isn’t the ability to deploy fixes from the command line an age-old IT superpower? With PowerShell and modern versions of Windows, this special bit of magic is baked right in.
SEE: 10 PowerShell commands to make remote management easier
Just follow the steps below to enable and configure this level of access using Microsoft’s Group Policy Management Console. But first, there are a few requirements to touch upon:
- Server running Windows Server 2008 R2 or later
- Active Directory Domain Services
- Group Policy
- Client computers running Windows 7 or later joined to the domain
- Administrative credentials
1: Enable Windows Remote Management
Launch the Group Policy Management Console (GPMC) and navigate to the following path: Computer Policies | Administrative Templates | Windows Components | Windows Remote Management (RM) | WinRM Service. Then, double-click Allow Remote Server Management Through WinRM Policy (Figure A).
Figure A
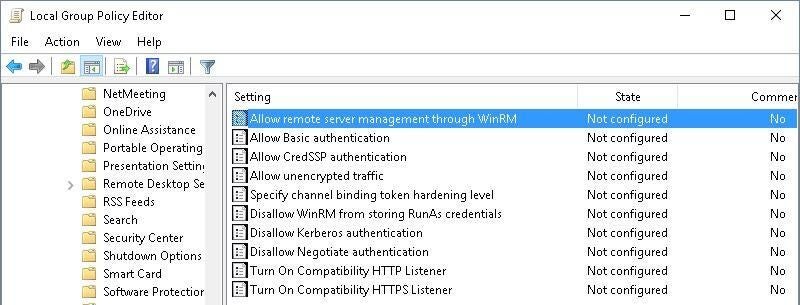
Select the radio button next to Enabled and place the “*” for each line in the text box next to IPv4 and IPv6. Now click OK to save the settings (Figure B).
Figure B

