If you have Linux servers in your data center or they’re being hosted on a cloud server (such as AWS, Google Cloud, or Azure), you cannot assume, simply because of the operating system you’ve deployed, they are secure. Even though Linux is one of the most secure operating systems on the market, it’s not perfect. In fact, there has been a rise of attacks on the platform, which will continue to trend upwards as Linux gains even more popularity.
What do you do?
When you suspect one of your servers might be under attack, you need to check on it. But how? In this piece I’m going to show you a few commands that can help you discern if your server is being hit by a denial of service (DoS) attack, which comes from a single IP address and attempts to cripple a website to render its server inaccessible. There’s another form of this attack, the distributed denial of service (DDoS), which comes from multiple sources.
Let’s find out how to tell if your Linux server is a target of a DoS attack.
SEE: Identity theft protection policy (TechRepublic Premium)
What you’ll need
The only things you’ll need for this is an instance of Linux and a user with sudo privileges. I’ll be demonstrating on Ubuntu Server 20.04.
How to install netstat
We’re going to be using the netstat tool to find out what IP addresses are currently connected to your server. To install netstat on Ubuntu, you actually install net-tools, like so:
sudo apt-get install net-tools -y
If you’re using CentOS or a Red Hat-based installation, netstat should already be installed.
How to check your server load
The first thing we’re going to do is check our server load. The command we’ll use for this will return the number of logical processors (threads). On a server, this number should be fairly low, but it depends on what you have running. You should make sure to run a baseline for this number, when you know everything is okay. If you suspect something is going on, run the thread check again and compare it.
To check for the number of logical processors, issue the command:
grep processor /proc/cpuinfo | wc -l
If that number is significantly higher than your baseline, you might have a problem.
For instance, on my Pop!_OS desktop, I have 16 threads, but on a Ubuntu Server hosting Nextcloud, I only have two. If either of those numbers were to double, I might be under a DDoS attack.
How to check your network load
We next want to check our network load. There are a number of tools you can do this with, but I choose nload. To install nload, issue the command:
sudo apt-get install nload -y
On CentOS that command would be:
sudo dnf install nload -y
To run the tool, simply issue the command:
nload
You should see a fairly normal incoming and outgoing network load (Figure A).
Figure A
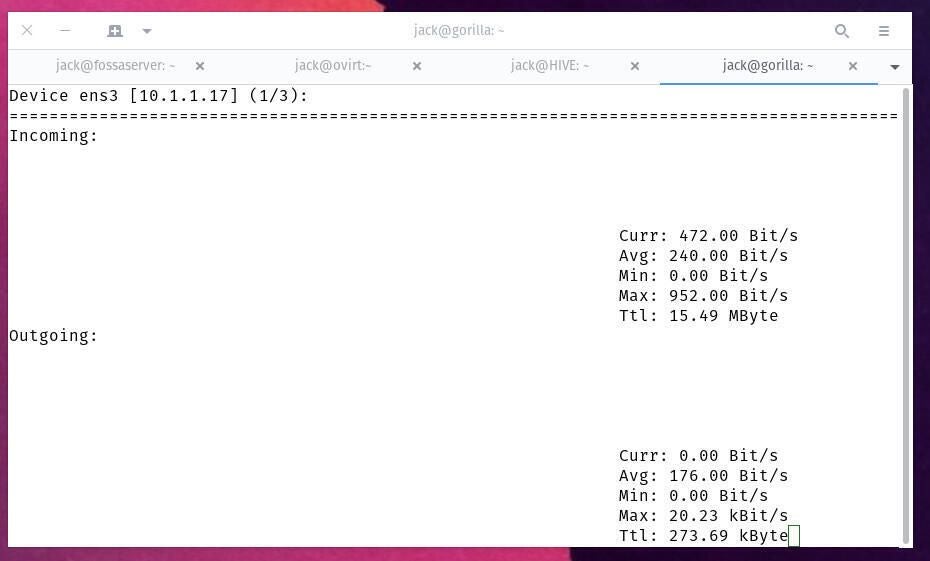
If that load is considerably higher than you believe it should be, you might be under attack.
How to find out what IP addresses are connected to your server
The next thing you’ll want to do is find out what IP addresses are connected to your server. For this, we’ll use netstat like so:
netstat -ntu|awk '{print $5}'|cut -d: -f1 -s|sort|uniq -c|sort -nk1 -r
The output of the above command will list out each IP address that is connected to the server and how many instances from each. As you can see, I have two IP addresses connecting to my server (one three times) (Figure B).
Figure B
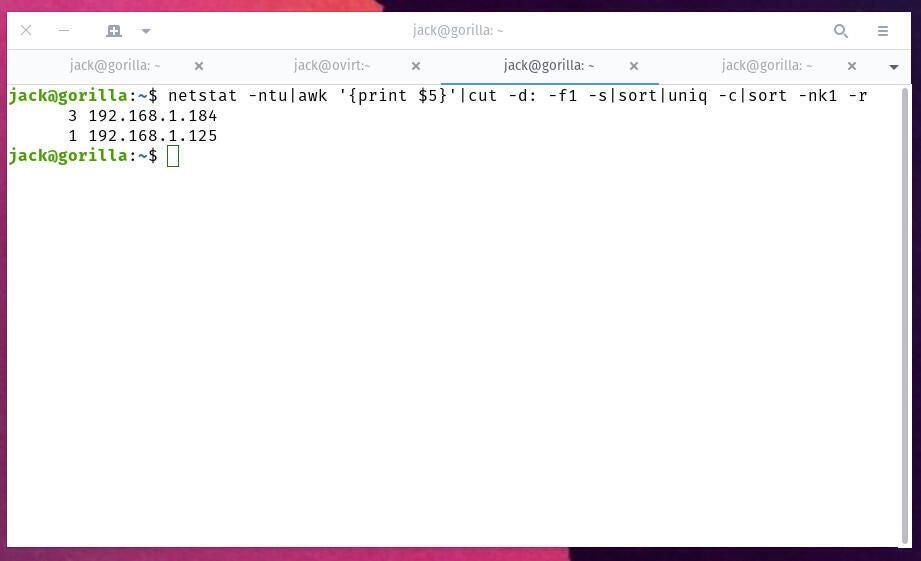
Make sure to look through this listing carefully. If you see an IP address with a large number of instances (over 100), the likelihood is pretty high that address is your culprit. Once you’re sure of the culprit, you can ban the IP address with the command:
sudo route add ADDRESS reject
Where ADDRESS is the IP address of the suspect.
At this point, go back and recheck your threads, connected IP addresses, and network loads to see if you’ve mitigated that DoS attack. If so, it’s time to report the suspected IP address and probably ban it from your network altogether. Next time around, I’ll walk you through the process of mitigating a DDoS attack.
Subscribe to TechRepublic’s How To Make Tech Work on YouTube for all the latest tech advice for business pros from Jack Wallen.

Image: Jack Wallen