Note: WinRM will be set to allow connections from any IPv4/IPv6 addresses when using the “*”. However, if you wish to secure access to a specific IP address or IP range, enter that in the textbox instead to lockdown the WinRM environment.
2: Configure Windows Firewall Settings
While still in GPMC, navigate to the following path: Computer Policies |Windows Settings | Security Settings | Windows Firewall with Advanced Security (Figure C).
Figure C
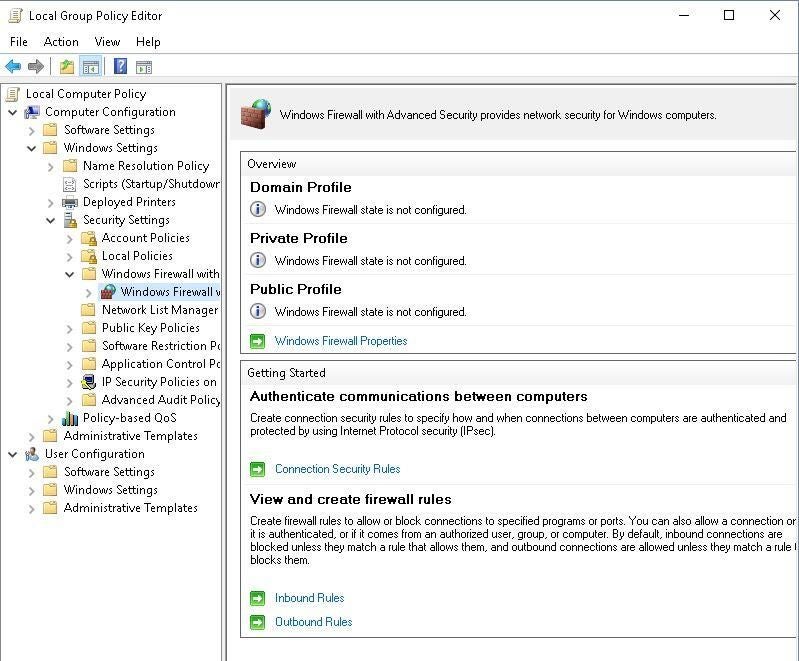
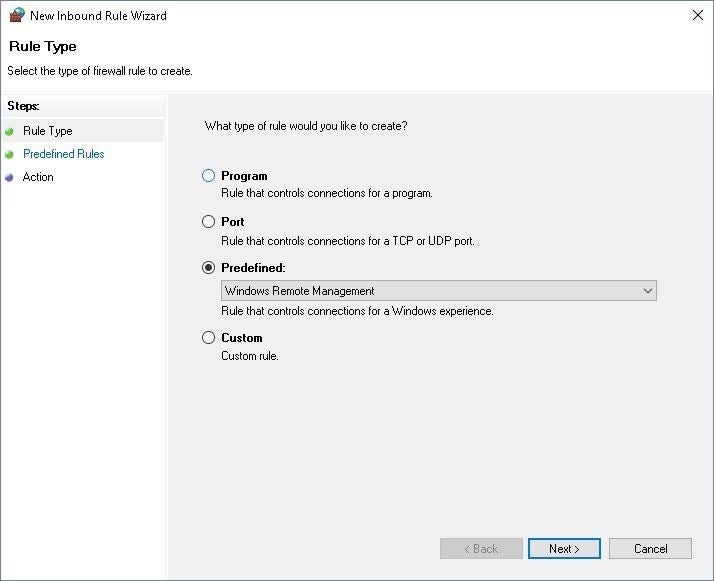
Expand the selection and right-click Incoming Connections, New Rule. The New Inbound Rule Wizard will appear. Select the radio button next to Predefined and from the drop-down menu, select Windows Remote Management. Click Next to continue (Figure D).
Figure D
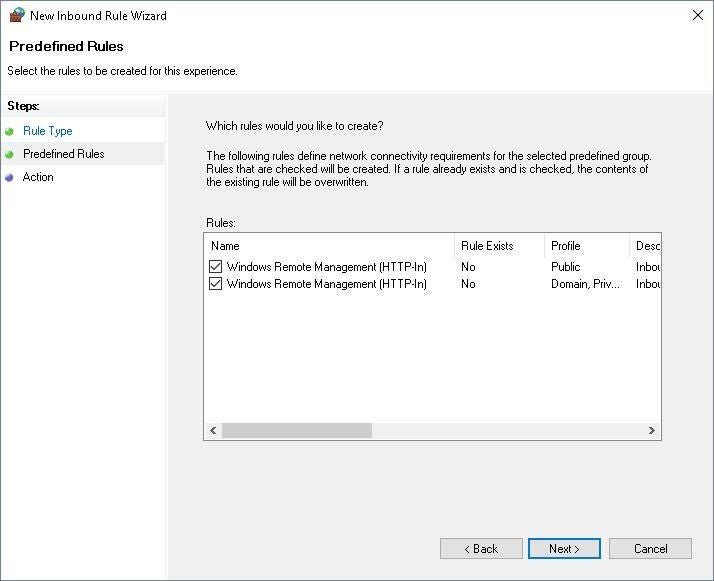
Two predefined rules will be displayed on this screen (Figure E). Click Next to proceed.
Figure E
Select the Allow The Connection option and click Finish to complete the configuration (Figure F).
Figure F

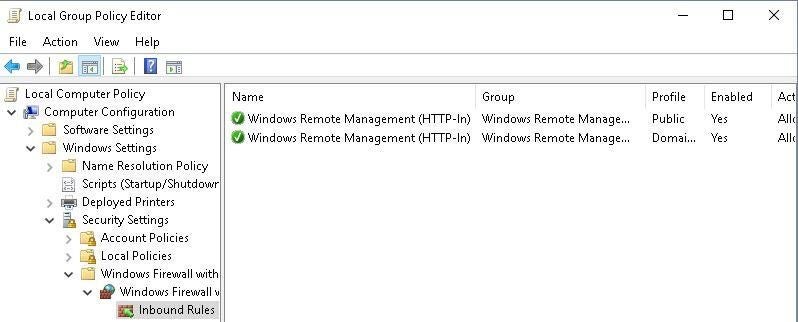
The two inbound rules should be successfully configured and displayed in GPMC (Figure G).
Figure G
3: Configure Windows Remote Service
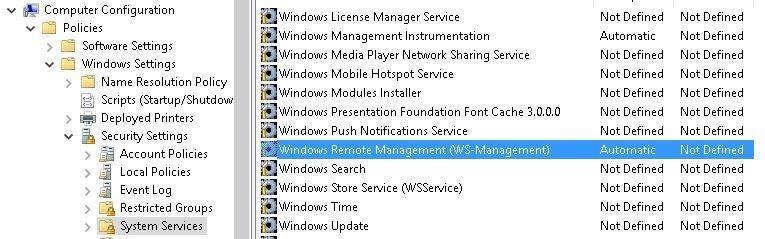
The last step in the configuration phase also occurs in GPMC. Navigate to the following path: Computer Policies |Windows Settings | Security Settings | System Services (Figure H).
Figure H
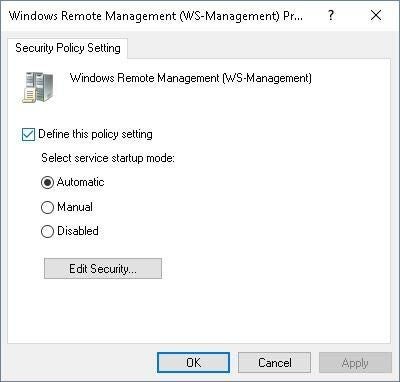
Double-click the Windows Remote Management (WS-Management) service to configure the properties. In the new window that opens, select Automatic under Select Service Startup Mode and check the Define This Policy Setting option (Figure I).
Figure I
Navigate to the following path: Computer Policies | Preferences | Control Panel Settings | Services. Right-click it and select New | Service (Figure J). Under the General Tab, select No Change from the drop-down menu next to Startup. Enter WinRM in the text box next to the Service Name and select Start Service from the drop-down menu next to Service action (Figure K).
Figure J

Figure K

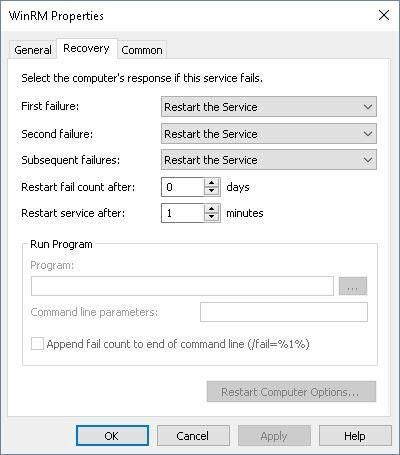
Under the Recovery Tab, select Restart The Service from the drop-down menu next to the First, Second, and Subsequent Failures sections, then click OK to save the settings changes (Figure L).
Figure L
With the protocol, service, and firewall settings configured within Group Policy, all devices that are set to inherit the policy from the parent Organizational Unit (OU) will receive the policy changes upon the next refresh cycle after replication has completed.
You now have everything in place to execute PowerShell cmdlets from an administrative station to connect to and run cmdlets on any computers remotely. Microsoft TechNet is a great source for info on the PSSession cmdlets and their syntax.
Also read…
- Microsoft open sources PowerShell; brings it to Linux and Mac OS X (ZDNet)
- Windows 10 update breaks PowerShell and Microsoft won’t fix it until next week (ZDNet)
- How to use PowerShell modules to knock out your admin chores (TechRepublic)
- How to automate account pre-staging in WDS with PowerShell (TechRepublic)
Your take
Do you do a lot of remote support? What tricks and technologies make your job easier? Share your recommendations and experiences with fellow TechRepublic members.